Turnkey cyber range programme closes the cybersecurity workforce gap
With cybercrime on the rise and the scarcity of cybersecurity professionals, organisations in Asia pacific are at risk of cyber attacks and security threats more than ever. Consequently, cybersecurity jobs are growing by more than 30% annually, sited in a report by (ISC) 2, 2021, students who are well prepared will be the first to be considered for the industry’s top jobs.
One company is addressing the skills shortage, in anticipation of the highly sought after careers in the coming years.
Academic programs that prepare students for jobs in cyber security are currently in high demand, and this number will grow exponentially as more organisations digitalise their workflow, and move their core functions to the cloud.
The Keysight Cyber Training Simulator (KCTS) enables students to develop their skills in a realistic environment with sophisticated tools currently used by professionals in enterprises and governments worldwide. As a result of the training and exposure, students can quickly fill the roles in cybersecurity across many industries soon after they graduate.
The simulator delivers advanced design and validation solutions to accelerate innovation and secure the cyberspace. Its cyber range simulator augments real-world traffic uses the company’s proprietary BreakingPoint solution.
Educators are making cybersecurity training a high priority to address the urgent need for cybersecurity professionals across all industries.

"Targeted at university graduates, the programme aims to develop the next generation of leading experts to stay at the forefront of an ever-changing cybersecurity landscape.”
Boon Juan Tan, vice president and general manager of General Electronics Measurement Solutions at Keysight Technologies
- Boon Juan Tan
Image source: Keysight Technologies.
KCTS is designed to help academic institutions fill the cyber industry workforce gap with industry-ready graduates. Unlike the common script-based cyber range approach, this simulator gives a realistic and rounded experience for the faculty and students.
Hone their skills in real-world scenarios
Distributed denial-of-service (DDoS) cyber attacks disrupt the normal traffic of a targeted server, service or network by overwhelming the target infrastructure with a flood of Internet traffic, triggering a system crash.

.
Image source: Keysight Technologies
https://www.keysight.com/sg/en/products/network-test/keysight-cyber-training-simulator.html
Students will learn in the same environment they will use on the job right after they graduate. For example, the platform simulates real-world attacks such as malware and malicious DDoS attacks enabling students to swiftly learn mitigation strategies from actual scenarios, not just scripts
Think on their feet
These augmented scenarios are regularly updated by professional teams, ensuring students are trained on the latest trends in the variety cyber threats.
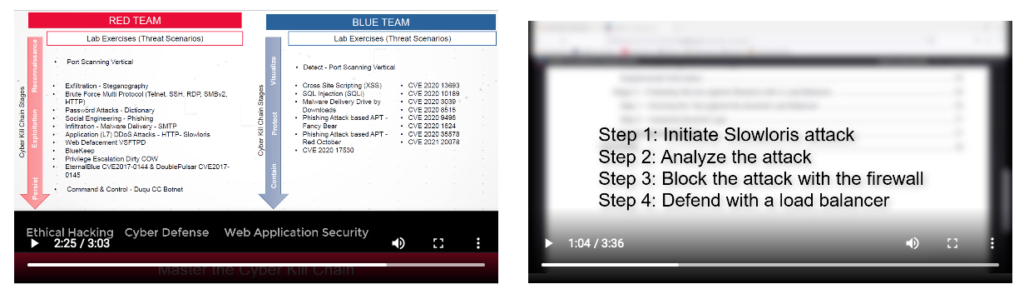
A full range of 'red team and blue team' lab exercises, based on one or more of the simplified cyber kill chain stages, prepares students for the unexpected and ever changing environment in the cyberworld.
Easy integration into the school’s Learning Management System (LMS) :
A common frustration for faculty is when third-party teaching tools have limited integration with the university’s LMS. Its learning tools ensure that instructors can leverage their university’s LMS investment. This way, the instructor has full ownership and control in creating and customising scenarios for the syllabus.
The design and validation solutions help in accelerating innovation to connect and secure the world. Its speed and precision standards extend to software-driven insights and analytics to market faster across the development life cycle.
The solution assists at different stages from in-design simulation, prototype validation, automated software testing, manufacturing analysis and network performance optimisation across cloud environments.




