Companies in Asia have been forced by the current pandemic to readjust their digital initiatives to respond to the unprecedented disruption to the way conduct their business.
A recent survey of senior IT executives in Asia gets the pulse of enterprise IT transformation in two key areas cloud migration and their ability to secure all user credentials with the rise of non-human identities.
The survey is conducted by FutureCIO on behalf of SailPoint. The data were further discussed during a C-Engage virtual roundtable: Recalibrating Your Identity Security Strategy for the Digital-Native Economy (Hong Kong and ASEAN).
Majority of enterprise workloads now in the cloud
Cloud migration has been an essential part of companies' digital transformation strategies for several years now. It has only accelerated at a significant phase over the last two years as the COVID-19 pandemic forced companies to adapt to the seismic shift in the business and social dynamics.
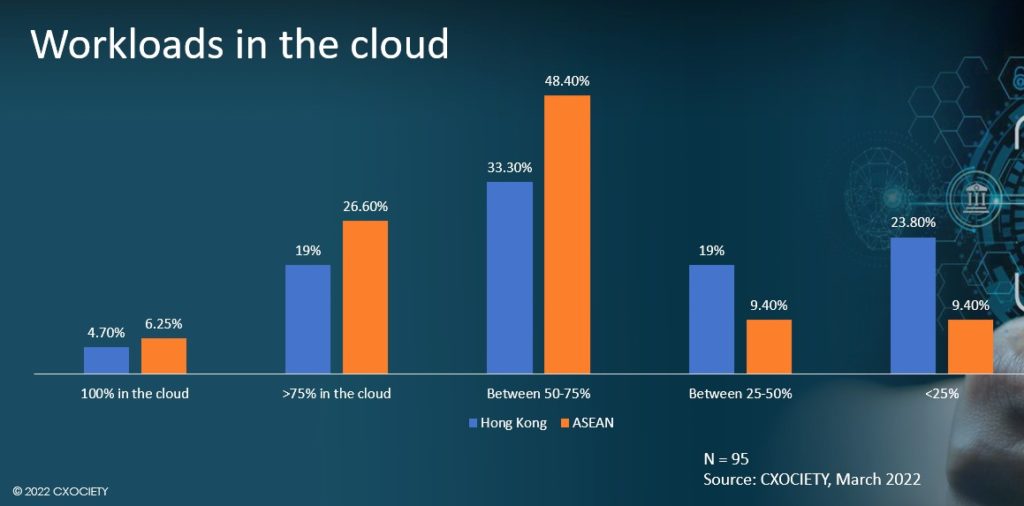
Source: CXOCIETY, 2022
With hybrid work now becoming the norm, companies have to arm their employees with the digital tools they need to effectively perform their jobs in a remote setting. Various enterprise applications are increasingly being moved and hosted on the cloud for higher availability, faster scalability and simplified IT management.
In the FutureCIO survey (see Figure 1), nearly three-quarters of Asia-based senior IT executives polled said that their organisations have migrated up to 75% of their workloads to the cloud. Drilling down to the numbers, nearly half of the respondents said that between 50% and 75% of their workloads are now in the cloud, while a quarter of them said over 75% of their workloads are now hosted in the cloud.
These figures indicate that companies are giving a vote of confidence to cloud technology as providing transformational value to their organisation – whether the migration takes the classic lift-and-shift approach, or it requires rebuilding applications so they can run at optimum level in the cloud.
With the rise of hybrid work, cloud migration is only expected to accelerate, and companies’ growing confidence in the platform will lead them to explore cloud-first initiatives for faster time-to-market as well as the flexibility to scale with delivering new online services.
Non-human identities - a blindspot in cybersecurity
Meanwhile, the same survey revealed that senior IT executives in Asia are quite positive about their company’s overall ability secure and manage both human and non-human identities (see Figure 2).
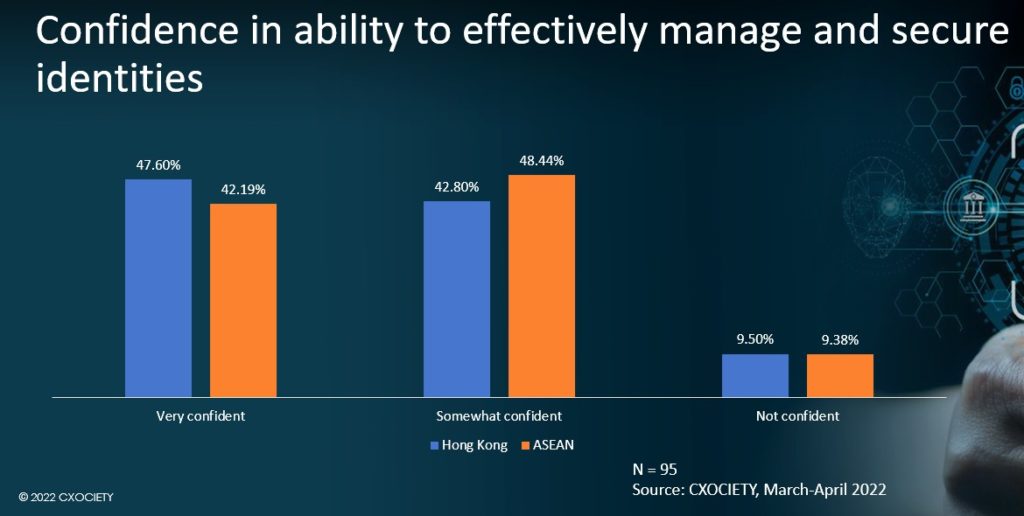
Source: CXOCIETY, 2022
A little over 90% of respondents revealed a degree of confidence for such a task – nearly split right down the middle with 50% of them very confident and another half somewhat confident in their company’s capability to safeguard the digital identities of human and non-human users in their network.
The survey results are quite remarkable given that many organisations have yet to deploy key identity-related security controls, and that the integration of identity with security is still a work in progress.
Non-human identities are the blindspot of cybersecurity as software bots, physical robots and IoT devices are plugged into enterprise infrastructure. These non-human identities – specifically IoT devices – are saddled by weak credential controls, which make them the primary target as the point of entry for most cyberattacks.
Companies are quite adept at applying proper access controls for human users tapping into their networks. However, the wide reach of digital initiatives from DevOps, cloud transformation and IoT among others have resulted in the exponential growth of non-human identities outnumbering human users by large margins.
Indeed, identities include not just people but workloads, services, and machines.
Machine identities are often linked with privileged accounts, and usually have a much bigger footprint than traditional human privileged accounts within modern IT infrastructures. These often pose a blind spot, since a machine, IoT, service account, and application identities are often overlooked when establishing security controls.
Challenges in protecting digital identities
The advent of non-human identities accessing the enterprise IT network is one of the major reasons why securing and managing digital identities is necessary in today’s hyperconnected world.
According to Identity Defined Security Alliance (IDSA), more attacks are originating from the use of legitimate credentials to breach an organisation. In the last two years, 79% of organisations reported a breach that can be traced back to a compromised identity.
Asian companies are having difficulty protecting this expanded security landscape, according to the FutureCIO survey (see Figure 3).
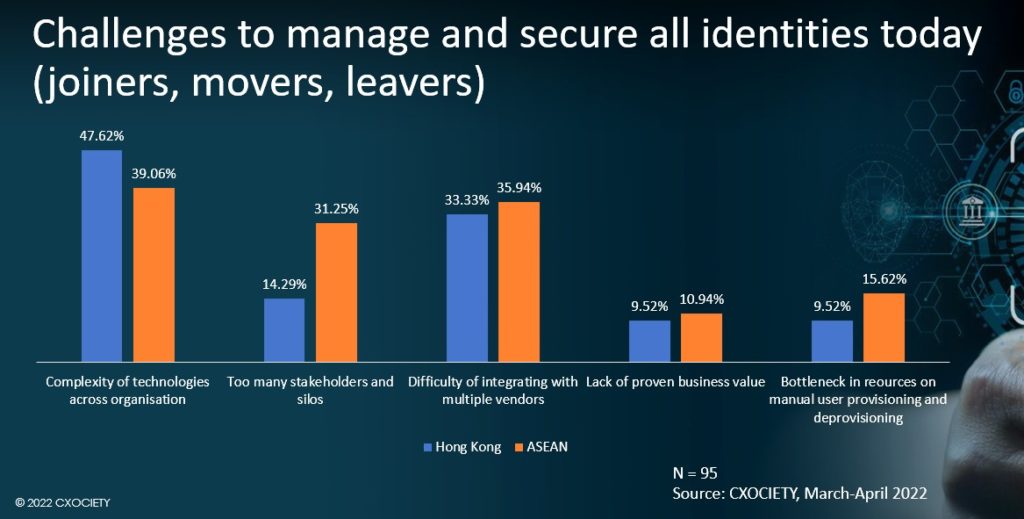
Source: CXOCIETY, 2022
The poll showed that 41% of senior IT executives cited the complexity of technologies across their organisation as the greatest challenge in safeguarding all digital identities in their network. Some 35% said the difficulty in integrating multiple vendors, while over a quarter or 27% of respondents noted that a large number of stakeholders and too many silos are hampering their ability to secure digital identities in their organisation.
These numbers suggest that companies need to revisit the cybersecurity framework to take into account the various technologies across the organisation and chart out a comprehensive and unified approach to protecting digital assets. More importantly, they need to ensure that their identity and access controls are aligned with the overall security posture.
In the last several years, the challenge has shifted from protecting the perimeter to protecting identities and the resources they access. A dynamic digital environment with more devices, applications and endpoints means a dissolving perimeter that can be exploited more easily when protected by traditional solutions.
A more holistic identity management strategy that could ensure end-to-end visibility, control, and protection.




