"A software supply chain attack occurs when a cyber threat actor infiltrates a software vendor’s network and employs malicious code to compromise the software before the vendor sends it to their customers. The compromised software then compromises the customer’s data or system."
National Institute of Standards and Technology, U.S. Department of Commerce
Such was the case when towards the end of 2020 Orion, an IT monitoring system from SolarWinds, was hacked by a group known as Nobelium. The SolarWinds hack, which was delivered by way of a software update, compromised the data, networks and systems of thousands of organisations, including private and public entities.
The incident revealed just how vulnerable computer systems are, and how interconnected enterprises are in the digital economy.
The what, why and when of software supply chain vulnerability
Jacob DePriest, deputy chief security officer at GitHub, explains that a software supply chain encompasses everything that goes into the delivery of an organisation’s software product, from initial development through to production. He adds that this includes code, binaries, and components from employees, third-party repositories, or package managers.
Open-source software grew from the desire of individuals and organisations to minimise dependence on proprietary software that is expensive, and for which the company has limited in its ability to innovate beyond what the vendor allows.
Open source software has grown in popularity, not only because it enabled organisations to test new ideas at a lower cost, but to pull talent, expertise and experience from a global community of developers, and potentially introduce innovation at a faster pace.
However, cautioned DePriest, this rapid development also comes with risks – developers may inadvertently inherit vulnerabilities from their open source dependencies, causing a ripple effect impacting the services and developers that depend on it downstream. The SolarWinds hack may well have relied on this premise.
Exploiting the vulnerabilities of a software supply chain
According to DePriest the software supply chain is susceptible to various risks, including unpatched vulnerabilities, innocent mistakes, and malicious attacks on dependencies.
He explains that supply chain attacks occur when bad actors purposely add malicious code to a component and ride the supply chain of that component to distribute the code to their targets. Attacks can happen well upstream from the main objective, say a dependency of a dependency. Attackers can use multiple methods, like inserting code as new committers, hijacking accounts, or compromising signing keys to impersonate official software.
He pointed out that developer accounts remain a prime target for social engineering and account takeover, making their protection one of the most important steps in securing the supply chain.

"To defend against these attacks, it's essential to move beyond basic password-based authentication. Embracing strong authentication and implementing 2FA significantly reduces the prevalence of compromised accounts. Ultimately, safeguarding developer accounts is the foundation for enhanced supply chain security, helping to ensure the integrity and reliability of the software ecosystem."
Jacob DePriest
Implications of a supply chain attack on organisations
DePriest warns that software supply chain attacks can have significant implications for organisations. These types of attacks can lead to data breaches, resulting in the exposure of sensitive information and customer data.
Financial losses may also occur due to operational disruptions, recovery costs, and potential legal ramifications, damaging the reputation of affected organisations and eroding customer trust and confidence.
He believes that cyberattacks will continue to rise.
"To keep up with the speed of threats, there must be a collective industry and community effort to secure the software supply chain: a partnership between the public and private sector, organisations and working groups focused on shared security goals and direct partnerships between companies," he explains.
He posits that success should be focused on supporting developer communities and ecosystems that design, build, and maintain the open source projects we all depend on.
Why build a secure software development ecosystem
DePriest says supply chain security has emerged as a critical focus within the open source community citing the exponential growth in the use of open source software.
"However, with this rise in popularity, nefarious actors have also emerged, exploiting user accounts, corrupting vital dependencies, and targeting vulnerabilities in major open-source projects," he cautions.
He cites events like SolarWinds and Log4j as reminders of the importance of securing critical software.
"We’ve seen how just one or two lines of vulnerable code can have a major impact on the health, safety, and trustworthiness of entire systems."
Jacob DePriest
Caveat Emptor of open source
While acknowledging the continued relevance of open source software, he concedes that keeping on top of open source vulnerabilities can be extremely time-consuming. He also agrees that a collective effort from the tech industry, private sector, and community is crucial to secure the software supply chain.
"By supporting open source maintainers and providing the necessary resources, we can enhance the overall security of the software ecosystem," he explains. "Everyone has a role to play in fostering successful communities, ensuring that the code used daily is both trusted and secure."
The good news – sort of
In the 2022 Gartner Thriving Amid Complexities Supply Chain Survey, respondents revealed the extent to which organisations are taking the threat of supply chain risks.
Figure 1: Supply Chain Cybersecurity Protection Deployment Rates
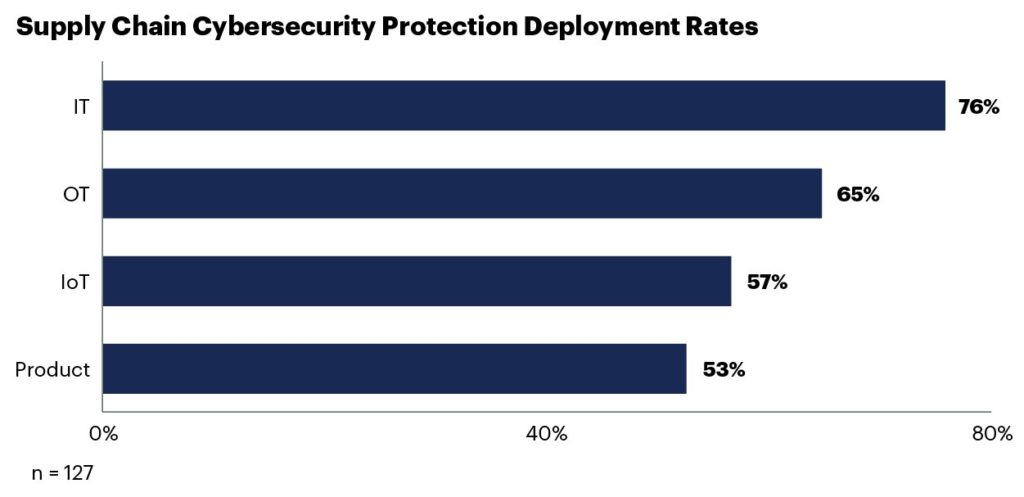
Source: 2022 Gartner Thriving Amid Complexities Supply Chain Survey
However, positive the trends are, Gartner warns that it is also observing an inflated sense of supply chain cybersecurity among respondents.

"If CSCOs are going to face the threat of increasing cyber risk head-on, they must continue to educate themselves, avoid complacency and take action. They must close the confidence/capability gap," said Mark Atwood, managing VP, Gartner Supply Chain.




