Quick… what’s a dirty little secret that most people would not want aired publicly? No… this is a business-related blog, try again. 😉 If you answered, “We were hacked, and it took our systems down long enough to impact our operations and those of our customers,” you’d be in good company.
At our most recent Executive Advisory Board meeting, one of our members lamented that while their team is quite advanced in terms of overall supplier relationship management, they are still frequently surprised when cyber disruptions happen at suppliers.
This week, during an event for our COO and CSCO communities, we surveyed attendees on whether they or their supply partners had been impacted by cyberattacks since the Russian invasion of Ukraine. We also asked if they are seeing a trend in this type of activity. It was an anonymous poll, but I suspect many of the leaders on the call chose not to reveal their situation. For those who did, the responses were telling.
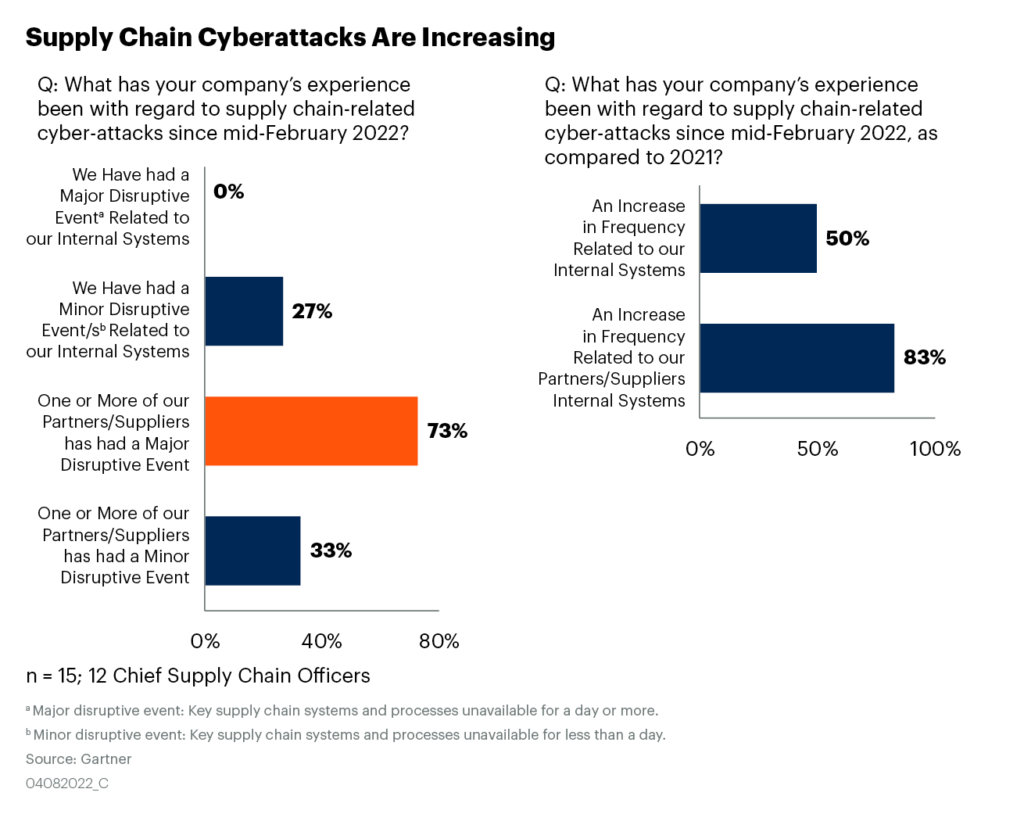
Nearly three-quarters of respondents had one or more of their suppliers experience a disruptive cyber event that took key processes and systems down for at least a day. More than a quarter had shorter-term disruptions to their internal operations. This level of cyber activity was an uptick for most when compared to the period prior to mid-February and the lead-up to the Russian invasion of Ukraine.
How should we respond?
At many companies, supply chain leaders are only granted the authority to execute CIO or chief information security officer (CISO) directives on cybersecurity. A challenge to this model is that often the weakest cyber links exist with suppliers and other external partners. CSCOs and their teams need to engage to ensure the extended value chain is protected, along with internal systems and assets.
Beyond governance issues, there are ROI-related decisions on the required response. One way to assess the amount of focus and resources that should be placed on extended value chain security is to treat this investment like any other type of risk mitigation or insurance policy. Gartner’s well-known risk management analyst, Paul Proctor, recently published a report on this topic (Use Value and Cost to Treat Cybersecurity as a Business Decision — Gartner subscription required). Here are some of the key findings from that research:
Organizations must stop investing in security tools and start investing in outcomes. A strategic vision for cybersecurity as a business decision is one that balances protection needs with desired business outcomes.
Technology and business drivers should influence how much is spent on a cybersecurity program and for what level of protection. This framing should be captured in a protection-level agreement (PLA) between the IT team and business leaders.
The PLA sets out the desired security and business outcomes and how the outcomes will be addressed by a set of controls that are consistent, adequate, reasonable and effective.
CIOs should not expect executive decision-makers to express their needs for protection in cybersecurity terminology. Instead, protection levels should be framed and influenced within the context of the following business drivers:
Business operations — Opportunities or decisions that put the organization more at risk
Regulatory demands — What PLAs are acceptable to the regulators?
Shareholders — Can the CEO stand in front of the TV cameras and defend the organization’s cybersecurity decisions to satisfy both customers and shareholders?
Partners — How many companies will not work with the organization because it is not appropriately secure?
Cyber insurance eligibility — What is necessary to obtain cyber insurance? Cost and requirements to obtain cyber insurance are trending up and are more stringent
Benchmarks — What are others doing?
Observable business impact — How much downtime or other material loss is being caused by security incidents? How can that be changed by stronger or weaker PLAs?
The first step in most remediation journeys is admitting we have a problem and then moving into the solution space. In line with that theme, we are excited to explore the topic of Secure Supply Chain with our global COO and CSCO community at an April 26 Leaders in Action event, co-sponsored by Mark Bakker and the team at HP Enterprise.
First published on Gartner Blog Network




