The Imperva Research Labs of nearly 27,000 scanned databases discovered that the average database contains 26 existing vulnerabilities. The five-year longitudinal study estimates that 46% of all on-premises databases globally are vulnerable to attack.
More than half (56%) of the Common Vulnerabilities and Exposures (CVEs) found were ranked as ‘High’ or ‘Critical’ severity, aligned with guidelines from the National Institute of Standards and Technology (NIST).
This indicates that many organizations are not prioritizing the security of their data and neglecting routine patching exercises. Based on Imperva scans, some CVEs have gone unaddressed for three or more years.
According to Elad Erez, Imperva chief innovation officer opined that too often, organizations overlook database security because they’re relying on native security offerings or outdated processes.
“Although we continue to see a major shift to cloud databases, the concerning reality is that most organizations rely on on-premises databases to store their most sensitive data.”
“Given that nearly one out of two on-prem databases is vulnerable, it is very likely that the number of reported data breaches will continue to grow, and the significance of these breaches will grow too,” he continued.
Regional observations
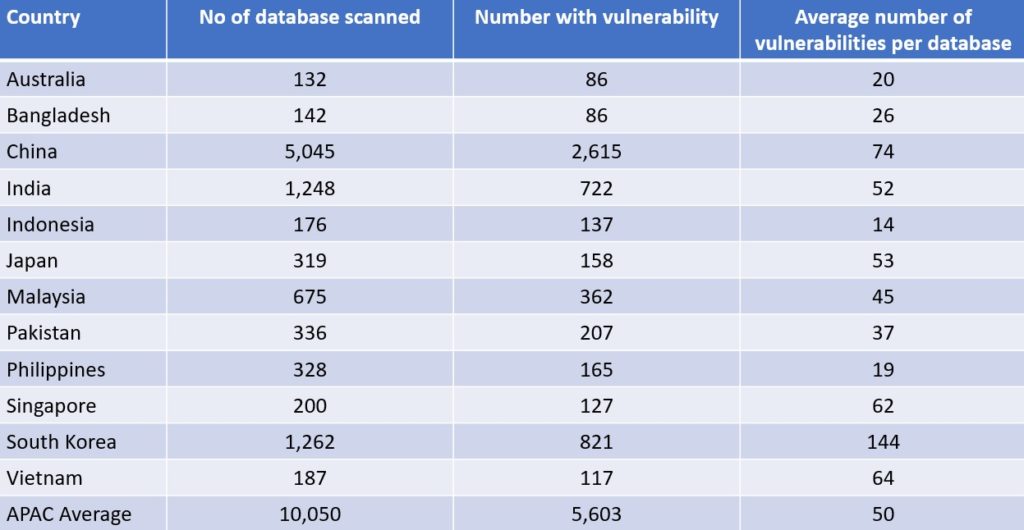
Erez commented that in Asia, database security and access management were traditionally very segmented in organizations. "Different people or teams had access to each database and were usually solely responsible for that database's security and updating. This caused huge problems, as not every system is managed or secured with the same process or rigour, thus allowing for differing security vulnerabilities," he continued.
He added that beyond this issue of unclear ownership of database security that causes organisations to defer efforts in this regard, some firms have the perception that data security is “hard” to solve and thus it gets pushed to the bottom of the agenda.
"Universally we find the security of data is underfunded and not a priority. This new research suggests that organizations aren’t aware of just how vulnerable those on-prem environments are, which is a sobering reality and speaks to the current state of data security. We hope this research will shed necessary light on the risk these common vulnerabilities present and just how exposed organizations are," he added.
New opportunities
The unprecedented number of database vulnerabilities offers attackers a vast landscape of opportunity.
For non-publicly accessible databases, attackers can use a range of tools such as SQL injections (SQLi) to exploit vulnerabilities in web applications that are connected to a database. This remains a consistent business threat as nearly 50% of breaches in the past several years originate at the application layer. Separately, attackers may use phishing and malware to gain a foothold in the internal network and then move laterally to the vulnerable database.
When it comes to public databases, the threat is even greater as exploiting them requires even less effort. Attackers can search for vulnerable targets through tools such as Shodan and acquire exploit code through repositories like ExploitDB which hold hundreds of points of compromise (POC) codes. From there, the attacker can run the exploit from anywhere since the database has a public IP address.
The way forward
Given the staggering number of vulnerabilities that exist in on-premises databases, it should come as no surprise that the number of data leakage incidents has increased 15% over a 12-month average.
An analysis of data breaches since 2017 shows that a majority (74%) of the data stolen in a breach is personal data, while login credentials (15%) and credit card details (10%) are also lucrative targets.
Erez said organizations are making it too easy for the bad guys. He added that attackers now have access to a variety of tools that equip them with the ability to take over an entire database or use a foothold into the database to move laterally throughout a network.
“The explosive growth in data breaches is evidence that organizations are not investing enough time or resources to truly secure their data. The answer is to build a security strategy that puts the protection of data at the centre of everything,” concluded Erez.




