That businesses in Asia-Pacific are adopting cloud computing technology is no longer being debated. The journey to the cloud, whether independent or part of a digital transformation journey, brings with it calls for reviewing an organisation’s security strategy, practices and policies.
Compounding the challenge for organisations moving to the cloud is the increased attention it has drawn from criminals elements who are using the very same cloud platform to target organisations that have relatively new or immature when it comes to securing their infrastructure, on-premises, in the cloud and hybrid.
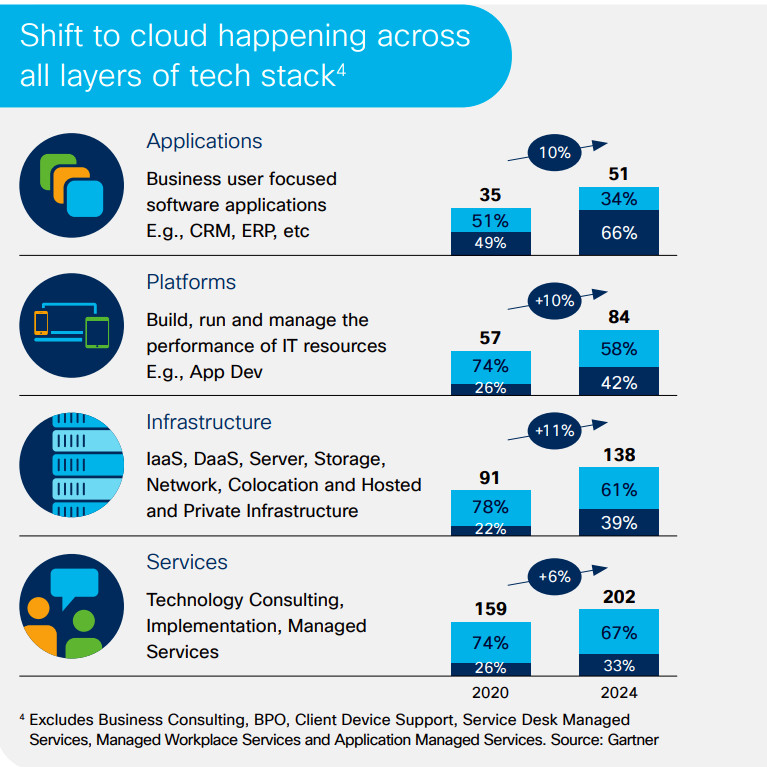
The eighth annual Business at Work report by Okta highlights three key points:
- Collaboration and security tools were the two most popular categories of tools deployed through the Okta Integration Network over the last 12 months.
- Google Workspace, Slack and Zoom have won many new customers across Asia-Pacific (APAC). They grew 68%, 40% and 37% YoY in terms of the number of customers in the region, respectively.
- Network security tool Palo Alto Networks GlobalProtect, workflow platform ServiceNow, email security tool Mimecast, and small business accounting software Xero were the most popular among APAC customers.

FutureCIO spoke to Brett Winterford, regional chief security officer, Asia Pacific & Japan, Okta, to get his perspective on the report and its implications to businesses in Asia-Pacific.
Remote work, and the use of multi-cloud, as you mentioned, are now the norm. How is this impacting the choice of security and collaboration tools? And do you see a trend towards more subscription-based services for these types of tools?
Brett Winterford: Absolutely. As organisations’ total technology architecture changes to support remote work, so does the security tooling. Many CIOs now want security services to be delivered to endpoints via the cloud, rather than trying to push all their traffic through a security stack at the edge of the network.
So, collaboration and security are the two most popular categories for tools and apps according to this study. What does that tell us about the environment that CISOs and CIOs operate in?
Brett Winterford: Some of it relates to how organisations responded to the pandemic. They were operating under extreme pressure - some of the decisions they had to make to enable remote access during the initial lockdowns - like using Remote Desktop Protocol to remotely administer systems - exposed them to heightened risks, but they didn’t have a choice given how fast they had to move.
Now we are at the point where employees expect frictionless remote access, and consumers expect to interact digitally with their service providers. What they're asking from us is a way to support remote work, from anywhere, and from any device.
Recently, we have started to see an increase in interest around Zero Trust. What’s your view on that concept?
Brett Winterford: The traditional security model was for users to access apps and data from inside the perimeter of a trusted network. And once a user authenticates to that network, there is an assumed level of trust. Unfortunately, that assumed level of trust is what attackers like ransomware actors have most readily abused.
Because the attacker only needs to get one foothold in a typical network and before you know it - sometimes in as little as a few hours - they can access the domain controller and install malware on every device on that network.
Specific to security strategies and postures, and even frameworks that organizations are using, how will changes in the way companies consume security tools and collaboration tools impact them? How will these changes impact organizations and existing security strategies and postures, or it's already done?
Brett Winterford: Organisations increasingly realise that many apps today are consumed as-a-service and from unmanaged mobile devices. Existing security frameworks in APAC haven't kept pace with that. I’m very pleased to see NIST, in the United States, taking the lead globally in guiding organisations on Zero Trust definitions and requirements. I’d like to see more of that in APAC.
What is your expectation of the security landscape? Do you anticipate the shift away from current norms that we've seen in the last couple of years?
Brett Winterford: I expect APAC businesses to adopt passwordless authentication in a big way this year, to make the process more secure but without introducing friction. That’s going to set many adversaries back a long way because the bulk of the attacks the world is currently seeing today involve the abuse of memorized secrets.
Once passwordless is widely deployed, brute force attacks and the recycling of stolen credentials will be far less viable for hackers.
Will the return to work require a reset of security strategies? If yes, how do you envision CIOs and CISOs going about making the shift?
Brett Winterford: No, I don’t think it will.
Once an organisation has taken a Zero Trust approach, it won’t matter as much whether users are accessing apps and data from the office, or the home.
The network perimeter still matters, but it is one of several attributes ― rather than the only attribute ― that we should assess to allow or deny access. Contexts like user behaviour, and whether a device or network is new to a user, have become important attributes.
How do you see the CIOs and CISOs balancing three things ― one is the desire to transform how we operate as a business, including the products and delivery models that we have, against securing the organization, which is primarily a CISO problem, and against optimizing productivity/efficiency of the workforce, which is usually the CIOs’ problem?
Brett Winterford: Speaking in terms of identity access management (IAM), this is where a single identity and authentication platform that satisfies all these needs can be transformational. If you have one platform that can allow organisations to authenticate not just their employees, but also external parties like contractors, partners and customers, it is dramatically simpler to manage.
And when it is operated as a cloud service, that enables technology teams to focus on delivering their core business instead of reinventing authentication for every app.




