
"Enterprises today forced to shift to dynamic hybrid work, supporting devices, users and customers from anywhere, there is no longer a secured perimeter. BYOD, mobile devices, and company issues devices are all used by staff to get work done," said Kenny Yeo, director of Global Cyber Security Advisory and head of Asia Pacific Cyber Security Practice at Frost & Sullivan.
In such an environment, identity security becomes even more important right now, concludes Yeo.
According to IDC’s Asia-Pacific excluding Japan (APeJ) Security and Trust Study 2022 69% of CEOs are now engaged in cybersecurity interactions either weekly (37.2) or bi-weekly (31.5%), supporting the ongoing importance of cybersecurity to the business.
But are words translating into action? Perhaps half-heartedly?
The CyberArk 2022 Identity Security Threat Landscape Report reveals that despite its management rhetoric, 84% of senior security professionals in Asia (82% in Singapore) said cybersecurity has taken a back seat in the last year in favour of accelerating other digital business initiatives.

Teck Wee Lim, CyberArk’s head of ASEAN, says despite the prevalence of news about ransomware and supply chain attacks, cybersecurity is not a top focus for many organisations.
“As the region eases its Covid-19 restrictions and resumes more economic and social activities, organisations here need to further enhance their cyber resiliency by adopting proactive cybersecurity strategies such as Identity Security controls based on Zero Trust principles to ensure that both human and machine identities are protected,” he continued.
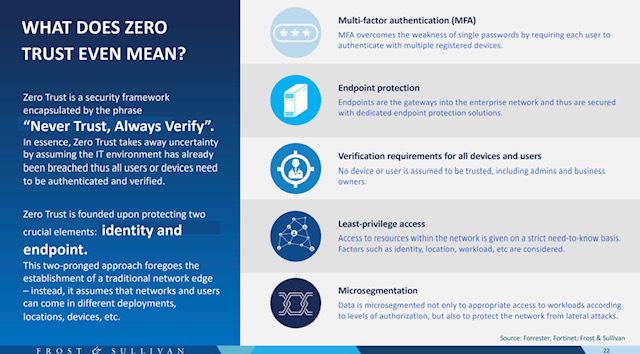
"Identity is a core part of the zero trust approach that many of us hear about today," added Yeo.
Singaporeans should be afraid
The CyberArk report revealed that almost 80% of local organisations surveyed have experienced ransomware attacks in the past year: two each on average. In addition, 74% of non-humans or bots have access to sensitive data and assets.
According to CyberArk, machine identities now outweigh human identities by a factor of 27 times on average - outstripping the estimated 28 digital identities that a staff member holds. Seventy-eight per cent of local respondents indicated that their organisation is susceptible to carefully crafted attacks such as a tailored phishing email to an individual with high levels of access.
Far more worrisome is the 46% of respondents that acknowledged having no identity controls in place for their business-critical systems.
A growing identity problem
Every major IT or digital initiative results in increasing interactions between people, applications and processes, creating large numbers of digital identities. If these digital identities go unmanaged and unsecured, they can represent a significant cybersecurity risk:
- 77% of non-humans or bots have access to sensitive data and assets.
- Machine identities now outweigh human identities by a factor of 59x on average.
- 91% store secrets in multiple places across DevOps environments, while 87% say developers typically have more privileges than necessary for their roles.
The 2022 attack surface
Secular trends (market activities that unfold over long-time horizons) of digital transformation, cloud migration and attacker innovation are expanding the attack surface. The report reveals that:
- Credential access was the number one area of risk for respondents (at 43%), followed by defence evasion (34%), privilege escalation (32%) and execution (32%).
- 77% of the organisations surveyed have experienced ransomware attacks in the past year: two each on average.
- 81% of respondents indicated that their organisation is susceptible to carefully crafted attacks such as a tailored phishing email to an individual with high levels of access.
- 74% have done nothing to secure their software supply chain post the SolarWinds attack and most (75%) admit a compromise of a software supplier would mean an attack on their organisation could not be stopped.
Creating cybersecurity debt
Security professionals in Asia agree that recent organisation-wide digital initiatives have come at a price. In some instances, security programs and tools have grown but not kept pace with what organisations have put in place to drive operations and support growth.
The resulting price (or cost to the business) is Cybersecurity Debt. This debt has arisen through not properly managing and securing access to sensitive data and assets, and a lack of Identity Security controls is driving up risk and creating consequences.
The debt is compounded by the recent rise in geopolitical tensions, which have already had a direct impact on critical infrastructure, highlighting the need for heightened awareness of the physical consequences of cyberattacks, including:
- 84% agree that their organisation prioritised maintaining business operations over ensuring robust cyber security in the last 12 months.
- 48% have Identity Security controls in place for their business-critical applications.
Cyberark CEO, Udi Mokady comments that the past few years have seen spending on digital transformation projects skyrocket to meet the demands of changed customer and workforce requirements.
“The combination of an expanding attack surface, rising numbers of identities, and behind-the-curve investment in cybersecurity – what we call Cybersecurity Debt – is exposing organisations to even greater risk, which is already elevated by ransomware threats and vulnerabilities across the software supply chain.”
“This threat environment requires a security-first approach to protecting identities, one capable of outpacing attacker innovation,” he continued.
Action items
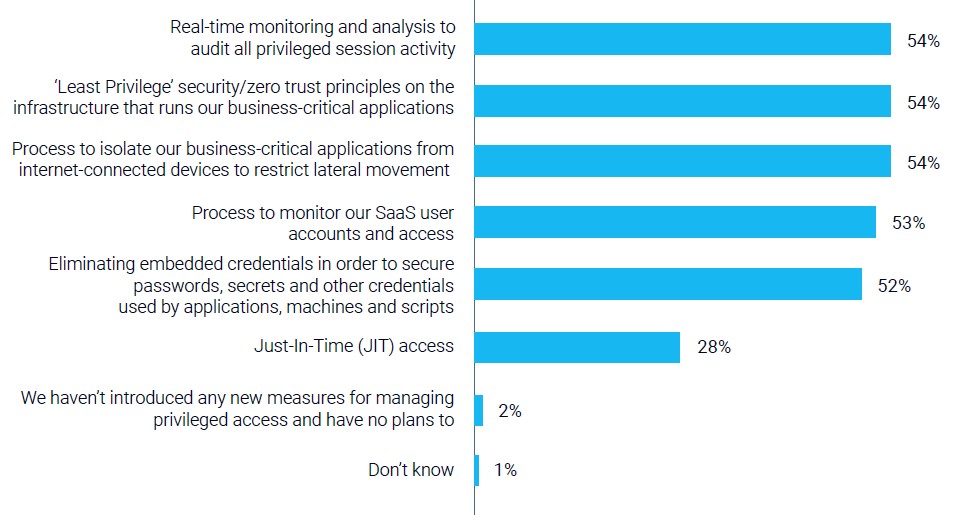
humans and non-humans?
Source: 2022 Identity Security Threat Landscape, CyberArk
75% of respondents in the study are calling for greater transparency suggesting a Software Bill of Materials would reduce the risk of compromise stemming from the software supply chain.
Among respondents to the survey, least privilege security/Zero Trust principles on infrastructure that runs business-critical applications (57%), process to monitor SaaS user accounts and access (57%) and process to isolate business-critical applications from internet-connected devices to restrict lateral movement (53%) were cited as the top three measures that most CIOs and CISOs questioned in the survey have introduced (or plan to introduce).
The top three strategic initiatives to reinforce Zero Trust principles are workload security; Identity Security tools; and data security.




