Cybersecurity firm IntSights has released its latest research white paper ‘Selling breaches: The Transfer of Enterprise Network Access on Criminal Forums’ which delves into the sale and purchase of unauthorized access to compromised enterprise networks and how such activities have become a significant enabler for criminal cyberattacks, particularly ransomware infections.
With the shift to a remote workforce, the resulting increase in the use of remote access tools and services have given attackers more attack surface to exploit and fuelled the marked increase in the sale of access to compromised networks.
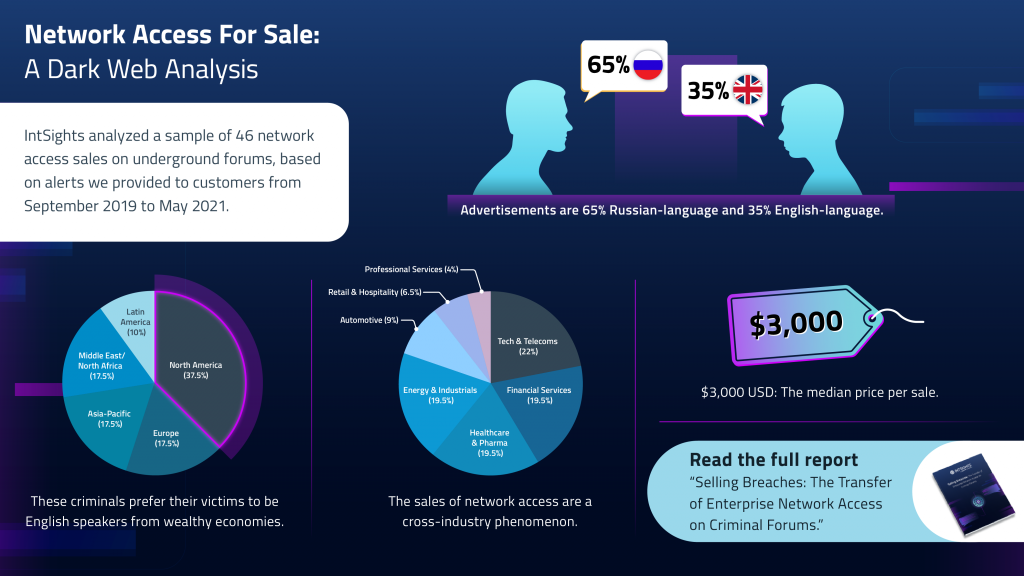
According to Paul Prudhomme, head of threat intelligence advisory at IntSights, there is a disproportionate focus in the US and other industrialised countries, which are just popular targets for crime in general because they're more lucrative for criminals.
“By analysing the statistics, the sales of the technology and telecom companies are the most popular targets by just a bit, followed closely in second place, financial services, healthcare and energy and industrials,” he added.
Fuel for cyber attackers
Prudhomme acknowledges what has been observed since the start of the pandemic. Criminal elements are taking advantage of the inherent holes in the infrastructure, particularly around the defences.
Cybercriminals are using known vulnerabilities in many of the foundation technologies used to connect people, businesses, and organisations. For instance, Remote Desktop Protocol (RDP) is part of the operating system of most client devices and is used to control these remotely.
A vulnerability of RDP that is commonly exploited is unrestricted port access (Port 3389). Attackers can use this port to carry out on-path attacks.
According to Prudhomme, brute force attacks are commonly used against RDPs for use in general as well as ransomware operations. The other common target following COVID-19 is virtual private networks (VPNs) which have grown in popularity as enterprises mandate large masses of remote work. The very same technology that is supposed to provide a secure connection between servers and applications and the users accessing these can also be used to infiltrate infrastructure.
He pointed out that VPNs that aren’t updated are the other pathways to infiltrating the network. Unfamiliarity with configuring VPNs is an easy access pass to compromising networks.
Prudhomme is careful to not dismiss the value of VPNs, saying: “Just because it can be compromised, doesn't mean you shouldn’t use it. I mean every line of defence will have a possibility in it. So ultimately, a robust security posture will have multiple lines of defence behind it. So, if one layer of defence fails, you still have several other ones that can stop an attack,” he elaborated.
The other option is social engineering attacks – sending people links to download what users think are legitimate communications.
Tradeoffs
Prudhomme remains a proponent of multiple lines of defence, commenting that a layered defence offers multiple means of protection.
Asked whether such a posture introduces latency to the overall performance of the network or applications, he acknowledges that there will always be trade-offs between usability and security.
“Security is often inconvenient. That is the nature of the beast. With that said, there are some things that one can do that that have very little or just a minor impact on usability,” he explained.
He cited the use of two-factor authentication as a proven means of protecting accounts. An attacker may somehow acquire a user’s access name and password but without the third code, they should not be able to get access.
He acknowledged that two-factor authentication processes will continue to evolve as attackers figure out a way to circumvent these technologies. “The two-factor authentication does add a degree of inconvenience. I think the value that it adds to the defence is worth that relatively modest amount of inconvenience,” he opined.
No security is perfect
Prudhomme does not deny that the imperfections in security solutions. Both VPNs and two-factor authentication are not immune to attacks. By employing multiple lines of defence, he is of the opinion that at some point one, if not several, of those will fail. “Let’s hope that at least one will hold,” he called out.
Asked whether a zero-trust concept is a more secure approach to prevent attacks. He reiterated that ‘there is no such thing as perfect security.’
“I think zero trust reduces that vulnerability in so far as the attackers like to abuse that trust. And if there's no trust for them to abuse, that does make it harder for them to do their job. Not impossible, but it still makes their lives harder,” he added.
Employing multiple defence strategies has the potential to deter attackers that are looking for an easy target. “If they find that a potential victim is simply too hard to compromise. Not impossible, but just too hard. It's too much work, they'll just go somewhere else,” he continued.
The only time this approach doesn’t work is against state-sponsored attacks. In these situations, a target is the target and no one else. “If they want you, they will get you. And they will throw everything at you until they get what they want. But for [common] criminals at least, if you just make their lives difficult, you can eventually deter them,” concluded Prudhomme.
Click on the PodChat player and listen to Prudhomme share highlights of the report as well as insights into strategies for improving cyber defences in 2022.
- how the surge in demand for sales of compromised network access can lead to significant enablers for ransomware attacks
- opportunities for security professionals to use intelligence to detect and thwart attacks
- what organisations can do to improve security hygiene and prevent the network compromise events




