Based on a survey of cybersecurity and application development professionals conducted by Enterprise Strategy Group (ESG), the "Modern Application Development Security" eBook highlights the extent to which security teams understand modern development and deployment practices, and where security controls are required to lower risk.
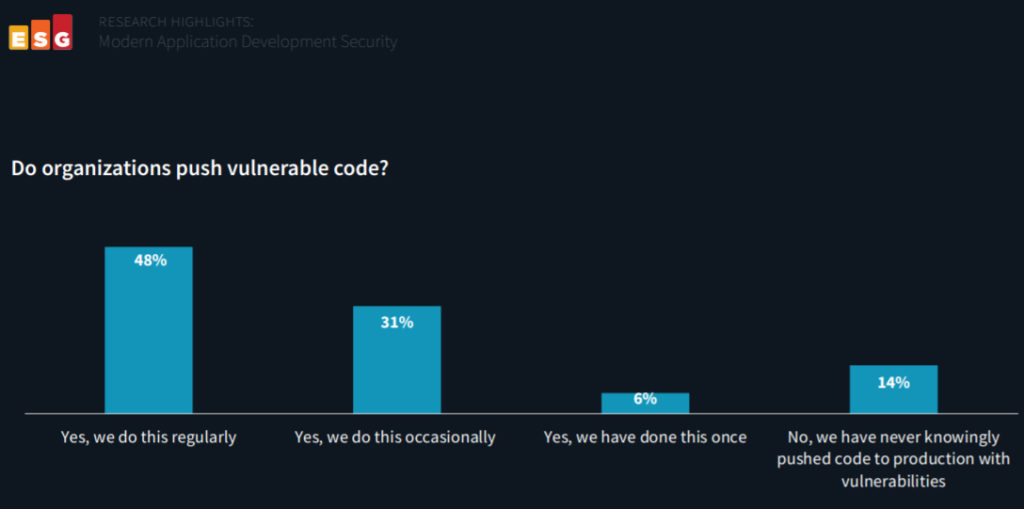
The study finds that nearly half (48%) of survey respondents consciously push vulnerable code to production due to time pressures. According to 43% of respondents, integrations complementing high-velocity application development are most important to improving application security programs.

FutureCIO spoke to Stephen McNulty, president, Asia-Pacific and Japan, at Micro Focus to get his perspective on whether security can and/or should be sacrificed in favour of faster-to-market rollout of applications.
Do you agree that pressure to go-to-market faster is creating the potential to introduce flaws in business applications, including mobile apps?
Stephen McNulty: Indeed, in organisations’ haste to move along the application development supply chain, they often overlook the aspect of security. Furthermore, the pressure to roll out applications is even higher in the current climate, as more customers are engaging with businesses virtually.
In the face of this pressure, the implementation of security unsurprisingly lags – specifically at the stage where code is being produced and released. However, organisations need to keep in mind that if they were to jump the gun in releasing their applications without introducing security in the early processes of development, they could expose them to serious vulnerabilities.
While the implementation of security at different stages of development (DevSecOps) might initially slow down the go-to-market cycle for applications, it creates a more reliable and sustainable final product with built-in security checks.
Does the work ethos – fail fast – encourage this behaviour?
Stephen McNulty: This principle interestingly aligns with DevOps’ core philosophy, which primarily promotes enhanced agility and implementation of automation processes. As the purpose of DevOps is to eliminate bottlenecks to increase efficiency, some might see the integration of security as an impediment to the process.
With that said, to determine whether it is the right time to live up to the philosophy—fail fast, I would suggest organisations to consider the potential costs to failing. In the current work-from-home environment, organisations that continue to innovate must ensure that security continues to be their top priority.
The ability to showcase that business applications and solutions were built in a secure environment will not only ensure compliance but also protect them from potential cyberattacks and breaches. To do this, it is important to equip teams with the right security assurance tools at the various stages of the supply chain.
These tools help to introduce security at the very beginning of application development so that it is integrated from day one and part of the software development lifecycle – and does cause any delays in the process.
Do you agree with ESG’s view that poor integration between DevOps teams and third-party security vendors lead to less secure applications?
Stephen McNulty: The lack of integration both internally and externally is definitely one of the growing concerns amongst organisations—this is further exacerbated with the current remote work arrangement that reduces communication touchpoints. The World Quality Report 2019-20 by Micro Focus highlighted the need for full lifecycle testing. However, organisations are not yet tackling this methodically.
To overcome this, organisations need to evaluate the potential vulnerabilities at every stage of the software development life cycle. It begins with something as simple as access to the network. Employees – or third-party vendors – that are working remotely come with security risks, as they are not using a secured office network. It is crucial to ensure that the network used is adequately secured.
This means isolating developers in a separate subnet, or a completely separate network. The lifecycle and governance of identity definitely have become far more important in the collaboration between teams and outsourced partners.
Next step is to ensure that the hardware of all parties involved in the application development is regularly scanned and patched. We have seen many cases of ransomware breaches on unpatched operating systems that can hijack the environment. Same goes for the tools and software that employees use to develop business applications.
Once a developer starts writing the code, the organisation needs to ensure that it is regularly scanned and that vulnerabilities are reported to the security team immediately and remediated in a timely manner and with the proper change controls in place. This ensures that the code and the business application have security built-in by design.
After the application is developed and an employee or third-party vendor is ready to pass the code to the next stage of the software supply chain, we still need to make sure quality controls and change release processes are followed.
Do you see a trend towards increased spending on application security particularly towards the cloud? Given that revenues are down, and spending controls up, where will this new budget come from?
Stephen McNulty: The current pandemic has impacted the revenues and spend on new projects. The current situation has also increased the need for greater security and risk compliance.
As communication, transaction and businesses operations are dealt with virtually, organisations simply cannot afford any hurdles caused by buggy applications. Based on our observations, we will be seeing more interest in cloud-based security solutions in areas such as quality assurance and testing.
A cloud-based approach for security testing not only ensures that applications are developed faster but also help to increase visibility into the testing environments – making coordination and management easier, which also, and perhaps significantly, increases cost-efficiency in the current climate.




