Imperva claims that new data shows organisations are failing to address the issue of insider threats during a time when the risk is at its greatest.
Commissioned by Imperva, research by Forrester found that 58% of incidents that negatively impacted sensitive data in the last 12 months was caused by insider threats, and 59% of APAC organisations do not prioritise insider threats the way they prioritise external threats.

“This approach is at odds with today’s threat landscape where the risk of malicious insiders has never been higher,” said George Lee, vice president, Asia-Pacific and Japan, Imperva.
He added that the rapid shift to remote working means many employees are now outside the typical security controls that organisations employ, making it harder to detect and prevent insider threats.
“Further, ‘The Great Resignation’ is creating an environment where there is a higher risk of employees stealing data. This data could be stolen intentionally by people looking to help themselves in future employment, or it could be taken inadvertently when an employee leaves the organisation,” he opined.
Not prioritising insider threats
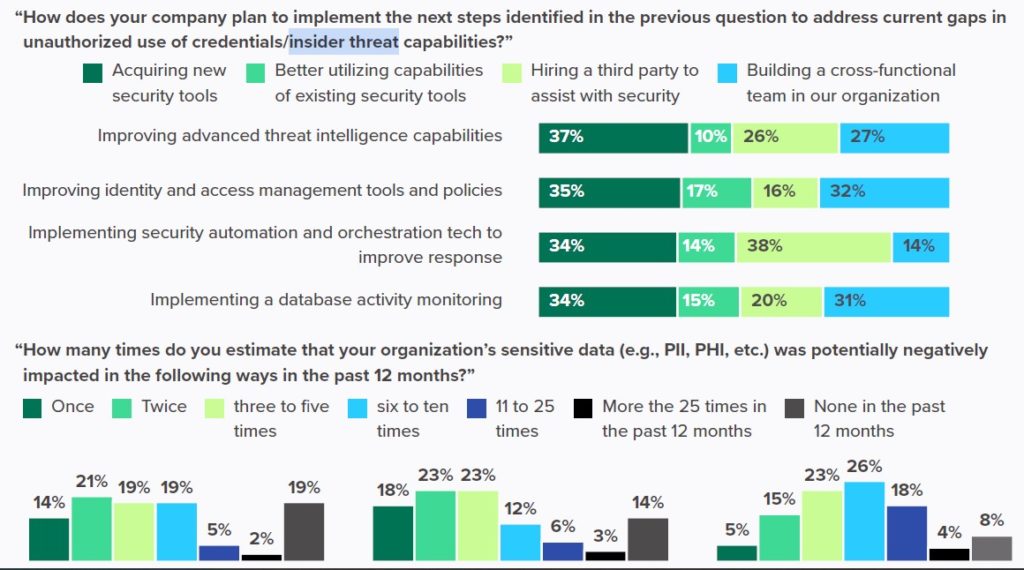
About 41% of APAC respondents blame lack of budget and internal expertise (38%), but other problems abound. Another 33% of firms do not perceive insiders as a substantial threat, and 24% say their organisational indifference to insider threats is due to internal blockers such as a lack of executive sponsorship.
In fact, 74% of APAC organisations do not have an insider risk management strategy or policy, and 70% do not have a dedicated insider threat team.
The findings show that organisations are woefully underestimating the seriousness of insider threats. Previous analysis by Imperva into the biggest data breaches of the last five years found 24% of these were caused by human error (defined as the accidental or malicious use of credentials for fraud, theft, ransom or data loss) or compromised credentials.
APAC firms are prioritising external threats over insider threats, even though insider events occur more often. Insider threats are hard to detect because internal users have legitimate access to critical systems, making them invisible to traditional security solutions like firewalls and intrusion detection systems.
“This lack of visibility is a significant risk to the security of an organisation's data. That is why leaders need to focus on the potential threats lurking within their own network,” added Lee.
The main strategies currently being used by APAC organisations to protect against insider threats and unauthorised usage of credentials are encryption (54%) and periodical manual monitoring/auditing of employee activity (44%).
Many are also training employees to ensure they comply with data protection/data loss prevention policies (57%). Despite these efforts, breaches and other data security incidents are still occurring and 55% of respondents said that end users have devised ways to circumvent their data protection policies.
Enhance insider protection
Organisations looking to better protect against insider threats should take the following steps:
Gain stakeholders’ buy-in to invest in an insider risk program. Insider risk is a human problem, not a technology issue, and must be treated as such. It is also a risk that cuts across all parts of the business. It is important to get senior executives from across the company to endorse and support the insider risk program for it to be successful.
Follow Zero Trust principles to address insider risk. Following a Zero Trust approach helps protect data and users while limiting the ability of insiders to use sensitive resources not required by their function.
Build a dedicated function to address insider risk. Since insider risk is a human problem and very sensitive in nature, it requires dedicated resources. These may be part of the security team or, better yet, a separate dedicated function.
Create processes for your insider risk program and follow them. The sensitivity of insider risk and its associated privacy concerns require that strict policies are implemented and followed. Treat every investigation as if it will end up in court and apply policies consistently.
Implement a comprehensive data security strategy. An all-encompassing approach goes beyond data loss prevention (DLP) to include monitoring, advanced analytics, and automated response to prevent unauthorised, accidental, or malicious data access. The technologies you deploy should support the processes you have created and the mandate for your insider risk function.




