As security threats run aplenty, new vulnerabilities faced from remote working and the upward trajectory of malicious activity, including ransomware continues to hit businesses in the region.
The state of cyber resilience today
The security landscape has become increasingly fraught with danger. There were on average 270 attacks per company recorded in 2021, a 31% increase from 2020.
Security is fast becoming an imperative for most organisations. Accenture’s latest State of Cyber Resilience Report revealed that 85% of global respondents agree that cyber security strategies need to be developed with business objectives in mind.
Yet, the truth is that 78% do not know when or how a cyber security incident will affect their organisation. The report also found that 81% of respondents also report struggling with staying ahead of their hackers, citing it as a “constant battle” with “unsustainable costs”.
Facing the security crossroads
Unsurprisingly, security budgets have increased. Accenture notes that IT security budgets are now up to 15% of an organisation’s total IT spend, 5% higher than the spendings reported in 2020.
As they look to defend themselves against the increasingly rampant cyberattacks, organisations find themselves at a cyber crossroad. Most think of cyberattacks as an either-or situation, where they are forced to choose between business objectives or their security priorities.
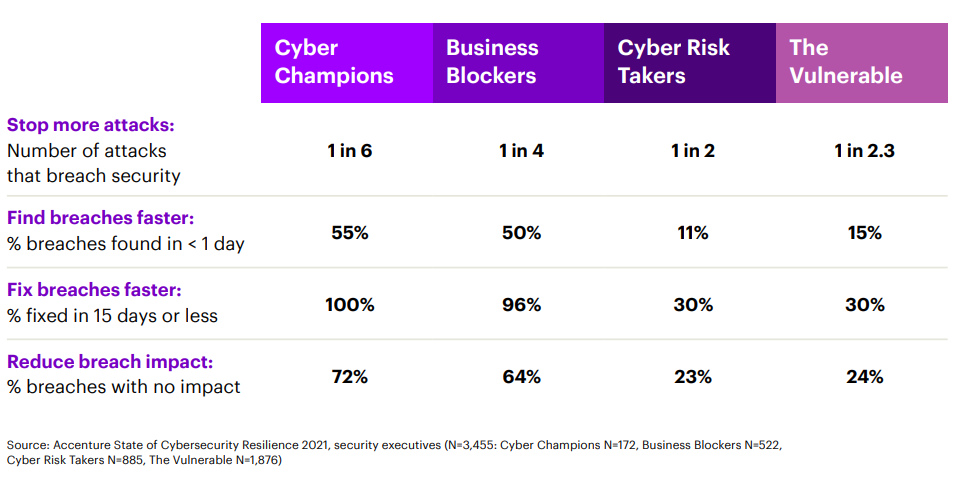
However, there is a third option to these long-outdated approaches. Cyber Champions, defined by Accenture as organisations that were able to achieve strong business performance while maintaining super cyber resilience were found to be ahead of the pack because of their ability to strike a balance between the two.
Absolute security is impossible, and organisations need to move from a posture of cyber security to one of cyber resilience. While cyber security is about reacting, cyber resilience is about anticipating and being able to continuously deliver on the intended outcomes despite adverse cyber events.
By adopting a stance that incorporates cyber resilience, Cyber Champions were better at stopping attacks, were faster at finding and fixing breaches, and were more adept at reducing the impact of cyber threats. This is as compared to their peers who were still relying on traditional cyber security postures.
Let CISOs do their jobs
To contend with hackers, leaders must first learn to think like them. Understanding how information can be uniquely externalised and exploited by adversarial forces is key to getting inside the minds of cyber attackers and helping organisations stay ahead of them.
Within the company, Chief Information Security Officers (CISOs) are the individuals best placed to do this, but they must be able to marry their technical knowledge in areas of information and data security with a keen understanding of the business.
Which can only be done when CISOs are deeply embedded in the heart of the business decision-making process and are no longer operating in a security-focused silo. Accenture research finds that by aligning cybersecurity and business needs, firms can reduce the frequency of successful cyberattacks and reduce their cost by up to US$294,000 per instance.
With a seat at the table, CISOs can gain a broader perspective that serves the whole business well. This also means they will be better equipped to uncover potential weak points and prioritise securing the data and applications that are the most mission-critical to the business.
We also find that CISOs with more autonomy over their cybersecurity budgets fared better at staying ahead of threat actors.
Keep an eye on what hackers want
Like business competitors, cybercriminals and more advanced adversaries are innovating continuously. Businesses and their security teams must do the same and do so within budget.
By taking a threat-centric approach and identifying the firm’s “crown jewels” – the data and applications most critical to the business – teams can then better design and execute threat and vulnerability programs that secure and deny access to them.
This requires firms to be realistic about their cyber security postures. The most prepared organisations measure and monitor the maturity of their cyber security programmes at least once a year to identify new or emerging gaps.
For example, many companies would have identified gaps in cyber security readiness with staff potentially not having the required knowledge to stay secure as they shifted to predominantly remote work models. This would have been combatted through education and potentially implementing more stringent access controls.
Additionally, working with red teams – white hat hackers that test an organisations’ cyber defences – to simulate attacks and actively seek out weak links can provide valuable information in conceptualising how your IT ecosystem could be vulnerable.
Remaining nimble
In a constantly shifting threat landscape, knowledge is power, but only if we can act on it. To make insights and threat intelligence actionable, organisations need to ensure that they have a robust security system that can adapt to the demands of a cloud-first world.
Cloud has opened new doors for hackers; easy remote access has turned computer systems into coffee shops where people and services move in and out. Leveraging cloud for security will help organisations better adapt to the rapidly evolving digital landscape and respond more effectively to modern security challenges.
This becomes increasingly pertinent as the world transitions quickly into a cloud-first one. In fact, over the next three to five years, it is predicted that more than two-thirds of workloads within APAC businesses will shift into the cloud.
Despite this, nearly one-third of global respondents say that security is not part of the cloud discussion from the outset, and report that their organisation is trying to play catch-up.
With 44% of APAC respondents citing security and compliance risk as one of the top barriers to cloud migration, security is seen as the biggest inhibitor to a cloud-first journey when in reality, it can be its greatest accelerator.
Too often, security is only added at the end of the cloud-first journey which leaves the organisation vulnerable to attacks. Thinking like a hacker means ensuring that these potentially vulnerable areas are secure and consistently embedding security within every aspect of it.
Focusing solely on business objectives exposes organisations to the threat of cyber attacks, especially in a world where responding to and preventing cyber threats have become a non-negotiable.
Nurturing the right conditions, fostering a mindset of resilience, and working actively to adapt people and processes will be part of winning the race towards cyber resilience.




