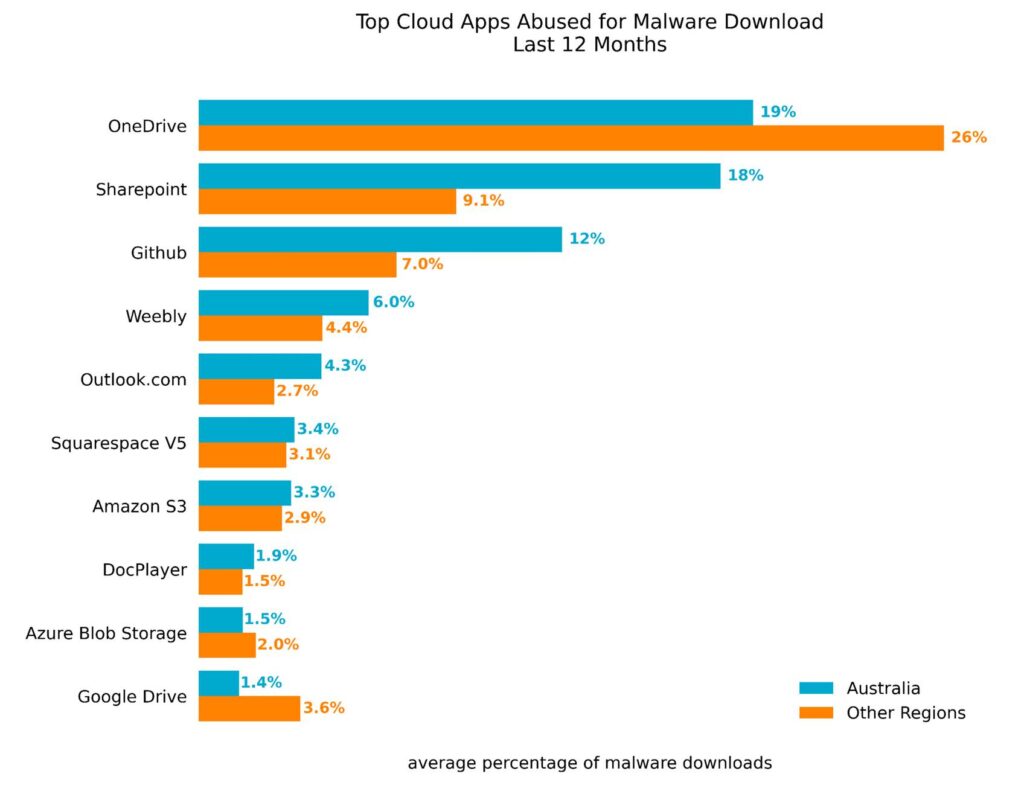
In what may well be the norm, the Netskope Threat Labs Report, released in October 2023, claimed that Australia leads the world in terms of cloud app adoption. Coincidentally, 64% of malware downloads in Australia come from cloud apps with OneDrive, SharePoint and GitHub ranked top in terms of channel for malware distribution.
Ray Canzanese Jr, director of the Netskope Threat Labs, laments that legacy security technology is often blind to cloud ecosystems, and unable to provide granular visibility and control over the data flowing to and from cloud applications.
“Too many organisations also still create security exceptions for enterprise cloud applications such as OneDrive, which we know is the source of more malware downloads than any other cloud app. Cloud ecosystems have become a major potential source for cyber threats in 2023, and organisations must improve application and network monitoring and detection capabilities to include cloud use,” he opined.
Breaches – as seen internally
Forrester principal analyst Allie Mellen says a data breach is often a stressful event that requires a timely response. She added that incident responders have to drop everything to respond quickly and completely in the event of a breach.
“The incident lead often manages the breach response, including the war room and coordination with other teams in the organisation. The response could take hours, days, or weeks depending on the technical scope of the incident and the requirements for post-incident review,” she added.
Response attitude at the time of the attack
Security experts and practitioners FutureCISO speak to acknowledge that breaches continue to happen. The only good news, if you can call it that, is that the window to detect is narrowing. The IBM 2022 data security report estimated it took an average of 277 days to identify and report a breach.
Off-the-record talks with CISOs suggest that the window of detection is coming down to a few days, although estimates point to 49 days as the average time it takes to identify a ransomware attack.

However, the question remains how prepared are organisations to respond to attack? Mellen suggests the best way to prepare for a cyberattack is to build incident response plans at multiple levels: for the security team and the broader organisation.
Allie Mellen
“Every part of an organisation is affected in the event of a breach that compromises customer data or employee data, as the public response requires everyone to participate. Making sure everyone knows their roles is critical to successfully responding to a breach.”
“Further, testing these plans in a real-world scenario regularly is crucial to ensuring everyone knows what to do and when to do it,” she continued.
What the board wants/needs to know
Asked what information is needed to keep the board and leadership updated on matters related to cybersecurity attacks, Jinan Budge, VP and principal analyst at Forrester concedes that there is no one set of information or metrics which is a silver bullet to communicating with the board and executives to update on the extent of a cyberattack, or cybersecurity.
“Rather, delivering consistent content and meaningful metrics while translating what they mean into terms the Board can understand are the secrets to success. This is not about the most beautiful PowerPoint, explaining the most innovative tool or detailed exploits,” she added.
Key dynamics to remember
- Your board expects a security team that manages cybersecurity as a risk, not a siloed cost centre that uses its language.
- Your board expects partnership, mutual trust and proactivity, not one-way, overly manufactured security presentations
- Your board expects straightforward communication in business terms, not tech speak.
Some key recommendations:
- Utilise your firm’s risk management framework, focusing on impacts.
- Even if it’s not your first time reporting to the board, make sure you get executive coaching on presenting and communicating, as well as business and board terminology.
- Explain the current security landscape and your vision for addressing it
- Measure the progress over time of your security program
- It’s always helpful to have someone who routinely presents to your board on sensitive issues (e.g., general counsel or CFO) to review your content.
- Prepare to recap major cybersecurity impacts, and frame how they could impact your term
- Foster a champion on the board who will support security initiatives, and coach you to address board expectations
- Define and socialise a common language, for all to use. Don’t assume that just because cybersecurity is always in the media, everyone understands the nuances of phishing for example.
- Bring in outside perspectives from time to time to share their perspectives
The importance of visibility
You cannot protect, and respond, to what you can’t see. Mellen says visibility is the first step to better understanding and detection of attackers. However, visibility alone isn’t enough, particularly for detection and response.
Security visibility, the capability to see all aspects of an organisation’s digital footprint including the risks and vulnerabilities within it, shouldn’t be questioned.
“To do detection well, you need a team to continuously build detections – and a team to respond to them. For teams that don’t have a lot of resources, it’s best to look to an external service provider like managed detection and response (MDR) to support a detection and response function, as managing that team internally can be difficult to attract, train, and retain,” she continued.
The importance of a security culture
“Security culture refers to the set of values, shared by everyone in an organisation, that determine how people are expected to think about and approach security. Getting security culture right will help develop a security-conscious workforce and promote the desired security behaviours you want from staff.”
National Protective Security Authority, USA
Budge concurs adding that security culture is not a nebulous, squashy term, and in 2023, the industry has developed a rigorous understanding and definition of security culture, and its impact.

“CISOs are measuring the attitudes, cognition, norms and responsibilities around cybersecurity, ultimately helping them understand the sentiment around cybersecurity in different parts of the organisation.”
Jinan Budge
She praised efforts to change the perception, not with more training, but with a thorough review of their security policies, processes, and technologies.
“A strong security culture helps CISOs gain budget, advocacy and visibility for themselves and their security program. It ensures that everyone, from the board level down, is displaying the correct cybersecurity behaviours, are advocating for the security team, supporting their initiatives and protecting themselves and the organisation from harm,” she continued.
Forrester Research stats
- 2.7 times more likely to have a security awareness and training program that changes behaviour and embeds a strong security culture
- 1.4 times more likely to agree they have created a security champions network from within the business
- Twice more likely to agree that the security organisation has formal support and authority from business leaders and executives
- 1.2 times more likely to agree they have the support and advocacy from the board
She posits that in terms of other outcomes, having a strong security culture is foundational to reducing the overall cybersecurity risk to organisations.
Many global and local breach publications estimate up to 74% of breaches include human elements, where people are involved in error, privilege misuse, use of stolen credentials, or social engineering. 2023 saw more human quantification vendors emerge, with tools and processes that take a data-driven approach to behaviour change, moving away from perfunctory, often unsubstantiated, security awareness and training, to Adaptive Human Protection.
“Changing behaviour has a direct impact on minimising the risks including the human element, which in turn reduces the overall cybersecurity risk to organisations,” concluded Budge.




