A smart contract is a type of blockchain record that contains externally written code and controls blockchain-based digital assets. When triggered by a specified blockchain event, a smart contract immutably executes its code and may result in another blockchain event.
Gartner predicts that smart contracts will become a critical component of the global digital infrastructure. Smart contracts will execute agreements that pertain to various digital interactions and/or transactions. As autonomous digital agents, smart contracts control the states of their corresponding digital/physical assets’ life cycle or enable middleware protocols to facilitate data sharing in multiparty processes.
However, smart contracts introduce novel vulnerabilities that can expand the cyberattack surface. Security and risk management professionals should assess risk and implement robust security controls when deploying smart contracts, especially in critical infrastructure. Gartner reviews smart contracts’ risk from multiple perspectives, including:
- Infrastructure security: The underlying infrastructure (such as public or enterprise blockchain platforms) usually exposes smart contracts to a unique set of vulnerabilities that require appropriate controls to mitigate risk.
- Contextual security: The functional context of smart contracts also affects how to ensure the correctness, safety and compliance with any relevant legal and regulatory requirements.
- Access control: Access control through ownership or roles is important to ensure privileged operations are performed securely either by humans or autonomously.
These perspectives are captured in the following security architecture framework:
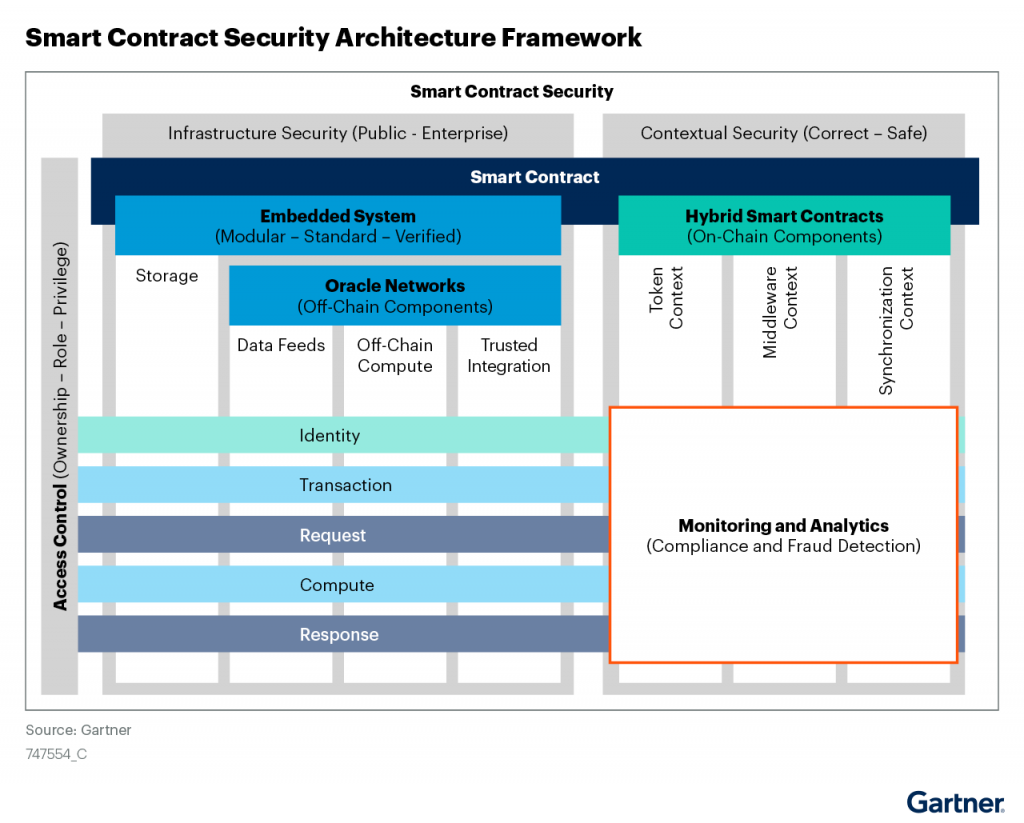
Source: Gartner 2021
Our key findings indicate that:
- Smart contracts behave as autonomous digital agents that control interactions or transactions in decentralized processes. While the logical model for smart contracts is almost the same, the physical implementation of smart contracts can vary significantly in different blockchain platforms.
- Smart contracts require a security model similar to embedded systems with simple, bug-free, and algorithmically correct code as well as modularized and isolated architecture. It is preferable to use ready-made, proven and contextually safe templates for smart contracts. This is important, considering that smart contract failure can have a major impact on digital and/or physical assets.
- Smart contracts’ access control mechanisms require careful design, as ownership or admin privileges can define who is able to govern and change the state of an asset. This is particularly important in the context of autonomy when the system switches to autonomous (self-administration) mode.
- Smart contract functional context may need additional measures for the correctness and safety of business logic. Contextual security requirements are more visible in complex hybrid smart contracts that combine both on-chain and off-chain services, such as using secure oracles for data feeds, off-chain computation, or trusted integration with enterprise systems.
To implement secure and safe smart contracts, security and risk management professionals should:
- Use verified and trusted templates for smart contracts development and carefully extend functionality as needed while keeping the code simple. Leverage formal verification tools where applicable.
- Consider modular smart contract architecture for complex use cases to minimize the blast radius of any failure as well as simplifying the maintenance and upgradability of your code.
- Implement robust embedded access control functions in smart contract code, enabling ownership and roles to manage privileges. This includes built-in functionality for self-administration scenarios in case your smart contract is configured to operate autonomously.
- Use secure oracle networks as a proven best practice to feed any off-chain data into their smart contract, implement trusted integration with off-chain systems/APIs, or implement off-chain computing services.
- Identify and mitigate their use-case contextual security risks. The process should include both known vulnerabilities as well as simulation or bounties to discover unknown vulnerabilities.
- This is to ensure the functions operate as intended for each use case, considering all external dependencies to prevent bad actors from gaming the system.
- Define smart contracts’ baseline behaviour and continuously assess deviations from the baseline that indicate malicious or anomalous behaviour using monitoring tools and analytics.
- This is to ensure security as well as compliance with regulatory requirements as applicable, especially for an organization that is involved in governing a smart contract or if smart contract vulnerabilities expose the organization to any type of risk.




