Ransomware attacks continue to skyrocket and pose serious financial and legal issues to organisations in Asia Pacific. When fallen prey to such attacks, most enterprises would choose to pay the ransom. However, supporting the attackers’ business model by paying the ransom only encourages ongoing criminal activity and will only lead to more ransomware attacks subsequently.
Ransom payments could also lead to further regulatory risk to the targeted organisation as paying ransom could be construed as illegal. Paying the ransom is aiding and funding criminal activity.
The regulatory landscape in Asia Pacific
In Hong Kong, even though there is currently no cybersecurity legislation prohibiting the payment of ransom, such payments could be considered a violation under section 25 of the Organised and Serious Crimes Ordinance. Organisations in regulated industries, such as financial institutions, are mandated to notify the regulators in Hong Kong of a major cyber incident. The Privacy Commissioner in Hong Kong also encourages companies to self-report and notify affected customers.
In other parts of Asia, Singapore for instance, payments to ransomware attackers could violate the Corruption, Drug Trafficking and Other Serious Crimes (Confiscation of Benefits) Act, or CDSA, which criminalises assisting another person to retain, control or use the benefits of criminal conduct. Payments to sanctioned entities could also violate Singapore sanctions laws.
In Australia, the Minister for Home Affairs intends to introduce new legislation this year that mandates the reporting of ransomware attacks and makes making ransomware payments illegal.
Support executives on decision making
It has never been more important for security teams to work with executives to ensure they make the business decisions necessary to prevent ransomware attacks.
The more they understand the risks, the better prepared they will be when making a decision and justify it in the face of scrutiny.
If the organisation does get hit, there will be fewer surprises if the problem is visible across the organisation. This will enable swift actions in the response, including in making a decision as to whether the organisation should pay or not.
Focus on eliminating risks and attack surface
In conjunction with supporting and preparing executives, it’s time to get the house in order now rather than wait for legislation to mandate it, or more importantly, be attacked.
While every metric and trend indicate that enterprises continue to add more security tools, successful attacks continue.
Many organisations simply focus defences on detection and response, which does help to reduce damage from attacks, but it does not prevent them from happening in the first place. Adding more tools simply isn’t the answer to a strong defence.
Unpatched vulnerabilities, device misconfigurations, unmanaged or unknown internet-facing assets and unauthorised software rank consistently among the top attack vectors for ransomware.
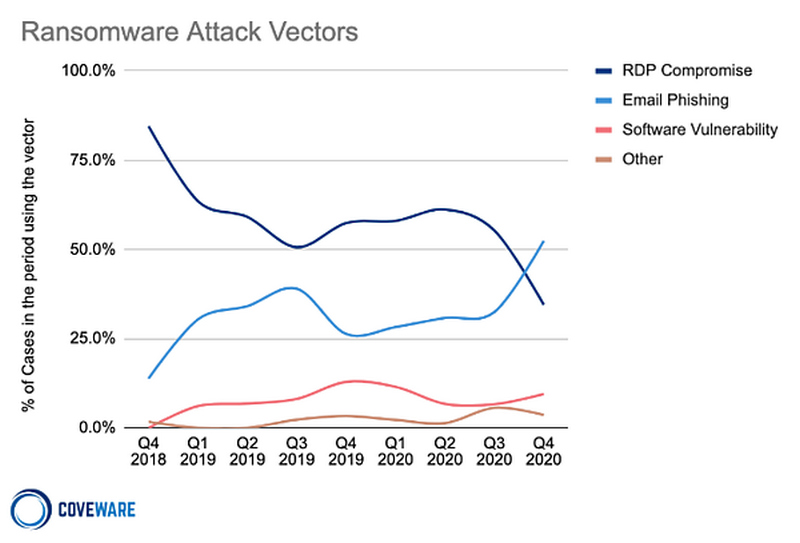
Source: Coveware 2020
While there’s no silver bullet to prevent ransomware, security teams must focus on eliminating any area of risk and shrinking their attack surface.
This includes knowing blind spots. It’s paramount to have visibility into every data asset in the environment including unmanaged assets appearing on the network, inventory all hardware and software and classify and tag critical assets.
Solid cybersecurity hygiene, patching for known ransomware vulnerabilities, applying needed configuration changes and adjusting security policies are a few important steps towards ransomware prevention.
Some other best practices to prevent business interruption from a ransomware attack include:
- Enforce password policies
- Employ best practices for the use of remote desktop protocol, such as applying multifactor authentication
- Employ network security and firewalls
- Enforce account use policies, such as assigning least privileges to users
- Keep software updated
Organisations will find themselves in a good position to avoid becoming a victim by getting the house in order and working with executives to ensure they are making the business decisions necessary to prepare for a potential ransomware attack.





