Security threats will further disrupt the smart device market in 2021. Product leaders must strengthen their strategy by addressing security and privacy. Safety, security, privacy, and user control are foundational to digital device manufacturing. The amount of information being transmitted from things continues to rise.
But smart device manufacturers must pay closer attention to securing these devices, with an array of emerging security technology like Microsoft Azure (Sphere), Vdoo, Satelles and Entrust connected device security solutions.
Most sensor-based things have minimal computing resources, and the opportunities for antivirus, encryption, and other forms of protection within things are more restricted. Therefore, IoT security products with a variety of capabilities have emerged to help address some of these challenges.
Adapting to the changing landscape requires digital device manufacturers to address the 4 Ws: who, what when, and where.
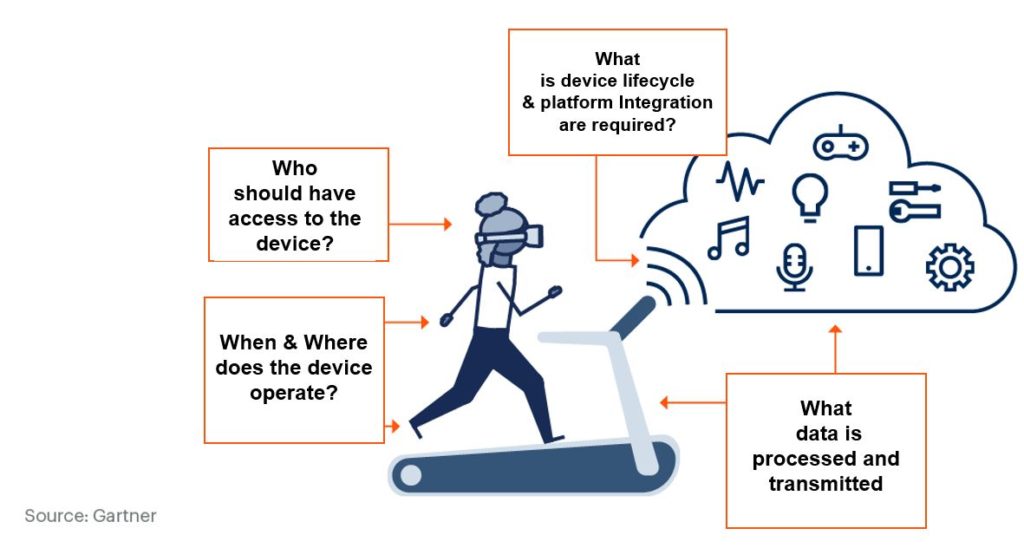
Architecting for the full life cycle management of a device and its security and privacy requirements must address these concerns as a starting point. This would entail adopting several technology solutions.
Recommendations for Smart Device Product Leaders
Product security officers and product leaders must adopt the following solutions:
1. Who: Identity and Access Management Solutions
Passwords have persisted primarily because they are free and highly ubiquitous in many enterprise systems. However, passwords have long been proven less secure. Issues such as poor memorability of passwords, weak or reused passwords, password storage, phishing, social engineering, and brute-force attacks persist with the use of passwords. The options for passwordless authentication are as follows:
Single-factor authentication:
- Phone-as-a-token
- FIDO2
- Other kinds of knowledge
- Biometric authentication
Multifactor authentication:
- Pin-protected SIM cards
- Biometric-enabled smart cards
- Step-by-step mobile push
- Windows Hello for Business
- FIDO2
Zero-factor authentication (CARTA underlay):
- Analytics consuming a range of familiarity signals
- Rule-based evaluation of networks, locations, signals, and devices
Sample Providers:
- BIOKey, Cisco, Google, Microsoft, Thales (acquired Gemalto), Xyntek
2 & 3. When and Where: Positioning, Navigation, and Timing (PNT) Security
Yes, two and three go together in the world of smart devices and IoT. Understanding when and where smart devices are operating and securing their location and time in a cyber-physical world is imperative. Unfortunately, PNT security is an increasing concern. Although illegal, jammers can use a transmitter to interfere with GPS signals and scramble or alter location and time. They can be stationary or mobile (car or drone). While they used to cost thousands of dollars, some can now be bought for less than $100. Fake GPS location apps are freely available in app stores. On the spoofing front, attacks are also on the rise, with a number of incidents being reported globally. Concerns are growing to the point in which an Executive Order on strengthening national resilience through PNT services was signed last February 12, 2020 in the US.
Sample Providers:
- Booz Allen Hamilton, ENSCO, Orolia, Satelles
4. What: Device Management, Data Security, and Platform Integration
Addressing the question of what is being protected may implore various technologies to achieve device management, platform integration, and data protection. Smart devices and IoT product strategy must include the following:
- Embedded trust device identity and key/credential management vendors that offer IoT-scale-federated and secure device management implementations.
- Moving target defence (MTD) is a technology in which dynamic or static permutations, morphing, transformations, or obfuscations are used to thwart attacker exploitation techniques. MTD continually shifts the configuration of the underlying system, thereby reducing the success rate of an advanced cyberattack.
- Device security management includes embedded protection, compliance validation operations monitoring, and patching via over-the-air device-to-cloud communication and threat detection.
Sample Providers:
- Embedded Trust: Mocana, Trustonic, Prove & Run, Thales Group, Crypta Labs, Infineon Technologies AG
- MTD: Morphisec, RunSafe Security, TrapX Security
- Device Security Management: Vdoo, Microsoft Azure (Sphere), Entrust
First published on Gartner Blog Network




