The authors of the paper, Thinking Outside-the-Box for Cyber Defense: Introducing an Innovation Framework for the 21st Century, noted that most defensive cyber capabilities, such as intrusion prevention systems and automated self-healing systems, are typically breakthrough innovations that are expensive, technologically more complex, and require extensive research.
"We believe that to systematically defend cyberspace, every type of innovation is needed to ensure an acceptable level of cybersecurity. In particular, by refusing to concede disruptive innovation to cyber threats and pursuing this type of innovation for the defence, we can prevail in future cyber conflict."
Katherine Hutton, LTC Ernest Wong, Ryan Gagnon

In this FutureCISO series, we ask Yvette Lejins, resident CISO for Asia Pacific and Japan at Proofpoint, for her take on the importance of looking beyond traditional approaches to security monitoring, detection and response to manage a wider set of risks.
"Because cyber threats are becoming more sophisticated! Just last year (2022), TA453 evolved and started using Multi-Persona Impersonation to trick victims," called out Leijins.
She explains this is why organisations must adopt a proactive and holistic approach to manage a wider set of risks since traditional security measures are no longer sufficient to protect against modern threats like ransomware, phishing, and supply chain attacks.
"Integrating threat intelligence, security automation, and employee training to enhance security posture is necessary. Advanced technologies (e.g., machine learning and behavioural analytics) are also needed to identify and respond to threats in real time," she continued.
Developing personal effectiveness
Stuart Madnick, a John Norris Maguire (1960) Professor of Information Technologies at the MIT Sloan School of Management, argues that cybersecurity has reached a tipping point.
"Following decades of private-sector organisations more or less left to deal with cyber incidents on their own. Now, governments feeling a need to “do something,” and many are considering new laws and regulations," he writes in a Harvard Business Review post.
Evolving regulations must now be added to the already myriad challenges security professionals must face as part of their role as stewards of the organisation's security policies and frameworks.
Leijins says to be effective, a strategic cybersecurity leader requires technical expertise, business acumen, and leadership skills.
"A successful CISO should align cybersecurity initiatives with the organisation's business objectives and communicate effectively with executives and board members to demonstrate the value of cybersecurity investments."
Yvette Lejins
Building a strong board-CISO relationship is critical, according to Proofpoint’s Cybersecurity: The 2022 Board Perspective report. "CISOs should be risk experts and consider employee viewpoints while managing risks and bridging security gaps. They should see the bigger picture and be adept at incident management during high-pressure situations," she added.
Keeping cybersecurity strategies relevant
How do you re-evaluate your overall cybersecurity approach to identify opportunities for detecting compromise and immediately investigating and responding?
Proofpoint advocates for people-centric cybersecurity as most attacks originate from someone clicking on a malicious link or downloading a suspicious attachment. Leijins comments that with socially engineered attacks rising, it's crucial that organisations identify very attacked people (VAPs) and determine who is most likely to fall for these attacks to prevent data compromise.
She advises that organisations must also recognise that traditional security approaches are insufficient for remote workforces. With cloud adoption and BYOD (bring your own device) policies, employees can bypass corporate networks and firewalls.
"Implementing layered defences at the email gateway, in the cloud, and at the endpoint, while utilising email authorisation protocols like DMARC and SPF, is necessary to ensure an organisation's protection," she continued.
Essentials to modern security practices
Security tools have evolved over the years to reflect the changing business and technology landscape. Sadly, the pace at which organisations are modernising their security posture, be it in the form of processes and decision-making, may not be in lockstep with the speed, tenacity and even cunningness of threat actors.
And as governments increase their efforts to force industry players to take on the threats with greater zeal, it may be time for organisations to listen and support the CISO and the security team to do their job and do it well. And this includes modernising security to provide the most strategic benefit in a cloud-application-centric and hybrid worker future.
"Security modernisation efforts should focus on adopting a cloud-centric security approach that enables a more holistic view of threats across on-premises and cloud environments," said Leijins. "This should include integrating security tools and technologies to enable quick detection, response, and remediation of threats."
She lists other key aspects including implementing identity and access management controls, prioritising data protection, and embracing a risk-based approach to security.
Security is as much about behaviour and culture
While a lot of attention has been placed around the critical role of technology towards the security of an organisation, at the core of the threat lies human behaviour. Remember the adage: humans are the weakest link.
And just to be clear, the "human" in this case is not limited to the untrained consumer or even careless employees of an organisation. It includes well-meaning, even sometimes trained professionals, who by circumstances of the occasion, failed to practice good security hygiene.
This brings us to the topic of investing in holistic behaviour and culture change programs designed to provoke more secure ways of working. Leijins acknowledges that holistic behaviour and culture change programs require a combination of training, awareness campaigns, and policy enforcement to promote more secure ways of working.
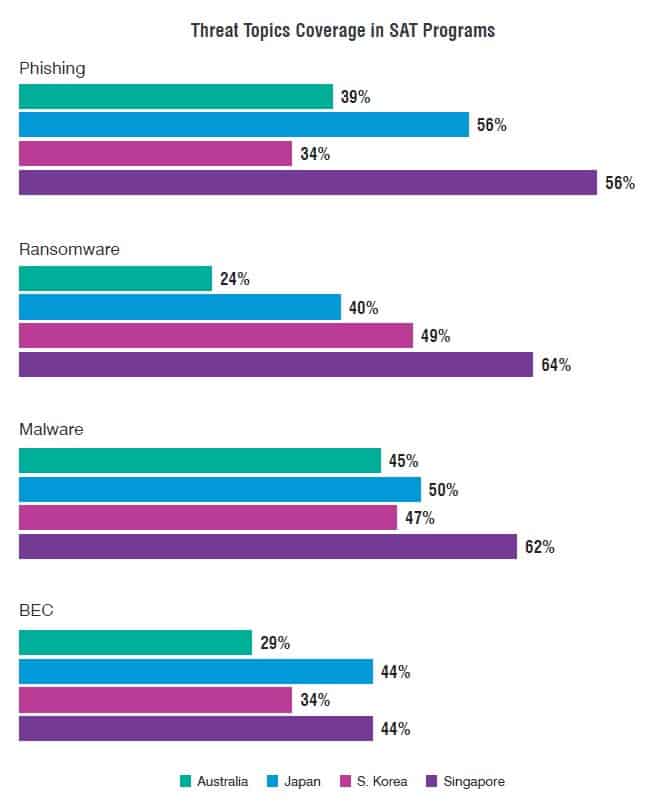
While regular security awareness training is critical in helping employees recognise and avoid common threats, according to Proofpoint’s 2023 State of the Phish report only 54% of Singaporean organisations train their entire workforce, and only 2 in 5 conduct phishing simulations.
Attitudes can be everything in this case. The same report reveals that at the global level, only 33% of employees say cybersecurity is a priority, compared to 90% of security professionals who see security as a top priority at their companies.
"Establishing clear policies and procedures around data protection, access control, and incident response and enforcing them consistently across the organisation is equally crucial. A robust security awareness training program and consistent policy enforcement can help protect an organisation's people and data," she concluded.




