The growing frequency and intensity of cyberattacks have been pushing businesses to boost their cybersecurity defences. In August 2021, a ransomware attack on a specialist clinic in Singapore, potentially exposing the data of more than 73,000 patients, prompted the Ministry of Health (MoH) to conduct a thorough review of the clinic's compromised IT system. The incident highlighted the fact that ransomware does not just lock down data, it also compromises consumer trust and can severely impede businesses.
According to PwC's recent survey, consumers have become more protective of their personal information, with data security having a far greater impact on brand trust than any other factor. However, only 38% of the respondents from Singapore agreed that “brands protect their data to a great extent.”
Unfortunately, with the ever-increasing sophistication of attacks, there is no silver bullet to ensure an organisation’s perimeter is 100% ransomware-proof. While preventive controls can help stop basic attacks, the only way to guarantee complete immunity is for the business to not be connected to the internet altogether.
Our reliance on digital and connected technologies across the entire economy – from point-of-sale (POS) terminals at small neighbourhood cafes to Artificial Intelligence (AI) and robotics-driven manufacturing processes – means being offline is realistically not feasible.
Businesses need to look beyond perimeter controls and consider how quickly they can remediate and get their business back up and running following an attack.
To do so, it is important to understand the two common methods attackers use to disrupt businesses and force them to the negotiation table: encryption and exfiltration.
Business paralysis with encryption
It is nearly impossible for a business to operate today without data.
This simple truth has been the principle guiding ransomware attacks and building their popularity since their inception in 1989 with the first-ever strain, PC Cyborg. While this rudimentary ransomware only demanded a payment of around US$500 and was distributed by floppy disk, its authors understood that if you lock up someone’s critical data, they will pay to regain access.
Since then, an entire economy has spawned, feeding off the desperation of companies suddenly staring into the abyss of days, weeks, or even months without access to critical data and systems that are required to operate their business.
According to a 2021 study by IDC, nearly half (44%) of the companies surveyed across the globe are willing to pay the ransom following a ransomware attack. Singapore is among the countries with the highest willingness, with 43% of the companies that are willing to pay the ransom in hopes of retrieving affected files, either internally or through insurance payout.
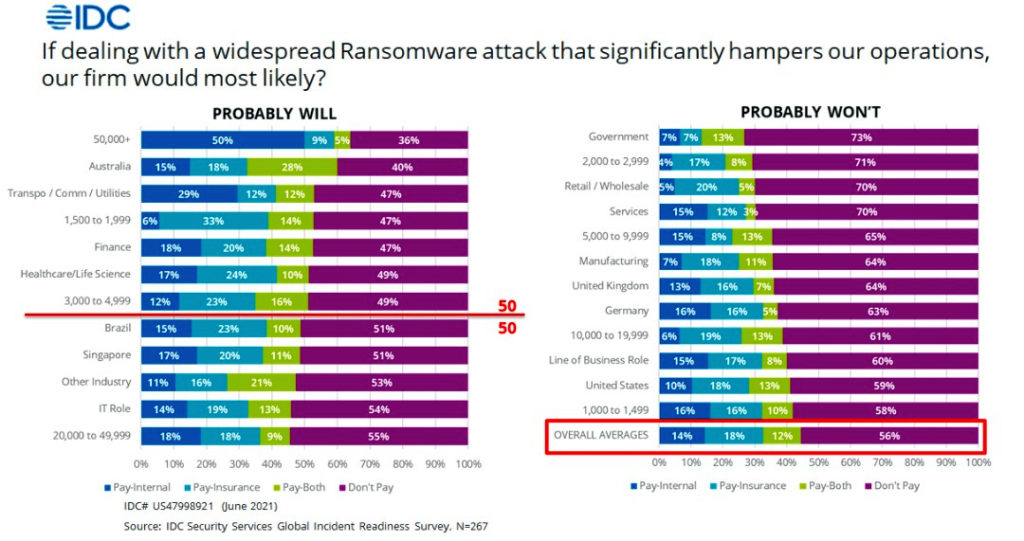
Ransomware is among the highest-rising cyber threats in Singapore. Based on the latest report from the Cyber Security Agency (CSA), the country recorded a 154% increase in ransomware cases from 2019 to 2020. As the world continues to become increasingly reliant on digital methods, this number is only expected to grow. There is, however, a better way – particularly as there is no guarantee attackers will decrypt data, and paying criminals simply further incentivises future attacks on other organisations.
The key to rapidly recovering, without negotiating with criminals, is having comprehensive and up-to-date backups that allow organisations to effectively turn back the clock and restart operations from a “save point” prior to the infection. Implementing a modern backup system was also cited by the CSA as one of the preventive measures against ransomware, and encourages businesses to remain vigilant against such threats, along with ensuring good cyber hygiene.
Ransomware attackers are savvy and understand that backups ruin their business model. The more sophisticated strains now actively seek out backup data to hamstring recovery efforts and increase the likelihood the victim will pay. Immutable backup data, natively air-gapped, provides organisations with a “ransomware insurance policy” that helps business-as-usual resume as quickly as possible, massively reducing recovery times from several days to just hours.
Exfiltration pincer movement
One of the biggest evolutions in ransomware was the introduction of exfiltration capabilities, first seen in the wild in late 2019 with the variant, Maze. The pincer manoeuvre has introduced both stealing and encrypting data and is now the preferred tactic of ransomware groups around the globe.
By threatening to publish stolen data, attackers increase the urgency of the victim’s response while also raising the stakes of the attack’s consequences. In December 2020, information technology firm SolarWinds fell victim to a highly sophisticated breach, which exfiltrated the data of its clients with the SolarWinds Orion installed.
A website called SolarLeaks was created to sell the data stolen from the companies breached in relation to the SolarWinds attack. The CSA of Singapore then investigated the incident and advised the company on the measures that need to be taken after the breach.
In the immediate fallout of such an attack, the first few days are traditionally spent in sheer panic as the organisation attempts to identify what data was taken. Having visibility into exactly what files were stolen is critical to response efforts as it allows the business to understand whether any personally identifiable information (PII), financial data, or intellectual property was taken, and which additional authorities or regulatory bodies need to be notified.
Machine learning models applied against backup data can help significantly accelerate this discovery process and reduce the time it takes to understand the full scale of an attack from days to mere minutes. This allows impacted businesses to be notified quickly so they can take appropriate measures to protect themselves from potential fraud stemming from the stolen data.
These attacks are not going to stop anytime soon, and will, in fact, continue to evolve and become more sophisticated and disruptive as attackers aim to make recovery as difficult and costly as possible. While businesses can never be completely immune from the risks of ransomware, they can minimise disruption and ensure operations are back up and running as quickly as possible.




