The Forrester 2021 State of Enterprise Breaches report revealed that in the past 12 months, organisations were breached an average of three times.
According to Forrester’s senior analyst, Allie Mellen, regions that hesitated to address challenges with business alignment were breached at a higher rate than those that addressed such challenges early on.

“Security decision-makers are more concerned about external attacks than any other attack vector, at 47%. Breaches come in various ways, however, and are much more evenly spread in frequency among external attacks, lost/stolen assets, internal incidents, and third-party providers.”
Allie Mellen
And it is not that organisations are not doing anything about it. Gartner says that over 90% of cybersecurity functions have an awareness programme. However, 69% of employees admit to intentionally bypassing cybersecurity guidance and 82% of breaches involve the human element.
Network lateral movement, or simply lateral movement, is a technique used by cyber attackers to further deepen their penetration into a network. The idea is once an attacker has entered an endpoint, say your laptop or mobile device, to extend access to the company network, through other hosts or applications that the organisation uses.
FutureCISO spoke to Jonathan Jackson, director of sales engineering for APJ at BlackBerry to talk about countermeasures against this rising use of lateral methods to penetrate enterprises.
What is lateral security in the context of today's business environment?
Jonathan Jackson: At its core, lateral security refers to securing businesses’ data from attackers who spread from one entry to the rest of its network. This technique enables attackers to move laterally undetected within a network. Lateral security is important as over 60% of SMBs who have suffered a cyberattack have gone out of business within six months.
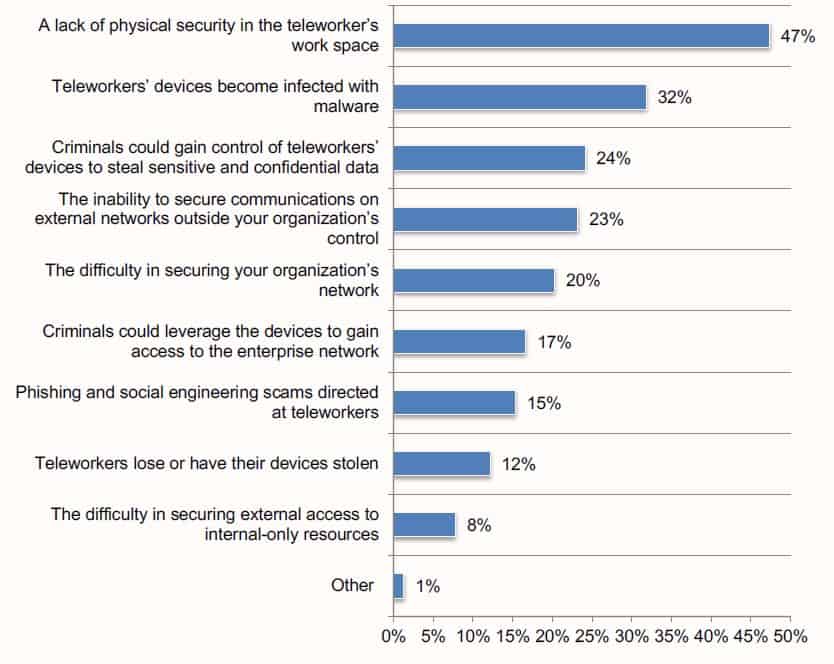
Source: Cybersecurity n the Remote Work Era, Ponemon Institute 2020
Threat actors will carry out lateral attacks from an initial mapping of networks to direct infiltration through illegally accessing the organisation’s credentials. Businesses need to understand how threat actors are carrying out lateral movement attacks and have the right defences such as firewalls in place to stop intruders from gaining access.
Are CISOs aware/familiar with securing internal APIs (as used in containers)?
Jonathan Jackson: CISOs should absolutely be aware of securing internal and external APIs, as this defines the software and application stack being used by businesses today. Traditionally, the industry has been focused on securing external APIs because that is how people typically gain access to information from outside one’s network.
However, when malicious users or an insider threat gains access to your network from the inside, then having to secure internal APIs will be just as important. It will be a CISOs responsibility to keep internal APIs secure and do that well.
How do I map (do I need to?) secure scale-out architectures?
Jonathan Jackson: Understanding scale on architectures is crucial as it pertains to the ability to provide the capability of your workloads, workflow and applications. Not only is it important to map secure scale-out architectures, but it is also necessary to map scale-back architectures.
Dialling up as well as dialling down. Cloud applications are built with elastic scaling in mind so as your workload decreases and you no longer require the extra capacity, you can scale back. Organisations will need to understand the design of cloud applications so they can scale accordingly.
Is a protection platform a better approach to securing the enterprise end-to-end? If not, what are my top 3 options or criteria for deciding the right approach for my organisation?
Jonathan Jackson: Although protection platforms promise a lot, over time they begin to exert a stranglehold on their customers, stifling competition and innovation.

“Unlike integrated platforms that support discrete functional areas of the enterprise, cybersecurity should be systemic, supporting and protecting every function, application, device, and person – which is too big a job for one platform.”
Jonathan Jackson
Optimal security requires a small, manageable set of complementary technologies to get the job done. It is important to have defences that can mirror the infinitely variable approach and tactics of today’s attacks.
We need to focus on multiple high-performing security models that overlap to fill the gaps and deliver the right balance of business risk and fail-safe capabilities for each organisation.




