The ExtraHop 2022 Cyber Confidence Index—Asia Pacific, noted that 83% of organisations in Asia Pacific were breached by ransomware at least once in the past five years, but only 32% publicly disclosed that an incident occurred.
The study which included respondents from Australia (43%), Singapore (52%), and Japan (23%) noted that growing cybersecurity budgets don’t necessarily buy improved degrees of protection and confidence, with only 39% of IT decision-makers (ITDMs) in Asia Pacific expressing a high degree of confidence in their organisation’s ability to prevent or mitigate cybersecurity threats, and an equal percentage having low confidence.
Of those that are confident, many shouldn’t be: Lax security practices, continued reliance on legacy technology, and actual attack numbers all suggest that confidence levels may be overstated or unrealistic.
This may explain why executives in the region don’t back transparency or disclosure of incidents since they can’t be confident history won’t repeat itself. It often does: On average, Asia Pacific businesses that identify as a ransomware victim will be infected—or reinfected—at least once a year.

“Security leaders in Asia Pacific are facing a challenge. They’re in disagreement with executives around disclosure, they’re getting increased budgets, but it doesn’t feel like enough, and there is worry around legal obligations,” said Jeff Costlow, CISO, ExtraHop.
He suggested that these leaders need to focus on their risk tolerance for their IP, data, and customer data and arm their teams with the tools and network intelligence that can help them defend their most critical assets.
"This survey reinforces the challenge organisations face in preventing attacks. Let’s arm defenders with the tools and forensics needed to prevent an intrusion from becoming a full-blown breach,” he added.
Other findings:
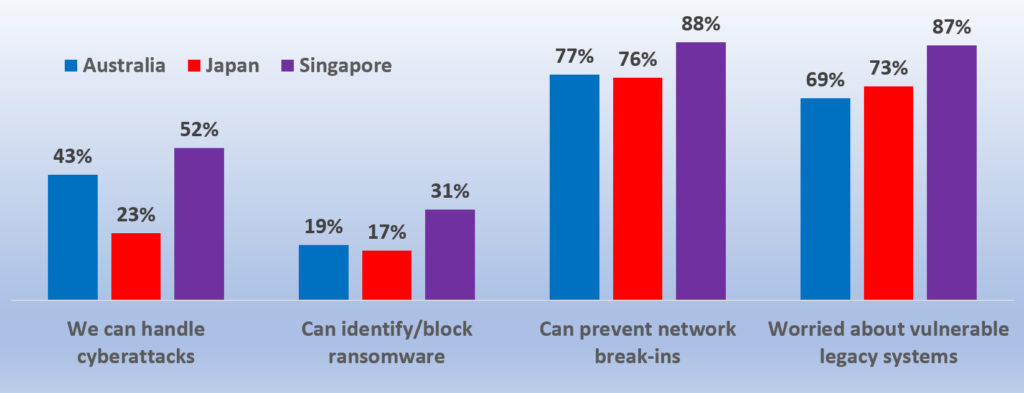
Source: Avanade 2022
The cost of ransomware is high: 45% of organisations in Asia Pacific have paid a ransom, despite a majority believing that paying increases the number of attacks. An almost equal proportion—44%—say they are covered by either specific or general insurance policies.
Ransomware attacks come in numbers: Only 17% of respondents said they experienced no ransomware incidents in the past five years; 46% had experienced one to five attacks, while 35% had experienced six or more. But 20% of organisations wouldn’t tell anyone if they were breached anyway, suggesting the proportion of organisations hit by ransomware is probably a lot higher.
Corporate leaders and security teams disagree on disclosure: Only 32% of organisations are public and transparent about ransomware attacks; 48% let some people know but keep it as private as possible, and 20% tell no one. This is largely against the wishes of IT security personnel, of whom 66% feel it would be better to be transparent and public about ransomware attacks.
Singapore-based firms most worried about official repercussions: The ‘stick’ of legal action and fines promotes action by senior management in security-related decisions, with a total of 73% agreeing with this statement. However, there are significant regional variations with 86% of Singapore-based organisations worried, compared to 68% in Japan and 64% in Australia.
An attentive focus on supply chain risks: Just over half (51%) of organisations allow third-party access to their networks, and most (86%) have considered the security aspects. This is highest in Singapore (96%) and Australia (87%) but lower in Japan (74%) where one in five haven’t assessed the security implications of such arrangements.
Budgets on the rise: Just under two-thirds (61%) of organisations expect cybersecurity budgets to increase in 2022. This is higher in Singapore (70%) and Australia (66%) but lower in Japan where 48% anticipate budget increases and 49% expect to see stable budgets year-on-year. Across the board, very few expect cybersecurity budgets to decrease.
Slow response times to critical vulnerabilities: Only 26% of teams are able to enact mitigations or apply a patch (where available) in under a day, with 39% taking one-to-three days, 21% needing a week, and 8% requiring a month or more.
Legacy technology hits confidence: 54% of respondents last updated their cybersecurity infrastructure in 2020 or before; one-fifth of organisations have technology that has gone at least three years without being updated. Additionally, 76% state they are concerned about legacy systems being attacked.
Even as companies continue to innovate with cloud technologies and remote workforces, IT infrastructures remain vulnerable to past architectural decisions, with legacy technology providing ongoing opportunities for attackers to infiltrate networks and unleash ransomware attacks.
A lack of visibility and effective use of data has also contributed to organisations' obstacles in identifying vulnerabilities and preventing ongoing ransomware attacks.

"Digital adoption rates have skyrocketed in Asia, especially during the pandemic as organisations prioritised modernising their legacy systems to support remote and hybrid working. Yet almost 80% of Asian organisations are worried about these legacy systems being attacked,” said Kenneth Chen, VP of Asia, ExtraHop.
He added that digital transformation is a journey and organisations need tools to support both legacy infrastructure and new SaaS solutions—tools that provide visibility into their network, protocol use, and software behaviour so they can identify and stop an attack before it can compromise the business.
Recommendations and next steps
Organisations should look for ransomware mitigation tools that can capture network communications across all devices, and use technologies like behavioural analytics and artificial intelligence to detect anomalies that signal a ransomware attack in progress. By leveraging a network detection and response platform, defenders can detect and stop the lateral movement and other post-compromise activity of ransomware attackers before they achieve real damage.
The report identifies several courses of action that Asia Pacific organisations intend to take in 2022.
Network Detection and Response (NDR): 42% intend to invest in NDR systems in the coming year, adding to the 34% of organisations that already have such systems in place.
Social engineering strategy: 47% of respondents plan to implement a social engineering strategy in 2022, building on the 21% that already have one in place today and the 58% that train staff to recognise social engineering cues. This correlates with a finding that about half of ITDMs are already confident in staff ability to identify social engineering-based cyberattacks.
Improved threat training and identification: 46% plan to implement staff threat training, and the same proportion plan to improve the speed of threat identification.
Onboarding more resources: 40% of organisations plan to increase or recruit dedicated internal security staff. The same proportion intends to engage external managed security services in 2022.




