Domain-based Message Authentication, Reporting & Conformance or DMARC is an email validation protocol designed to protect domain names from being misused by cybercriminals, authenticate the sender’s identity before allowing the message to reach its intended designation.
It verifies that the purported domain of the sender has not been impersonated and relies on the established DKIM (DomainKeys Identified Mail) and SPF (Sender Policy Framework) standards to ensure the email is not spoofing the trusted domain.
Increased risk of email fraud
Security vendor Proofpoint claims that 50% of the top 30 companies listed on the Singapore Exchange (SGX) and tracked under the Straits Times Index (STI30) are not taking proactive steps to protect their customers, partners and employees from mail spoofing techniques used in phishing, business email compromise (BEC) and other email-based attacks.
Proofpoint says it looked at the level of protection against the STI30 companies’ domain names and found that half of them have not published a DMARC record, making them susceptible to cybercriminals spoofing their identity and increasing the risk of email fraud targeting users.
Only one of the STI30 companies observed have implemented the recommended (strictest) deployment that blocks malicious emails from reaching intended targets. This means 97% of Singapore's largest companies are not using established best practices for email security and authentication and are therefore more susceptible to identity deception attacks.
Unnecessary risk
In an era where hybrid work is on the rise, and email communication with suppliers, resellers, employees, and customers is business-critical, this gap represents a prime opportunity for cybercriminals to launch social engineering attacks pretending to come from known brands.
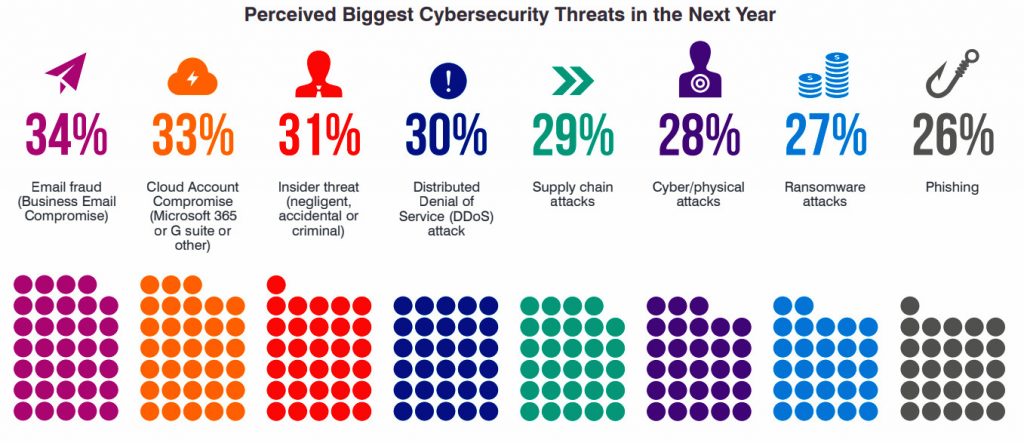
Proofpoint’s 2021 Voice of the CISO Report that surveyed 1,400 CISOs from around the world revealed that 44% of surveyed CISOs in Singapore indicated that they were at risk of suffering a material cyber attack in the next 12 months, with Business Email Compromise emerging as the number one concern.
Yet, organisational cyber preparedness continues to remain a major concern more than 18 months into a pandemic that has permanently reshaped the threat landscape. According to the report, only 40% of Singapore’s CISOs polled said that they have strengthened their security posture to better support remote working.

Alex Lei, senior vice president, APJ at Proofpoint says, “Email continues to be the number one threat vector, with over 90% of targeted cyberattacks starting with email. With firms adopting hybrid work arrangements, securing this vector has never been more important.”
He opined that companies that have not implemented email authentication best practices may be unknowingly exposing themselves to cybercriminals aiming to capitalise on intricate supply chains and potentially tricking critical stakeholders with fraudulent emails.
“We recommend implementing robust email defences and inbound threat blocking capabilities that include deploying DMARC email authentication protocols, combined with cybersecurity awareness programs that train users to spot and report malicious emails,” he continued.

Maiwand Youssofzay, country manager for South Asia and Korea at Proofpoint added: “DMARC requires deep expertise to successfully implement as well as significant time and resources to gain knowledge of how email authentication works.”
Does this suggest incompetence or ignorance on the part of those not implementing DMARC, particularly those that seek public funds to support their business?




