Identity theft has become one of the most frequent tactics hackers use to achieve their malicious goals. Phishing personal information for the purpose of using someone else's profile to make purchases or transfer funds are some of the dangers looming for those who prefer to do their banking online.
Identity thieves go through personal belongings, electronic devices, social accounts and even trash to find more about their target. They can access corporate databases to steal lists of customer information, destroy their records, sell the data to third parties or even assume another person's identity.
Security leaders experience disruption in Identity and Access Management (IAM) due to increased customer traffic on digital channels and the expansion of the remote workforce during the pandemic. According to a global study on data breaches, the average cost rose from US$3.86 million in 2020 to US$4.24 million in 2021.
FutureCIO sat with Edwardcher Monreal, HID Global's principal solutions architect, IAM consumer authentication solutions, to demystify some of the tools of the trade in hacking identity and security access.
Identity hacktivist - the modern-day burglar
Hackers employ various tools to break into a personal bank account. We ask Edwardcher about the latest tricks up the sleeves of cyber attackers and what security experts can do to tackle the problem.
In an ever-changing cybersecurity landscape, what is considered more pragmatic than other solutions?
One of the trends we see today focuses on mobile channels, where banks engage their customers through an app. Fraudulent transactions on mobile apps are usually premeditated by identity theft where stolen credentials are used to access bank accounts from a mobile device.
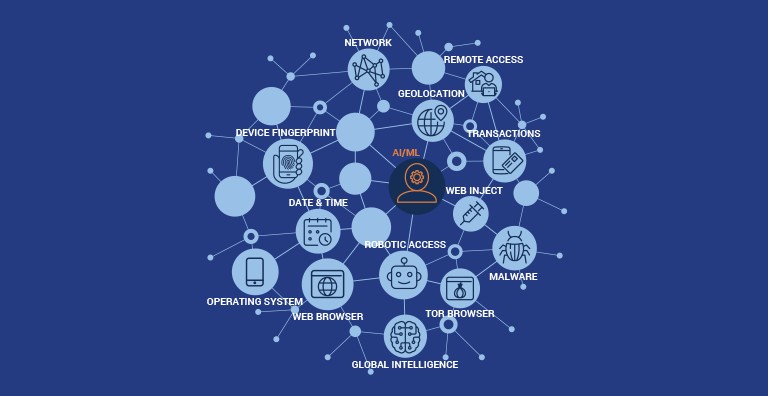
Specifically, it is about leveraging customer data and understanding their behaviour and incorporating AI (Artificial Intelligence) and data analytics into the banking toolkit to combat fraudulent transactions.
During COVID, in ASEAN in particular – several banks were ill-prepared during a time when people were compelled to bank online through a mobile app. Banking credentials are used to perform basic services like paying a mortgage, a utility bill or transferring funds to an account.
During this user journey, user behaviours are studied and their data is 'mined' to attain hyper-personalisation. From a security perspective, this data can be used by banks to understand users' behaviour profiles and build a better understanding of the risks and identify vulnerabilities within particular transactions.
What are the other types of attacks deployed by hackers?
Edwardcher Monreal: Bank security specialists build threat models to identify possible attacks. Banks leverage these solutions to perform the necessary risk management and data analytics, using AI to help automate decision-making. It assesses customer behaviour risks and seeks to provide a better consumer experience in a safer online banking environment.
What happens when a bank account is stolen?
In an ‘account takeover’ through a banking app, a hacker can use a stolen credential acquired from a Man in the Middle (MiTM) attack through your wireless network using a Wi-Fi Pineapple device or similar ready-made attack kit while you surf in public access points at coffee shops or airports.
Most of them can also get stolen credentials via phishing campaigns by subverting trust through social engineering. In this situation, a hacker is able to acquire someone else’s credentials without his/her knowledge, using the stolen ID to access an e-wallet or savings.
Detecting online-banking anomalies

A world without passwords would result in fewer phishing incidents. But in reality, many consumers still rely heavily on password-based systems – at least as the first-factor access point.
Two-step authentication - is this fully safe?
"The direction forward is that the consumer market will rely less on passwords in future. As FIDO gains in popularity, we will definitely see a shift towards password-free means and biometric keys to access our credentials to go online."
Edwardcher Monreal
People understand 'multi-factor authentication' as a second step to logging into their accounts. But even if you have a good two-step verification procedure but rely on SMS - you're still not considered secure.
Scammers also use social engineering tactics in spear-phishing to fool victims into responding to a false sign-in attempt, e.g. someone in the organisation asks you to ‘change your passwords' when in fact, you had not requested one. The goal of the ID thief is to find 'the weakest link' - and it is not really in the system but actually - the individual.
Biometric solutions have caught on, will actually find usernames and passwords becoming redundant?
Edwardcher Monreal: As a security practitioner, I would like to see less reliance on passwords because they are based on what you can write down or save on a file. If an attacker can access that, then that's really - game over.
Multi-layered approach to threat and fraud detection
Gartner's 5 layers of fraud prevention
Image source: https://www.hidglobal.com/sites/default/files/resource_files/iams-hid-risk-management-solution-cc-en.pdf
Fraud detection
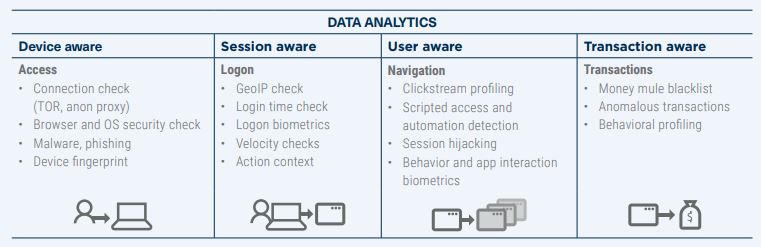
With AI and data analytics systems at your disposal, you can identify mobile fraud earlier. While not all solution systems are identical, some only focus on behavioural biometrics while others specialise in device intelligence or malware in mobile devices.
It is not just about having the actual data and using it, but it is more important to have in place a system that is able to learn and understand what could happen. Most banks should employ a well-rounded set of solutions that can help identify threat patterns.
What can CIOs and CSOs do to ensure that they have more secure access, especially for the financial and banking landscape?
Edwardcher Monreal: Seek advice from regulatory bodies on cyber threats, trends and current issues. For example, Singapore, the Philippines and Indonesia have specified guidelines on how to manage and mitigate such risks towards real-time fraud detection and identification.