You can't do business without your vendors. They support critical elements of your organization, from cloud storage services to payment processing to physical items like office supplies or physical components. Your vendors make your organization run more efficiently – but sometimes at a risk to your financial, reputational and operational resiliency.
Cybercriminals are increasingly targeting third parties and suppliers in the hopes of breaching their clients. Unfortunately, it’s working: according to EY, 36% of organizations have had a data breach caused by third parties (like vendors) in the past few years.
Breaches caused by third-party vendors can negatively impact your financial health; according to Ponemon, the cost of a data breach ticks upward when a vendor is involved (for example, if an attacker exploits a vulnerability in third-party software to get to your data). Those breaches involving a third-party vendor cost an average of $4.33 million.
For this reason, vetting your vendors is critical. The due diligence process, however, can be both tedious and time-consuming for you and the vendor. Questionnaires vary in-depth, and you may not get the accurate answers you need to gain visibility into third-party risk. This is where security ratings are a huge advantage to help validate a vendor’s security posture.
What are security ratings?
Security ratings are a score that provides you with an at-a-glance assessment of an organization’s cybersecurity risk using data-driven, continuously evolving metrics. Security scores (such as SecurityScorecard’s ratings) are the average of several risk-factor scores that provide visibility into an organization’s information security control weaknesses in addition to potential vulnerabilities throughout the digital supply chain.
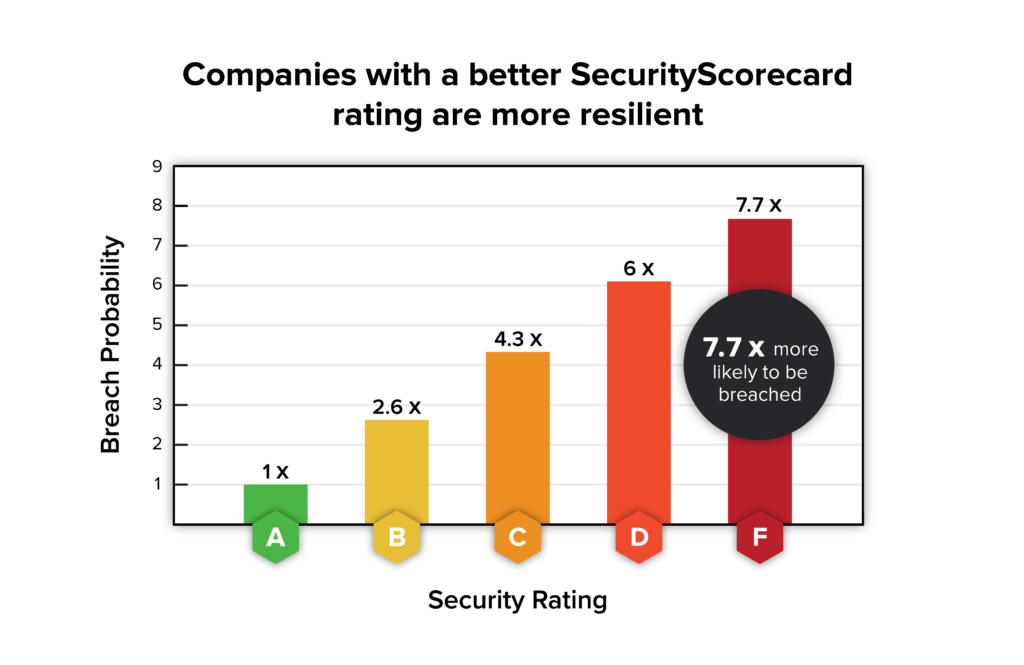
By looking at the breakdown of security ratings, you can see information about an organization’s security practices – for example, how often they patch software vulnerabilities and whether their endpoints are secure.
Security ratings are compiled by platforms that scan the internet for possible control weaknesses, often employing technologies like the ones that cybercriminals use. Unlike cyber criminals, security ratings platforms alert your IT staff to the control weaknesses and suggest remediation actions to mitigate the risk.
While many organizations use security ratings to monitor their own vulnerabilities, they are also extremely useful for monitoring the security posture of active and potential vendors.
Improve vendor due diligence with security ratings
Third-party risk management, or TPRM, is the process of vetting your vendors to understand the risk they may pose to your organization and your supply chain. Organizations with strong vendor risk management programs systematically identify, assess and mitigate threats to their assets and data that might be caused by the organization's supply chain.
Traditional risk management programs use questionnaires and other static methods of assessing a vendor’s risk. Security ratings can improve this process in a few key ways:
1. Ratings automate the due diligence process
Due diligence can be a huge drain on internal resources; large organizations can have hundreds or even thousands of third parties. In fact, Gartner found that 60% of organizations work with more than 1,000 third parties.
That’s a lot to keep track of with the same level of attention, particularly for organizations that use spreadsheets and other manual tools to track vendor risk. A manual process that takes a lot of time and, as with any other manual data-entry process, can be prone to human error.
Security ratings are automated tools that reduce busywork by offering a way to easily monitor vendors without having to manually create questionnaires, hunt down information or update spreadsheets.
2. Ratings collect consistent data
Often, when presented with a questionnaire, third parties may answer a question in different ways. Some might answer yes or no, some might attach a screenshot, and some may simply copy and paste what they answered on the last 10 questionnaires.
Discrepancies in the provided data make it difficult to understand because you won’t be comparing apples to apples – vendors vary in their level of importance to the organization and in their security levels. A tool cannot automatically process all those different kinds of data — instead, someone will have to manually review it.
Ratings, however, always collect the same kind of data, structured in the same way, so you can easily compare scores — whether you’re comparing two vendors, or seeing how the same vendor’s security posture has changed recently.
3. Easily compare vendors
Comparing your potential vendors’ security postures is simple when using ratings. At a glance, you’ll be able to see which third parties present the biggest risks to your organization, and assign a risk rating of high, medium, or low. These criticality ratings can help your organization target resources for the vendors that merit the most attention.
4. Trust but verify
When assessing your third parties with questionnaires, you must take your vendor’s word that the questionnaire is accurate. While you don’t need to assume that your vendors are lying to you, know that the information used by security ratings platforms allows you to gain an accurate, up-to-date, external view of security. Take a “trust but verify” approach to objectively assess vendors in your due diligence processes.
5. Monitor continuously
Questionnaires and surveys are static tools that can only capture a vendor’s security at one point in time. They provide snapshots of their security posture but rarely give the full picture. A vendor may be secure today but fall out of compliance tomorrow.
Ratings providers, however, monitor your vendors continuously; you’ll receive a notification whenever a vendor falls out of compliance, and be able to scan for problems the vendor might not know about, like an Amazon Web Services bucket that has been misconfigured, chatter on the dark web about breached assets, or other undetected vulnerabilities. Pairing security ratings with an automated TPRM solution enables you to make these data-driven decisions about risk more efficiently.
How can SecurityScorecard and ProcessUnity help?
While it’s impossible to eliminate risk entirely, you can proactively manage risk by staying aware of your vendors’ security controls. To reduce the resources expended managing third-party relationships, consider an intelligent tool that automates your organization’s third-party management process.
SecurityScorecard enables organizations to drive a scalable and automated third-party risk management program. SecurityScorecard is the only omni-directional security ratings provider of cyber risk ratings, questionnaires, a marketplace of integrations and attack surface intelligence.
By leveraging ProcessUnity Vendor Risk Management, your organization can integrate security ratings into an automated third-party risk management platform. ProcessUnity’s pre-built connector embeds SecurityScorecard’s overall security risk rating and individual factor scores into the solution.
This integration lets you view risk-related information in one centralized location without having to manually enter data, continually update information, or move back and forth between your security rating solution and third-party risk management platform.
First published on SecurityScorecard blog




