As National Cybersecurity Month ends, we are reminded of the opportunity to educate businesses on the most effective ways of protecting against ransomware attacks.
The SonicWall mid-year Cyber Threat Report noted a 151% rise in ransomware attack volumes globally in the first half of 2021. This is a wake-up call for businesses of all sizes to not only recognise the threat but to act.
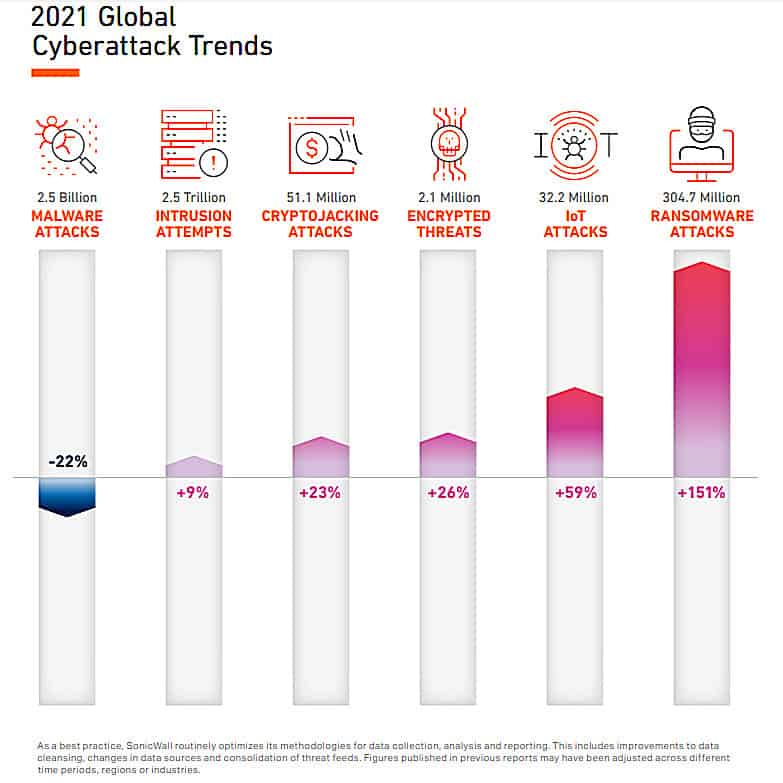
Fortinet’s Global Threat Landscape Report revealed that Hong Kong, as an example, saw over 750,000 ransomware attacks aimed at organisations between April and June 2021.
This puts a huge strain on business leaders and IT teams to keep people and data safe, protected but also recoverable.

In concurring, Joseph Chan, senior regional director, Veeam Hong Kong, Macau & Taiwan says the continued surge of ransomware attacks in Hong Kong poses a great threat on small and large organizations, compelling them to re-evaluate and renew their data protection strategies.
“We believe the first step towards building resilient infrastructure is educating stakeholders and implementing accurate data back-up and protection solution/techniques. Further, devising an effective contingency strategy to mitigate the impact of the threats is equally important,” he added.
The National Institute of Standards and Technology (NIST) has published official best practices for businesses on how to protect data and guarantee business continuity, which Veeam has adopted and will support the implementation of.
Identify
Determine what environments exist which an attack might affect, what risks are associated with those environments, and how this all relates in context with your business goals.
- The human firewall – probing: Technology alone cannot protect your organisation. Everyone must be aware of security risks and understand how to report potential incidents. Evaluate the cybersecurity awareness of your workforce and test them regularly through phishing simulations.
- Plan for business continuity: Outline the processes that are crucial for your organisation’s business continuity such as essential contacts and actions should a disruptive event occur. This plan should be stored in a separate location so that it is immutable and available 24/7/365.
- Tag your digital assets: Identify and tag the assets that are most critical to your organisation so that you can identify and protect them effectively.
Protect
Develop and implement appropriate safeguards to ensure critical infrastructure service delivery by proactively supporting your ability to limit or contain the impact of a cyber-attack.
- Educate your human firewall: Training your staff around cybersecurity is a highly effective way to raise your protection level. This education must take place continuously, with employees receiving updates and new briefings as threats arise whatever their job titles.
- Invest in your digital hygiene: Make sure you’re doing everything in your power to make life harder for malicious actors to ‘infect’ your organisation. This includes creating unique passwords that are updated regularly, using multi-factor authentication, and removing unused devices and applications.
- The 3-2-1-1-0 rule: Keep at least three copies of each piece of important data you have. Store your backup data on two different media types and replicate one copy off-site. Further protection can be achieved through encryption and only using infrastructure that is secure by design.
Detect
The detect function allows for a timely discovery of cybersecurity events and is a critical step to setting up a robust cyber strategy. The faster an event is detected, the faster its repercussions can be mitigated.
- Set up detection systems: The biggest risk is that they may rapidly propagate other systems, so gaining visibility into potential ransomware activity is key. Set up timely alerts when defending against viruses, malware and ransomware.
- Place virtual tripwires: When any suspicious activity is observed virtual tripwires like an unused admin account with alarms tied to it will trigger a red alert instantly.
Respond
The respond function helps users develop techniques to contain the impact of cybersecurity events by ensuring you develop and implement appropriate actions.
- Create an incident response plan: Outline procedures for detecting, communicating, controlling and remediating security incidents so that employees know how to best respond to cybersecurity events when they arise.
- Be calm and accountable: Never blame IT or employees for a breach. It won’t help you respond to the incident and will generate even higher levels of fear and stress. Stay calm and get the right people together to activate the incident response plan as quickly as possible.
Recover
Not all cyber-attacks can be averted, so make sure you have a recovery strategy in place for those moments when your cybersecurity defences have been breached.
- Define your recovery strategy: Prioritise action points that can be used to undertake recovery. Back up your data and make sure backups cannot be accessed by an attacker.
- Design your recovery: Backup systems must be designed with recovery performance in mind, rather than simply focusing on the amount of time the backup will take. Determine what your recovery SLAs are in terms of the RPO and RTO values that are acceptable to you.
“By preparing in advance, you can align to a framework that provides a reliable strategy when operations are disrupted. As well as having a plan, cybersecurity is about creating a culture where all employees are aware of their role in protecting critical data and systems by exercising impeccable digital hygiene,” concluded Rick Vanover, senior director, product strategy at Veeam.




