Ransomware remains one of the more dreaded cyber threats of the decade. But for a ransomware attack to be initiated, the attacker must first have your credentials. One such enabler of ransomware operations is infostealers.
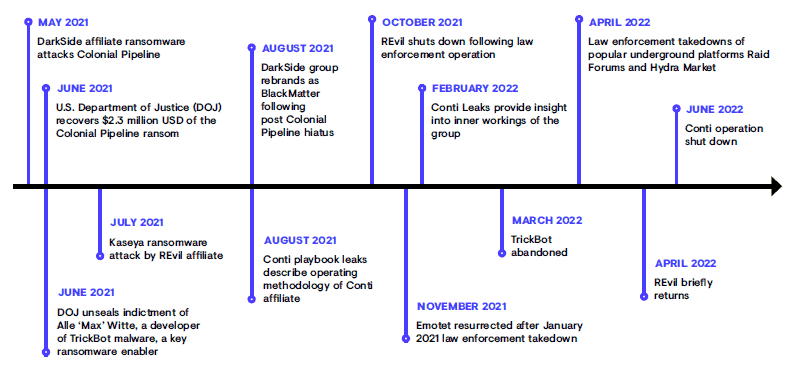
Source: Secureworks
According to Secureworks Counter Threat Unit researchers, on a single day in June 2022, over two million credentials obtained by infostealers were available for sale on just one underground marketplace. Check Point estimates that up to 21% of malware worldwide is made up of infostealers.
Alex Tilley, head of intelligence research for Asia-Pacific at Secureworks, warns that infostealers are full-featured spying toolkits in as much as they can do anything that they want on your machine.
“Once they are installed, they are very insidious. And because they've been around since 2006, they are very mature and very good at what they do in taking your information,” he added.
He opined that Asia-Pacific appears to be a ‘testing bed’ for new types of attacks. He also observed that while the early infostealers were called banking trojans, these have since moved to other industries partly as banks and regulators have become more aggressive in protecting their processes.
Mining old stolen data
Accenture’s Cyber Threat Intelligence team (ACTI) noted a marked increase in the number of logs for sale from July to October 2022.

Source: Accenture 2022
ACTI reports that in 2022, the high-profile breaches of several large organisations illustrated the ease at which threat actors can breach network defences using stolen employee credentials and leveraging MFA fatigue attacks.
Tilley laments that there remains stolen data from the last 15 years ‘sitting out there.’ He argues that cybercriminals are revisiting these old stolen data, including passwords, to identify which can be used to infiltrate company networks.
“Unfortunately, oftentimes it works because that stolen credential hasn't been changed in 15 years, or five years or two years,” laments Tilley.
Situations when VPNs don’t work
Virtual private network (VPN) usage got a boost in 2020 as organisations instituted work-from-home processes in a bid to normalise operations following government-mandated lockdowns. Statista estimates the VPN market globally at US$44.6 billion, up 75% from 2019, and forecasts this to rise to US$77.1 billion in 2026.
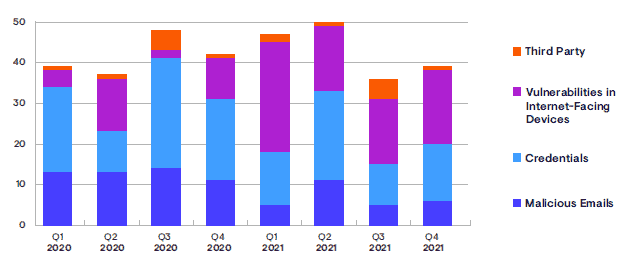
Source: Secureworks
Tilley opined that VPNs alone are not sufficient to protect an organisation’s network from hackers trying to get in, particularly if passwords are stolen. A stolen password can be used to access a network even if s VPN is being used to access the network. However, using multi-factor authentication can stop access to the corporate network even if a stolen password is being used to enter the network.
He believes that MFA should be on the top of a CISO or CIO’s priority list.
The job of security professionals
Asked whether the adoption of FIDO2, passwordless and passkeys help in the fight against Infostealers, Tilley concedes that it is inevitable that sometime in the future, criminals will find a way to circumvent these developments.

“That doesn't mean that we shouldn't move towards these more secure (solutions). Security is always a balancing game between functionality and security. Our job is to enable the business to operate. What we must never do, I think is, as part of this discussion is, we must never say, we're done."
Alex Tilley
Acknowledging that developments and threats will continue to evolve, he concedes that security is a never-ending game.
CISOs and CIOs working together in 2023
In the realm of security, visibility is important. “If you can’t see the threat, you can’t deal with it,” stated Tilley.
“Infostealers do not exist in a bubble. There is always something around them that you can see – be it the way it was delivered, be it the attack tool that was used to put it into your network, be it the abnormal user login activity – if you've got a user in Laos, and suddenly, they are logging in a German time zone,” he suggested.
He supports the deployment of endpoint protection solutions as these provide some visibility. However, he cautioned reminded that other things will occur at the same time as that Infostealers are being delivered and we can see those, and we just need to act on those.
What lies ahead in 2023
Ransomware attacks are moving beyond just preventing access to data and networks and have moved into the realm of extortion using the content of the data – corporate secrets that need to be kept secret.
“It is still using those same techniques of access into networks, using infostealers and other penetration tools, to get access to your network to find those juicy bits of data to steal, and then holding you to your feet, to the fire, as it were. I think that might be big,” concluded Tilley.
Click on the PodChat player more about how organisations can combat the rise of infostealers.
- What is infostealer malware? How does it work?
- Are infostealers prevalent in Asia? What are the motivations? Any difference between the types of infostealer malware used in Asia compared to elsewhere?
- How do infostealers work? In what situations (in Asia) are infostealers more successful in this region?
- We’ve noted the rise in the use of VPNs during the pandemic. Will the use of VPN lessen the threat of infostealers?
- The increase of MFA and VPNs aside, what are the misconceptions among CISOs, security professionals and users when it comes to combating infostealers?
- Will the adoption of FIDO2 and passwordless or passkeys help in the fight against infostealers? Do you anticipate cybercriminals finding ways around these?
- Coming into 2023, what strategies will work best against infostealers? How should CISOs work with CIOs and the rest of the organisation to better secure the business against infostealers?
- Closing our PodChat, what are your expectations for 2023?




