The Colonial Pipeline is the largest pipeline system for refine oil products in the U.S. and supplying 45% of the fuel needs of the East Coast, including gasoline, diesel, home heating oil, jet fuel, and military supplies.
So when it succumbs to a ransomware attack, it is a wakeup call not only to the management of the US$1.39 billion (annual revenue in 2021) company, it is a reminder to every organisation of the real threat that dropping the cybersecurity ball can mean to the organisation, its employees, partners and customers.

ABI Research‘s digital security research director Michela Menting warns that any company (especially one with upwards of $500 million in annual revenues) that is not prepared for such attacks has clearly been purposefully skimping on basic cybersecurity tools, training, and strategy.
The nature of the attack
Colonial Pipeline was hit with a ransomware attack where infiltrators penetrated the corporate IT systems, installed malware, encrypted data and systems, and locked out Colonial Pipeline from its own IT systems.
The attack was perpetrated by a group known as DarkSide. Menting said the group utilizes an additional tactic that involves stealing a copy of the data before encrypting the original. This puts additional pressure on the company, as DarkSide threatens to release the data publicly unless the ransom payment is received.
Omer Dembinsky, data research manager at Check Point Software Technologies argues that DarkSide works in a Ransomware-as-a-Service (RaaS) model, where it leverages a partner program to execute its cyberattacks.
“This means there is little known at this point about the real actor behind the attack,” he laments.
The entry point of the attack
The primary infrastructure weakness is unknown at this point as Colonial Pipeline has not revealed any information pertaining to how the threat actors got in.
“Typically, however, such groups use a mix of social engineering, such as phishing emails, and vulnerabilities of remote access mechanisms, to get in and then privilege escalation (e.g., gaining elevated access to restricted resources) and lateral movements (e.g., using one system to access other systems to move deeper into the network) inside the infrastructure to identify weaknesses and assets,” said Menting.
How to prevent the hack, or to make it more difficult/less successful
With much about the attack remaining unknown (at the time of this post), “the fact that ransomware shut down most of Colonial Pipeline's operations, both IT and OT, means that their security posture must have been poor at best,” noted Menting.
Everyone is a target
Ransomware is neither new nor revolutionary. The fact that there is a sophisticated, organized cybercriminal market for ransomware shouldn’t be news for anyone in the industry. The hack on Collonial is a harbinger of cyberthreats to come.
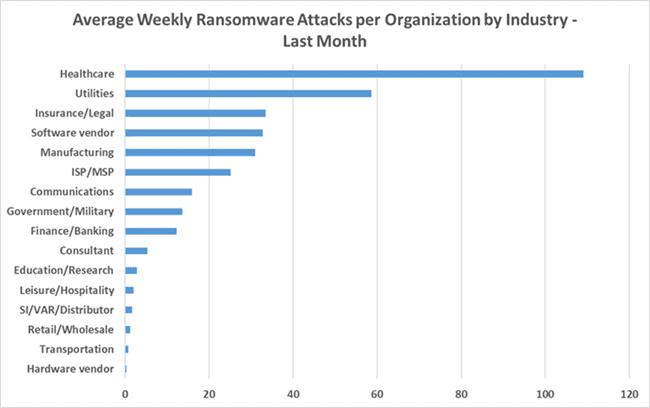
CheckPoint says the number of organisations impacted by ransomware globally has more than doubled in the first half of 2021 compared with 2020. The Asia Pacific has the highest average weekly number of ransomware attacks per organisation.
The insurance/legal, manufacturing, and healthcare sectors are the most targeted sectors since the beginning of April 2021 in Asia Pacific.
No end (from attacks) in sight
Colonial follows other large scale attacks including against the city of Tulsa, and the REvil ransomware that tried to extort Apple, and more recently against AXA Insurance group’s international subsidiary AXA Partner and its operations in Thailand, Malaysia, Hong Kong and the Philippines.
Menting acknowledged that cybercrime is as lucrative as the IT industry itself. “For companies that take these threats seriously, there are a great many resources available, including guidelines, standards, regulations, best practices, technologies, architectures, strategies, and information sharing processes,” she explained.
These tools are available at the public, private, and international levels, and the U.S., where the attack took place, is among the leaders in the cybersecurity space.
By some accounts, the cybercrime community appears more organised than the industries and consumers it targets. More recently cybercriminals have started to use some of the very same tools the IT security has developed to protect cyberattacks.
ABI Research says a failure as big as that of Colonial Pipeline simply shows an obvious wilful ignorance to take cybersecurity seriously, to their unfortunate detriment.
Expanding connectivity in both IT and OT will mean continuously increased threat vectors. The key is to understand that even the best cybersecurity solutions will not, and cannot, always guarantee absolute protection for all assets.
Consequently, organizations large and small should always be prepared for an eventual attack, which means architecting their infrastructure so that it can continue to operate despite an ongoing attack while simultaneously recognizing and dealing with the threat.
This is not an easy feat, but there are concepts such as zero-trust security and cyber-resiliency which can aid in creating such a posture.
Expect an acceleration of efforts?
ABI Research has forecasted that cybersecurity spending for critical infrastructure will grow to reach US$106 billion in 2021. Should it be more?
Menting noted that many in the industry expected attacks against critical infrastructure of this nature and breadth to have been launched by nation-states.
"However, despite global geopolitical tensions, most of the big powers have abstained from such large, public-facing, debilitating attacks against one another, as they could be considered acts of war," she added.
Despite the dangers, cybersecurity efforts have been sporadic, fragmented, and half-hearted in critical infrastructure, leaving many gaping holes in security postures.
Unsurprisingly, the organized cybercriminal market has stepped in to pick the low-hanging fruit, but ransomware is such a profitable market that it has become highly competitive, with sophisticated ransomware gangs going after bigger and bigger targets.
There is still hope?
However, there is still a fine line for the types of companies organized crime is willing to go after. The closer these groups get to undermining critical infrastructure, the more dangerous they become to national security and the greater the risk of serious repercussions from concerned governments.
Additionally, these repercussions may not just come from the victim country, but also potentially from their host nation, especially when this country might be Russia or China.
Menting deduced that to that end, while there is no conclusive evidence that most of these groups are state-sponsored, there is clearly an implicit understanding between the gangs and their home countries that allow them to conduct their illicit operations with impunity. If these gangs start to cause too much trouble from a national security perspective and create problems for their host nations, reprisals back home may be likely.
“It is clear DarkSide is conscious of such consequences, as evidenced by their recent half-apologetic press release and their efforts to distance themselves from any political motivation some may want to infer about their attack,” she opined.
Nonetheless, it may be that, in this instance, they may have gone after too big a fish, however poorly secured Colonial Pipeline seems to have been.
“Hopefully, however, it will give large corporations a push to revise and strengthen their cybersecurity strategies, especially those in critical infrastructure, and show them – yet again – that they are not exempt from common cyberattacks,” concluded Menting.




