What do firewalls, intrusion detection systems (IDSs), virtual private networks (VPNs), and network traffic encryption and authentication have in common?
They are network security measures designed to protect the enterprise’s perimeter from external attacks.
What they do not do is protect an organisation from vulnerabilities from within like poorly designed business applications. As organisations accelerate migration of workloads to the cloud, CIOs and CISOs will need to work in tandem with the development team to enhance web application security.
Application vulnerabilities – the hardly-told story
Application vulnerabilities are more common than anyone is willing to admit. You know they are present because we receive frequent notifications about software patches to almost every device and application we use today.
Don’t believe me? Go check out the Common Vulnerabilities and Exposure (CVE) system for the latest in publicly known information security vulnerabilities and exposures. Should we worry? Yes and no. No, because ethical vendors are regularly updating the software we are using – we just have accept the updates when they become available (after some due diligence of course). Yes, because we can never tell if our vendors are really committed to our interest are they are just in for the money.
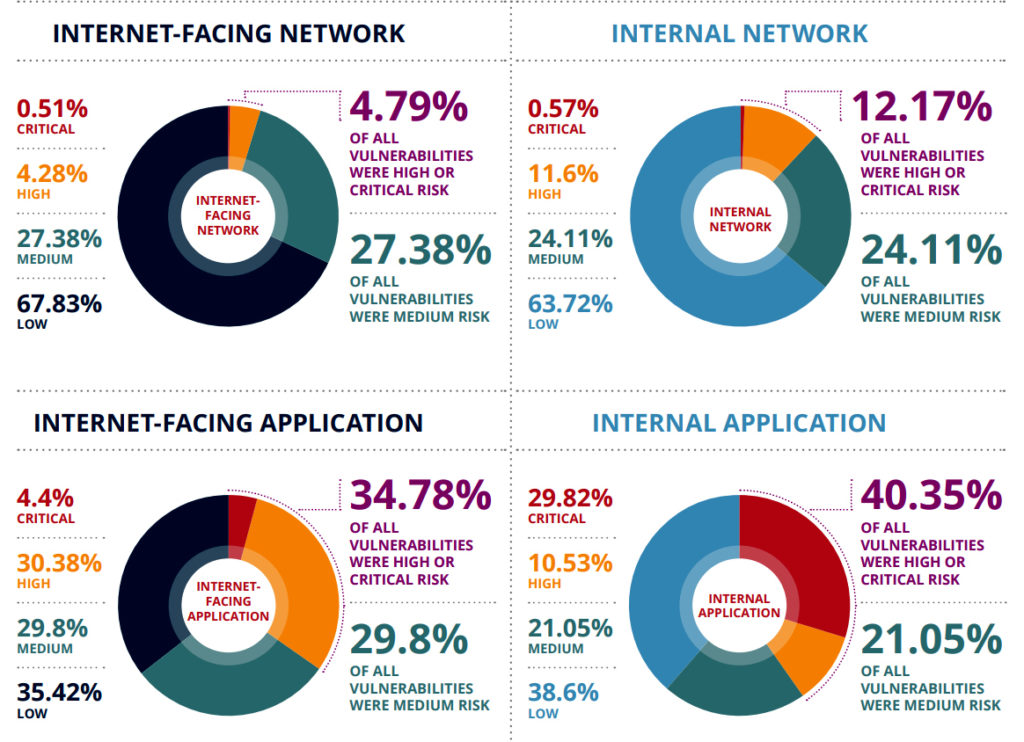
According to Edgescan’s 2020 Vulnerability Statistics Report, more than 40% of internal application vulnerabilities are considered a critical risk. It also found that over 34% of vulnerabilities in internet-facing applications are considered a critical risk.
2020’s migration to the cloud – double-edge sword
The cloud has been touted as bringing about the multiple benefits of scalability, flexibility, faster time-to-market, lower cost-to-market, and with the onslaught of COVID-19, productivity. The one area where confusion as regards to a cloud benefit is security. Whereas it is true that major cloud service providers including hyperscalers are likely more able to afford better security infrastructure and practices than most enterprises, security experts contend that accountability is restricted to uptime and the security of their infrastructure.
Mark Lukie, systems engineer manager for Barracuda Networks, noted that enterprises are ultimately responsible for what information they put in the cloud.
Enterprise applications security
Enterprises have many options today in terms of the applications that will power their business. In most cases, the application portfolio will include in-house developed applications, off-the-shelf suites that are either on-prem or served natively in the cloud, and applications served as-a-service (aka SaaS). More recently, the maturing understanding and use of application programming interface (APIs) have seen companies acquire licenses to use SaaS-based software tools that perform specific tasks (aka microservices). The justification for this latter approach is often labelled best-of-breed, or to facilitate rapid time-to-market via OEM software licensing.
According to Lukie, a lot of businesses are still using on-prem infrastructure. From a security standpoint therefore they are looking for solutions that are available (or consumable) as a service. Either they don’t have the security skills in-house to develop themselves or they want to avoid the heavy lifting that comes with building things yourself.
A worrying application insecurity trend
In a 2019 Forrester Research survey, 42% of organizations that had experienced an external attack blamed the incident on a software security flaw, and 35% said it had resulted from a buggy web application.
Lukie laments the sad state of organisations that are ‘putting their heads in the sand’ ignoring the security elements of their public-facing applications.
Some of these companies have not bothered to employ web application firewalls or have in place teams able to address security issues. In its Web Application Firewall 2020 report, Gartner predicts that by 2023, 30% of all web application will be protected by some sort of application security or API protection.
“That still leaves 70% of application exposed. That risk is still high if you ask me.”
“Anyone that has personally identifiable information, or key customer information that they are generating (in the cloud) really need to make sure they have good security posture around their applications,” he added.
API adoption – a security conundrum
Fifty-one percent of respondents to the 2020-2021 RapidAPI Developer Survey acknowledged that the API economy is a top priority for their organisation. This is evidenced by the 61.3% increase in their use of APIs compared to 2019. Just as interesting, 71% of developers plan to use even more APIs in 2021.
Lukie has expressed concern that the use of APIs may inadvertently increase the risk to organisations should attackers figure out how API frameworks present data. There is a lack of control when it comes to responding to API requests for data,
“For the toxic request coming into the API, the attackers have figured out how to steal information or inject stuff into those APIs. It is a new form of data and how they are writing codes. We need to make sure we’ve got good security around those API and how we are protecting it,” he elaborated.
Bots – the new attack vector
Software robots or bots have become popular among enterprises. Lukie said developers use bots to help QA (quality check) their applications, making sure that when they write good codes, these bots can basically be crawled and be used for goods, on their websites.
Unfortunately, bots can also be used for nefarious purpose. Bot development have matured to the point where these can be used to mimic human activities and thereby used to subvert legitimate processes.
The road ahead – beyond 2021
Lukie said the current remote work environment exposes both employees and companies. “I think a lot of the organizations need to think about that holistic approach, making sure they encapsulate their users with good training and awareness.”
“They need to make sure they have got good security solutions that not only protect their cloud environment, but also from a networking perspective,” he concluded.
Click on the PodChat player above to listen to the full dialogue with Lukie.
- According to Gartner Security, the application layer currently contains 90% of vulnerabilities. Any reason for such a high percentage?
- Do you see the migration to the public cloud making businesses any less secure than they already are?
- Who should own the responsibility of securing an organisation’s business applications, including those that are developed in-house, licensed from third-party, and acquired via an as-a-service model?
- We now have over 20 years of experience in the use of cloud computing, and more with developing applications for use in business. What are we doing wrong?
- The use of API to connect applications and businesses will continue. How should organisations enhance their security strategy without slowing their embrace of API and web applications?
- With greater use of bots, how should the CIO frame the company’s security strategy to minimise the risks?
- What is your advice to other members of the C-suite and even the Board as it relates to creating a more secure business environment in the digital era with COVID hanging around us?




