Editor’s note: This is an excerpt from a more extensive blog post by Miryam Meir on the topic. Click on the link to read the full blog post.
Digital transformation was well underway before the pandemic and to enable remote work and e-commerce, organizations have been adding new digital offerings at an unprecedented rate. Businesses are growing increasingly reliant on digital infrastructure with the expectation to secure a shifting cloud while managing a hybrid workforce and a growing IoT.
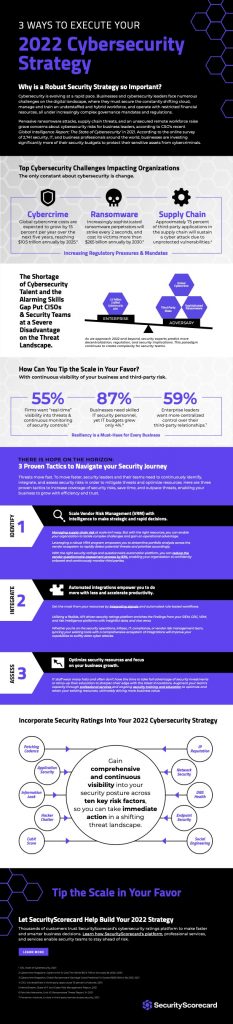
Transformation and a global pandemic have created a feeding frenzy for threat actors that are driving urgent governance mandates which have a reputation of introducing more complexity to an already complicated, understaffed, under-budgeted situation.
2021 experienced an increase in supply chain attacks, larger-scale data breaches, and a lack of sufficient talent. And with new regulatory and compliance mandates, the security concerns are far from over.
Today, security leaders face several challenges as they work to keep up with the pace of change in the cybersecurity space:
- Increasingly sophisticated and costly ransomware events
- Growing third-party and fourth-party supply chains
- Shifting cloud and IoT perimeter
- Shortage of cybersecurity talent in the industry.
As we approach 2022, analysts predict more decentralization, regulation, and security implications over the next few years. This paradigm continues to create complexity for security teams.
Despite progressive steps in automation, many teams are still manually gathering data from various point solutions and implementing third-party risk management (TPRM) functions through email and spreadsheets. Faced with an expanding attack surface, these methods won’t cut it, especially when you’re already spread thin.
Relying on time-consuming, inaccurate processes that do not scale to your entire ecosystem can lead to costly complications:
- According to the U.S. Treasury Department’s Financial Crimes Enforcement Network (FinCEN), the average ransomware payout increased 30% year-over-year bringing the average payout to just under $1M.
- Cyberedge reports that 86% of organizations suffered from a successful cyberattack last year and 69% of organizations were compromised by ransomware—both record numbers.
- 4th, 5th, and Nth party events are causing just as much damage as single-party events.
Threats move fast, and to move faster, security managers and their teams need to continuously identify, integrate, and assess security risks. That’s why we’re excited to bring you our Q4 2021 featured release, so you can accelerate risk mitigation and get the most out of your resources. Build these strategic planning assumptions into your 2022 roadmap for the year ahead.
Three ways to secure cybersecurity risk, faster
Here are three ways to increase coverage of security risks, save time, and outpace threats, enabling your business to grow with efficiency and trust:
1. Identify.
Scale VRM with intelligence to make strategic and rapid decisions.
Vendor Risk Management is a key factor in assessing opportunities and mitigating risk fast. Organizations with strong vendor risk management programs systematically identify, assess, and mitigate threats to their assets and data that might be caused by the organization's supply chain.
Implementing manual VRM functions diminishes our ability to identify risks because time is of the essence in today’s threat landscape. Leveraging a robust VRM program enables the enterprise to streamline its portfolio analysis across the vendor ecosystem to rapidly determine the full impact of threats and prioritize accordingly.
2. Integrate.
Automated integrations empower you to do more with less and accelerate productivity.
If you have dozens of security tools in your tech stack, you’re not alone. But without integrated signals and workflows, you aren’t getting the most out of your resources. Utilizing a flexible, API-driven security ratings platform allows you to enrich findings from your SEIM, GRC, VRM, and risk intelligence platforms with a comprehensive data set, and vice versa. And with automated rule-based workflows, you’ll be able to drive collaboration and accelerate risk mitigation.
3. Assess.
Optimize security resources and focus on your business growth.
IT staff wear many hats and often don’t have the time to take full advantage of security investments or ramp up their education to sharpen their edge with the latest innovations. Utilizing services, assessments, training, and education can help optimize resources, evolve your knowledge-base and architecture, increase time to value while improving the organization’s security posture.
3 ways to execute your 2022 cybersecurity strategy
First published on SecurityScorecard




