Gartner Sr director analyst Richard Addiscott says business leaders now widely accept that cybersecurity risk is a top business risk to manage – not a technology problem to solve. "Supporting and accelerating business outcomes is a core cybersecurity priority, yet remains a top challenge," he continued.
In the Deloitte report, 2023 Global Future of Cyber Survey, Allan Cockriel, group CIO/CISO for Shell observes a more significant focus on cybersecurity as an enterprise business risk. He goes on to add that "across the organisation, there is a significant shift in partnership in viewing cybersecurity as a core ingredient of our transformation and not a side garnish or afterthought."
Gartner says security leaders must rethink their balance of investments across technology and human-centric elements when creating and implementing cybersecurity programs in line with nine top industry trends.
Trending: Observability
Alvin Tan, regional vice president, Tanium noted that the escalating threats and breaches of recent years are paving the way for the realisation of a need to converge IT observability and cybersecurity.
He explains that observability, in this case, uses 3 types of data – metrics, logs and traces - to provide deep visibility. He opines that observability allows organisations to fully see, understand and manage their systems.
Tan acknowledges that achieving observability is hampered by infrastructure complexity.
"Observability is a lagging indicator even as we try to speed up cyber security insights with automation. By the time we gather the metrics, logs and traces into a data lake, we are already behind the attack. We should be looking for real-time capabilities that shorten our time to security," he explains.
A better way for unified endpoint management
A study by the Ponemon Institute found attacks on endpoints to be some of the most prevalent that respondents had experienced, with 81% of businesses experiencing an attack involving some form of malware, and 28% experiencing attacks involving compromised or stolen devices.
Tan acknowledges that organisations struggle with managing endpoints. Many are unable to deal with employee flux, new endpoint assets, and old ones that need to be decommissioned. The mass move to remote work may have exacerbated security measures.
He opines that unmanaged and orphaned endpoints present the biggest risk to an organisation as they are the ones that are non-compliant and unpatched. "When breached, the gap remains undetected for a long time since they are not under management," he added.
Gartner defines unified endpoint management (UEM) as a tool that provides agent and agentless management of computers and mobile devices through a single console.
"A UEM is the latest buzzword to articulate the need for a single management interface to scalable, speedy and secure communications architecture with each and every endpoint, to manage and secure them as required, wherever they may be," he elaborates.
Tan believes there is a need to consolidate the many agents into a single agent to achieve a quick boot time and enhance productivity. (* editor's note, click on the PodChat for a deeper insight by Tan on UEM)
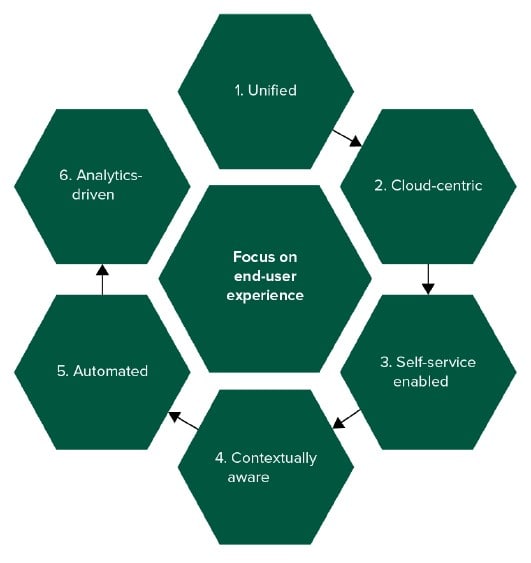
In The Future of Endpoint Management report, Forrester noted that the transition to remote work during the pandemic has accelerated the move to modern endpoint management, which the firm says holds six characteristics (see Figure 1).
Figure 1: Modern Endpoint Management leverages six core principles
The need for real-time security
One of the outcomes of the digital economy is the desire of customers for instant gratification – to get responses in real time. This expectation is trickling into workflow as organisations employ technologies like automation, artificial intelligence and analytics to achieve deeper levels of customer engagement.
The unintended consequence of this is complexity – which strains an organisation's ability to adapt existing security frameworks, for example, to reflect more accurately what is acknowledged as a more virulent criminal community (see the World Economic Forum report, Global Cybersecurity Outlook 2023).
Tan cites just one area of increased vulnerability – endpoints. He opines that many organisations are unable to say how many endpoints they have with accuracy.
"So, when a zero-day vulnerability like Print Nightmare emerges, it may take them many days to find the offending endpoints," he posits. He recalled that when a software library vulnerability Log4J emerged, large organisations he spoke with took over four months to address the vulnerability, and many were unable to confirm whether they still had the library in their systems.
Tan stressed the traditional way of gathering data into a log or data lake is far too slow and presents many downsides to really understanding your organisation’s posture vis-à-vis an emerging threat.

"We need real-time visibility of all our assets and software libraries. We also need real-time knowledge of our level of cyber hygiene. We need real-time knowledge of our systems when a zero-day vulnerability emerges or when we discover a breach, and we need real-time capabilities to respond rapidly to an incident. Real-time knowledge gives us heightened situational awareness."
Alvin Tan
"Real-time capability is the only way you can gain certainty," he concluded.
Click on the PodChat player and hear Tan elaborate on the need for a unified endpoint management approach to improving an organisation's resilience post-pandemic.
- Can you briefly describe for us what is Tanium?
- What is observability from the perspective of the CIO/CISO as it relates to security? Where do these roles converge (and diverge) on the topic?
- Define endpoint protection in the context of the hybrid way of work.
- What is unified endpoint management, and where does it sit in the technology stack?
- How does UEM help an organisation meet its resilience goals post-pandemic?
- What are the proven steps to modernising endpoint management strategies?
- How effective/reliable is real-time security?
- Given the evolving nature of threats and the security solutions to tackle these, how can CISOs/CIOs optimise their approaches to security?




