The frequency of ransomware attacks has increased dramatically over the past year, with most of these costly attacks targeting businesses.
In the past 12 months, Barracuda researchers reported a huge 64% uptick in the number of ransomware attacks compared with the previous year, with attacks on corporations, including infrastructure, travel, financial services, and other businesses accounting for more than half of all attacks (57%) between August 2020 and July 2021, a 39% increase since last year.
According to the study, municipalities are the second most attractive target for ransomware hackers (16%), followed closely by education (13%) and healthcare (13%).
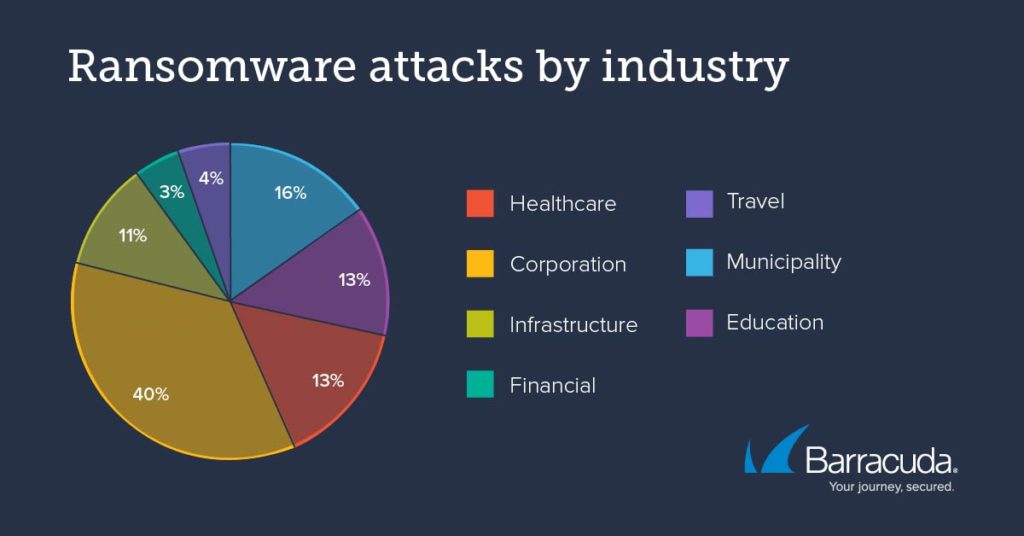
And while results show that cybercriminals are still heavily focused on organisations based in the United States (44%), researchers noted that ransomware is a pervasive issue across the globe with 30% of attacks targeting organisations in Europe, the Middle East and Africa (EMEA), 11% targeting Asia-Pacific countries, 10% in South America and 8% in Canada and Mexico.
Modus operandi
Ransomware attacks see cybercriminals using malicious software, delivered as an email attachment or link, to infect the network and lock email, data, and other critical files until a ransom is paid.
These evolving and sophisticated attacks can cripple day-to-day operations, cause chaos, and result in financial losses from downtime, ransom payments, recovery costs, and other unbudgeted and unanticipated expenses.
Barracuda researchers say these attacks are becoming even more deadly as cybercriminals level up their tactics and attack patterns, and with it, their ransom payment demands. Today, the average ransom ask per incident is over US$10 million, with only 18% asking for less, and a huge 30% asking for more than US$30 million per incident.
Attack pattern
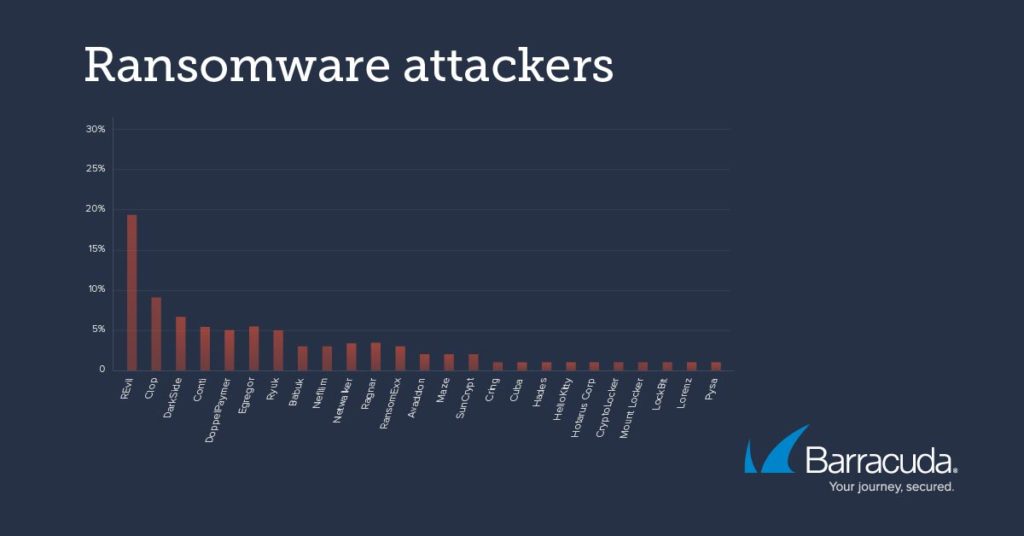
The analysis also revealed that many of these attacks are being led by a handful of high-profile ransomware gangs, including REvil, which was responsible for 19% of attacks, and DarkSide (8%).
When it came to evolving attack patterns, researchers found that instead of just relying on malicious links and attachments to deliver ransomware, current attacks see cybercriminals using phishing attacks to steal credentials, before using them to compromise the victim’s web applications, such as web portals or software-as-a-service (SaaS) apps, to introduce ransomware and other malware onto the victim’s system, infecting the network as well other users of the application.
Barracuda also saw a rise in hackers using double extortion schemes, where after stealing sensitive data from their victims, they demand payment in exchange for promising not to publish or sell the data to other criminals. Since criminals cannot be trusted, victims who pay are often contacted several months later and asked for another payment to keep the stolen data secret. Some ransomware criminals will accept payment but sell the data anyway.

Barracuda systems engineer manager for Asia-Pacific Mark Lukie commented that ransomware is an issue that is not going away anytime soon, and can affect businesses of all sizes, as attackers often start with small organisations that are connected to the larger targets and then work their way up towards bigger paydays in the future.
To safeguard against attacks, Barracuda urges businesses to do everything they can to prevent credentials loss, like training staff for email security awareness and implementing anti-phishing capabilities in email. The company recommends implementing watertight security solutions to secure web applications; taking a zero-trust approach to secure access and endpoint security, backing up data and enabling a secure data protection solution to recover critical data in the worst-case scenario.
“Prevention is always better than remediation, so making sure that you are doing everything you can to protect against these increasingly sophisticated and costly attacks is the best way you can be confident in saying no to ransomware criminals,” suggested Lukie.




