Public Key Infrastructure (PKI) is a process of authorizing data sharing or transactions between sender and receiver by providing protection with public and private keys that are approved by central authorities with the help of digital certificates.
The foundations of PKI came out in 1976 when Whitfield Diffie and Martin Hellman published a method of securely exchanging cryptographic keys over a public channel. Fast forward to 45 years later, is PKI still relevant?
It might seem so given that MarketsandResearch forecasts the PKI market to grow to US$9.8 billion by 2026, up from US$3.9 billion in 2021.
The major driving factors contributing to the high growth rate of the PKI market include an increasing adoption rate of PKI solutions and services, the increasing trust in online sellers and customers, increasing instances of malware and file-based attacks, rising concerns pertaining to loss of critical data, the surge in the adoption of IoT and cloud trends, and stringent mandatory regulations and compliances.

In an exclusive with FutureCIO, Brian Trzupek, senior vice president of Product at DigiCert, revisits the evolution of PKI use in modern times.
What is PKI automation?
Brian Trzupek: As organisations move towards digital transformation, the more they rely on PKI and digital certificates to ensure trust and protect sensitive data. But managing PKI is quickly becoming impossible to do manually and more companies are looking at automating their PKI management.
PKI automation describes the range of processes and tools to manage PKI certificates and key life cycles that reduce the need for human intervention. The main objective is to minimise the monotonous tasks related to managing digital certificates, reducing human error, and freeing teams to focus on higher-level activities.
Some aspects that can be automated are certificate request, renewal, validation, alerts or revocation, allowing companies to simplify their PKI security, reduce costs and save time. Essentially, PKI automation looks to automate and improve the efficiency of certificate management workflows at key points during the certificate lifecycle.
In the context of cybersecurity, why would I need PKI automation, where is it applied?
Brian Trzupek: A typical enterprise in APAC is currently managing over 40,000 security certificates, according to DigiCert's report, 2021 State of PKI Automation. This is a sharp increase from previous years, and there is evidence that this rise comes with its share of cybersecurity risks including data breaches, non-compliance issues and service outages.
Two-thirds of these enterprises have experienced outages caused by certificates expiring unexpectedly, and 35% experienced five to six such outages in the past six months, according to data from the survey.
This may result in organisations being faced with reputational damage as well as an impact on customer trust and relationships, as well as revenue. PKI automation, thus, helps to reduce the likelihood of cyber-attacks by bolstering security systems against threats.
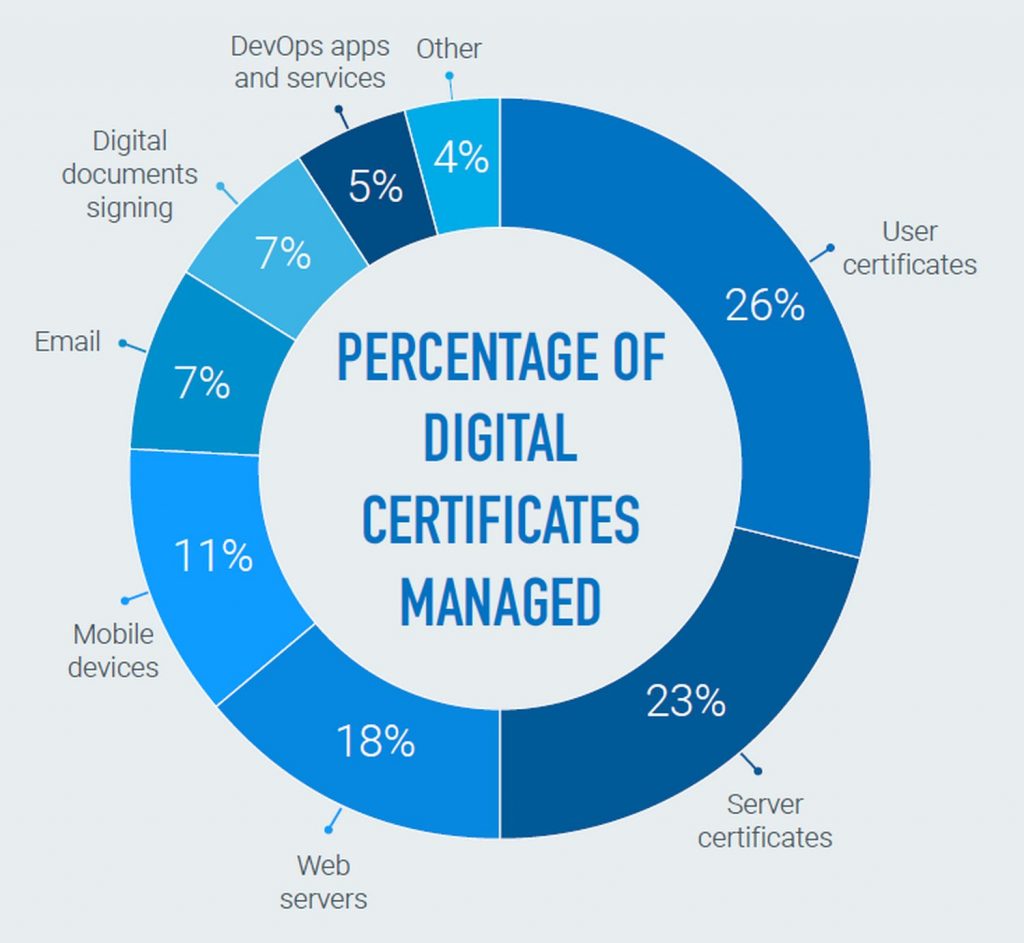
PKI automation can be applied to all use cases in which PKI is used including web servers, server certificates, user certificates, mobile devices, email, digital documents signing as well as DevOps apps and services.
Maybe this is repeating from #2, but can you name some use cases for PKI automation applicable to Asia?
Brian Trzupek: Within Asia, business continues to move online, whether it be banking, real estate, remote working accelerated by the pandemic, or the growth of smart devices often referred to as the Internet of Things (IoT).
According to a new McKinsey Global Survey of executives, companies in Asia have accelerated the digitisation of customer interactions by four years, and the share of products and services that are digital in nature by over ten years, over the course of the Covid-19 pandemic.
This acceleration outpaces the global average of three years and seven years respectively. Digital transformation is happening in Asia and is leading to digital-first business processes.
Everything from employees accessing the corporate network and associated applications such as sales systems, customer information and work email requires authentication and encryption that PKI can provide. Similarly, a unique digital certificate is required for each user, each client, each IoT device (business or consumer).
A unique code signing certificate should be used for each software code commit during the testing and build process, prior to and at production, for any company building or integrating software into its digital services.
IoT devices use code signing certificates as well to prevent unauthorized or malicious code from running on the device or corrupting it. PKI digital certificates also authenticate devices to the network and can be inserted upon device manufacturing to provide a “device birth certificate.”
For email, digital certificates allow emails to be signed and associated with each user in the network to prevent spoofs.
In many of these enterprise use cases, digital certificates can be automated to interact with IT team policy and automatically deploy while providing visibility into important certificate management milestones, such as renewal and revocation. This can help prevent certificate expiration that may shut down online services.
Automated PKI management can play a key role in avoiding the negative consequences of certificate failures while providing actionable intelligence to organization security teams to manage effectively.
What are the top 3 misconceptions around automating PKI certificate lifecycle management?
Brian Trzupek: Firstly, some IT leaders believe that PKI management does not provide value as they view it as a back-support and administrative tool with minimal impact.
However, digital transformation has caused PKI to come to the forefront as it acts as a cornerstone for websites, servers, applications as well as upcoming technologies like IT.
Organisations are, thus, increasingly using PKI management strategically so that their security systems are scalable and able to support them in the future.
Next, many take an “if it ain’t broke don’t fix” approach to PKI management, thinking that manual PKI certificate lifecycle management is working for them.
However, in an increasingly complex certificate ecosystem, manual PKI management brings many dangers as the scale and complexity of keeping certificates secure can quickly take a toll on IT departments. For example, an IT team can easily miss an expired certificate leading to time-consuming repairs and potential outages.
Finally, some believe that PKI automation is an overly complicated process that is not worth the effort or worry about unintentional security concerns brought about by automation.
Are all PKI automation tools equal?
Brian Trzupek: Not all PKI automation tools are equal as providers offer different features and proprietary technologies that aim to simplify and improve systems and processes. Organisations should, thus, choose PKI automation tools that best address their challenges and concerns.
Many organisations are looking for centralisation with certificate issuance and management available from the same provider.
Some features not included by all providers include IP-Based Scanning, APIs, remote management of load balancers and scheduling capabilities that could also act as a differentiating factor.
Checklist of things to evaluate PKI automation tools and services against?
Brian Trzupek: In general, organisations should look for tools and services that automate tasks that are repetitive, manual, have high volume, are time-sensitive and are prone to human error:
- Renewing or requesting new certificates to save time and stress on this tedious process.
- Validation and approval processes can be automated so that all future certificate issuance and renewals can be done almost immediately.
- Alerts for certain events, so that IT teams are kept posted on important certificate management activities.
- Once an issue is encountered, the renewal and installation to resolve the issues quickly and efficiently should also be automated.
- Finally, using a code signing manager, development teams can automate code signing with built-in API integration to pre-plan and approve signature windows for secure releases and updates.
With all these points checked and ready, organisations can be sure that their automation tools are robust and comprehensive.
However, it is also important to know what not to automate. We don’t recommend automating tasks that require human intervention and key decision makings, such as customer support, tasks that have low ROI or complex processes that need to pass through multiple approval levels and decision-making.




