Gaming research firm, Newzoo, forecasts the 2020 global games market will generate revenues of $159.3 billion with 2.7 billion gamers globally.
According to ACI Worldwide, online gaming transactions saw a 97% increase and it expects the figures to keep rising during the COVID-19 pandemic. Unfortunately, the good news is closely followed by some bad news. The growth in the number of gamers has made them a target of fraud.
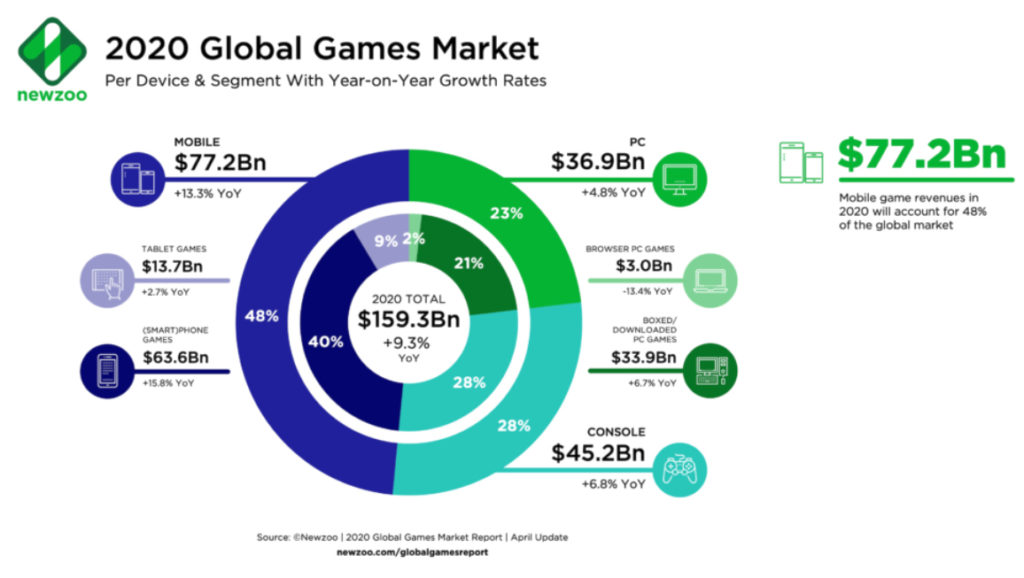
The ACI Worldwide report, What turns players into payers, predicts that mobile gaming alone will be a $100 billion market by 2021. “While the potential revenue opportunity for games has never been higher, the free-to-play model and abundance of game choices have given gamers the power to choose where, how, and when they spend their money. Games get one chance to engage, delight, and convert their players,” noted the report.
A 2018 research report by ACI Worldwide and Newzoo revealed that as many as one in five gamers in Germany, the US and the UK have been a victim of payment fraud while playing popular games. One in three gamers is less likely to spend money on games online due to fraud concerns.
One gaming company, PUBG Corporation has signed on with Vonage to include two-factor authentication (2FA) as a quick, simple way to identify and validate genuine customer transactions,” said a PUBG Corporation spokesperson. “With 2FA capabilities from Vonage, we are protecting our customers against theft, building trust and increasing customer loyalty.”
How it works
Using just a phone number, Vonage generates codes, localises and employs the fastest channel available, switching from SMS to voice when needed, to authenticate new and existing customers. This works in tandem with the Vonage SMS API which allows customers to send SMS verification codes to users who register for their service.
Sunny Rao, Vonage senior vice president and general manager for the Asia-Pacific region, said: “Vonage Verify gives customers the ability to authenticate end-users on their preferred channel and customise the failover workflow process with no coding or development, giving customers total control to reach end-users and improve customer acquisition easily.”
2FA enough?
“Unfortunately, 2FA does little to mitigate infection,” said Chua Bo Si, Technical Program Manager at HackerOne.
He added that mobile malware (or malicious mobile applications) exploits the fact that the users were tricked/enticed and gave explicit permission to install the application on the mobile phone. This basically allows the malicious application to have free reign over the mobile phone and also allow access to the data and mobile applications with poorly configured permissions (e.g. Intent).
What else to do
Chua believes that user awareness is the first line of defence. “If the producer or company that uploads the game is dubious or unknown, think twice before installing them, even if it is from the Google Play Store,” he added.
He also suggests using a well-known antivirus software specifically made for Mobile Applications to scan for malicious mobile applications.
“Finally, be aware of the application asking for excessive permissions to your mobile device. Some of the permission grants might be intended and required for the mobile application to function, but if you see that excessive permissions are requested for, it should also raise an alarm that you should investigate further before accepting,” concluded Chua.




