SETI@home was launched on May 17, 1999, to help search for extra-terrestrial – that’s right: ET – by using the CPU of idle computers connected to the internet to perform data analysis. A few other projects used the same concept: Great Internet Mersenne Prime Search to search for prime numbers or a number one less than a power of two; Einstein@Home to search for signals from rotating neutron stars and to generate accurate three-dimensional dynamic models of stellar streams in the immediate vicinity of the Milky Way.
Yes, at a very young age I was in love with astronomy (not so much with maths though).
But like many good ideas, the concept can be turned for nefarious purposes.
Crytojacking and why IT should be concerned
Cryptojacking is one such abuse of a good idea. Investopedia defines cryptojacking as a form of cyberattack in which a hacker hijacks a target's processing power to mine cryptocurrency on the hacker's behalf.
Why cryotojacking? Cryptocurrency mining (cryptomining) is a very energy-intensive process with some estimates putting the figure at 67 terawatts hours per year.
Cryptojacking targets vulnerabilities in Windows and in applications that run on server hardware, for example, databases. Cloud providers in particular present a juicy target but the direct victims are applications running in the cloud meaning your ERP, CRM or any application that has a database. Yes, the onus should be on operators of these cloud services to prevent cryptojacking but you may want to check the fine print in your service contracts. Otherwise, you could end up paying for compute resources you never used in the first place. [see attack timeline below for how this happens]
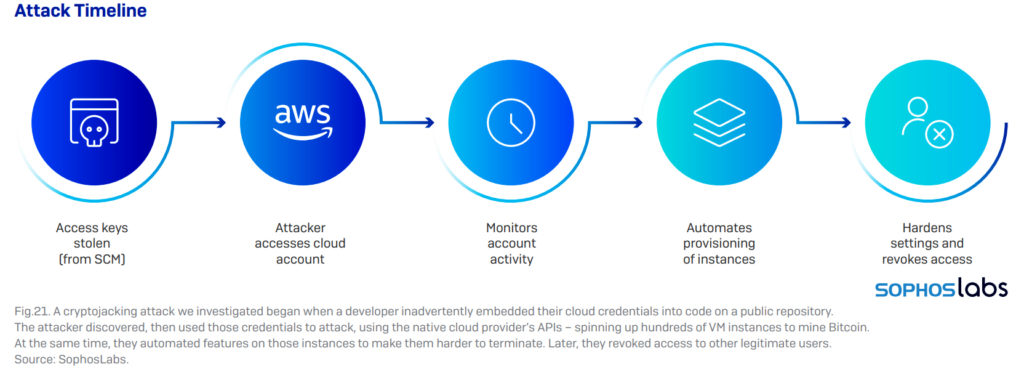
MrbMiner et al
The developers of MrbMiner target internet-facing database servers (SQL servers) because these servers as designed for compute-intensive applications.
In a time where ransomware attacks have caused multi-million-dollar losses, it can be easy to treat cryptojacking as a nuisance rather than the serious threat that it is. Organisations tend to get complacent where cyptojacking is concerned as it is a silent and invisible threat, but it is important to remember that it is easy to implement and very difficult to detect.

Gabor Szappanos, threat research director, SophosLabs, warned not to treat cryptojacking less than a cyberattack that it is: “Once a system has been compromised it presents an open door for other threats, such as ransomware. It is therefore important to stop cryptojacking in its tracks. Look out for signs such as a reduction in computer speed and performance, increased electricity use, devices overheating and increased demands on the CPU.”
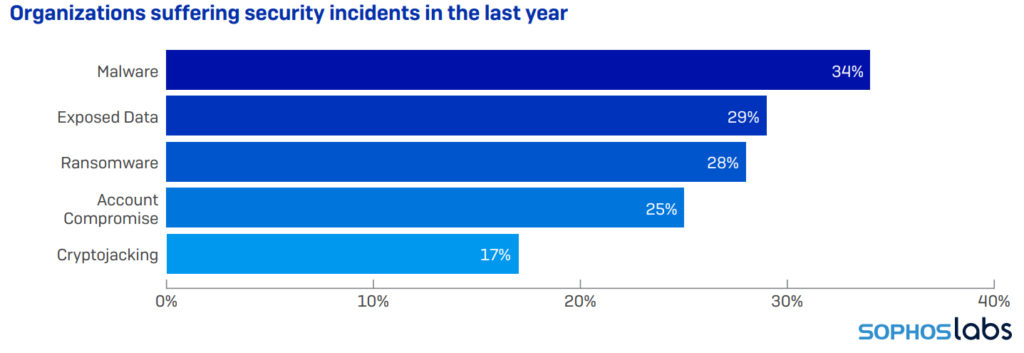
The top five security attacks of 2019
After all is said and then and you still think cryptojacking is not a concern, checkout the top five security incidents of 2019. See something you recognise?
Key takeway
To stay ahead and remain vigilant, IT managers and individuals should look out for signs such as a reduction in computer speed and performance, increased electricity use, devices overheating and increased demands on the CPU. There are also other business implications like opportunity costs when systems are slow to respond to legitimate demand, security risks, reputational and regulatory costs and ethical concerns.
The Sophos report, Standing Up to Cryptojacking, is an interesting read because it illustrates the ease with which to set yourself up to be a cryptominer, how to make money from cryptomining, and the ways to cryptojacking.
Did you know adblockers may help prevent cryptojacking? Some options to consider in the fight against cryptojacking: block websites hosting JavaScript miners both at the gateway and the endpoints; stop cryptomining malware at all points in the attack chain; and kickout cryptomining apps from your network.
Sophos offers additional suggestions:
- Keep devices patched
- Use mobile management technology to identify native mobile apps that shouldn’t be there
- Educate staff on cryptomining (and how it is something not acceptable to the company)
- Maintain strong password policy at least until we have a better way of IAM tools
- Keep watch of tell-tale signs that you have been cryptojacked – slow network, rising electricity bill, or spikes in CPU consumption




