Today’s Security Operation Center (SOC) teams are protecting a fast-expanding digital footprint that extends across hybrid cloud environments – creating complexity and making it hard to keep pace with accelerating attack speeds.
They can be slowed down by labor-intensive alert investigations and response processes, manually stitching together insights and pivoting between disconnected data, tools and interfaces.
According to the Global SOC Study Results published last month, SOC professionals spend around one-third of their day investigating and validating incidents that turn out to not be real threats.
IBM Security QRadar Suite unveiled
At the RSA Conference running this week in San Francisco, IBM unveiled its new security suite designed to unify and accelerate the security analyst experience across the full incident lifecycle. The company has rearchitected its threat detection and response (TDR) portfolio to maximise speed and efficiency, and to meet the specific needs of today’s security analysts.

The new IBM Security QRadar Suite includes EDR/XDR, SIEM, SOAR, and a new cloud-native log management capability – all built around a common user interface, shared insights and connected workflows, with the following core design elements:
- Unified Analyst Experience: Refined in collaboration with hundreds of real-world users, the suite features a common, modernised user interface across all products: designed to dramatically increase analyst speed and efficiency across the entire attack chain. It is embedded with enterprise-grade AI and automation capabilities that have been shown to speed alert investigation and triage by 55% in the first year, on average.
- Cloud Delivery, Speed & Scale: Delivered as a service on Amazon Web Services (AWS), QRadar Suite products allow for simplified deployment, visibility and integration across cloud environments and data sources. The suite also includes a new, cloud-native log management capability optimized for highly efficient data ingestion, rapid search and analytics at scale.
- Open Foundation, Pre-Built Integrations: The suite brings together the core technologies needed across threat detection, investigation and response - built around an open foundation, an extensive partner ecosystem, and more than 900 pre-built integrations that provide strong interoperability between IBM and third-party toolsets.

“In the face of a growing attack surface and shrinking attack timelines, speed and efficiency are fundamental to the success of resource-constrained security teams,” said Mary O’Brien, general manager, IBM Security.
The IBM Security QRadar Suite represents a major evolution and expansion of the QRadar brand, spanning all core threat detection, investigation and response technologies, with significant investment in innovations across the portfolio.
Delivered as a service, the IBM Security QRadar Suite is built on an open foundation and designed specifically for the demands of hybrid cloud. It features a single, modernized user interface across all products – embedded with advanced AI and automation designed to empower analysts to work with greater speed, efficiency and precision across their core toolsets.
By helping analysts respond faster and more efficiently, QRadar technologies can also help security teams improve their productivity and free up analysts’ time for higher value work.
The QRadar Suite automatically contextualises and prioritises alerts, displays data in visual format for rapid consumption, and provides shared insights and automated workflows between products. This approach can drastically reduce the number of steps and screens required to investigate and respond to threats. Examples include:
- AI-Powered Alert Triage: Automatically prioritizes or closes alerts based on AI-driven risk analysis, using AI models trained on prior analyst response patterns, along with external threat intelligence from IBM X-Force and broader contextual insights from across detection toolsets.
- Automated Threat Investigation: Identifies high-priority incidents that may warrant investigation, and automatically initiates investigation by fetching associated artifacts and gathering evidence via data mining across environments. The system uses these results to generate a timeline and attack graph of the incident based on MITRE ATT&CK framework and recommends actions to speed response.
- Accelerated Threat Hunting: Uses open source threat hunting language and federated search capabilities to help threat hunters discover stealthy attacks and indicators of compromise across their environments, without moving data from its original source.
The QRadar Suite leverages open technologies and standards across the portfolio, alongside hundreds of pre-built integrations with IBM Security ecosystem partners. This model enables deeper shared insights and automated actions across third party clouds, point products, and data lakes, which can reduce deployment and integration times from months to days or weeks.
A peek into the new Cisco XDR
Also at the RSA Conference, Cisco offered a glimpse of its upcoming Cisco XDR solution designed to simplify incident investigations and enables SOCs to immediately remediate threats.
Now in beta with general availability set for July 2023, the cloud-first solution applies analytics to prioritise detections and moves the focus from endless investigations to remediating the highest priority incidents with evidence-backed automation.
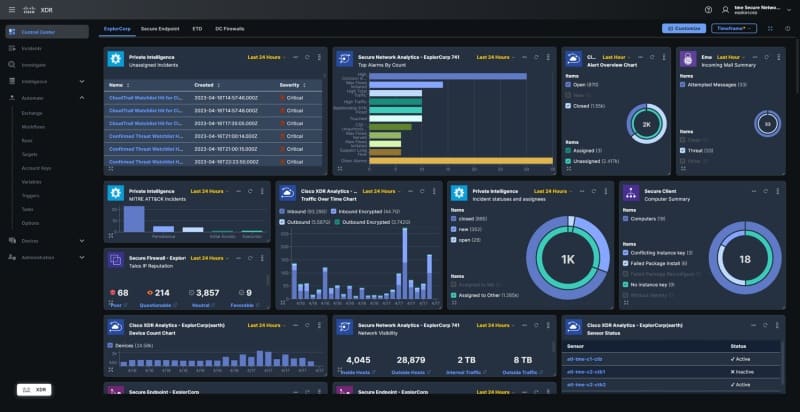
While traditional Security Information and Event Management (SIEM) technology provides management for log-centric data and measures outcomes in days, Cisco XDR focuses on telemetry-centric data and delivers outcomes in minutes.
It natively analyses and correlates the six telemetry sources that SOC operators say are critical for an XDR solution: endpoint, network, firewall, email, identity, and DNS. On the endpoint specifically, Cisco XDR leverages insight from 200 million endpoints with Cisco Secure Client, formerly AnyConnect, to provide process-level visibility of where the endpoint meets the network.

“The threat landscape is complex and evolving. Detection without response is insufficient, while response without detection is impossible. With Cisco XDR, security operations teams can respond and remediate threats before they have a chance to cause significant damage,” said Jeetu Patel, executive vice president and general manager of security and collaboration at Cisco.
In addition to Cisco’s native telemetry, Cisco XDR integrates with leading third-party vendors to share telemetry, increase interoperability, and deliver consistent outcomes regardless of vendor or technology. The initial set of out-of-the-box integrations at general availability include:
- Endpoint Detection and Response (EDR): CrowdStrike Falcon Insight XDR, Cybereason Endpoint Detection and Response, Microsoft Defender for Endpoint, Palo Alto Networks Cortex XDR, SentinelOne Singularity, Trend Vision One
- Email Threat Defense: Microsoft Defender for Office, Proofpoint Email Protection
- Next-Generation Firewall (NGFW): Check Point Quantum, Palo Alto Networks Next-Generation Firewall
- Network Detection and Response (NDR): Darktrace DETECT™ and Darktrace RESPOND™, ExtraHop Reveal(x)
- Security Information and Event Management (SIEM): Microsoft Sentinel




