The IBM Cost of a Data Breach Report 2021 noted that the average total cost of a data breach stood at US$4.24 million, up 10 from the previous year. Factor in remote work and the average cost goes up further to US$4.96 million. It also took longer to identify breaches in 2021 with an average of 287 days, seven days more than 2020.
Why does it take on average 287 days to identify and possibly fix the breach? Factors that weighed on the length of time to identify and contain included the type of data breach, attack vector, factors such as the use of security AI and automation, and cloud modernization stage.
As one expert commented: we spend too much time overanalysing choices we make about security, looking for that perfect protection that just simply does not exist.
In this article, we focus our attention on extended detection and response (XDR).
First coined by Nir Zuk, chief technology officer at Palo Alto Networks, XDR is a unified security and incident response platform that collects and correlates data from multiple proprietary components. The platform-level integration occurs at the point of deployment rather than being added in later.
This consolidates multiple security products into one and may help provide better overall security outcomes.
Asked why an organization would consider deploying XDR, Kerry Singleton, managing director, cybersecurity, Asia Pacific, Japan, China (APJC), Cisco, added that XDR goes beyond the typical platform-based security. It's an evolution of the existing threat detection and response solutions.
“The role of XDR is to bring these different components together, provide the capability around analytics and detection, and provide integrated threat detection,” he added. “XDR solutions also look at how we remediate issues, such as alerts that come in, as well as investigate previous activities and conduct threat hunting.”
The rising threat of third-party risk
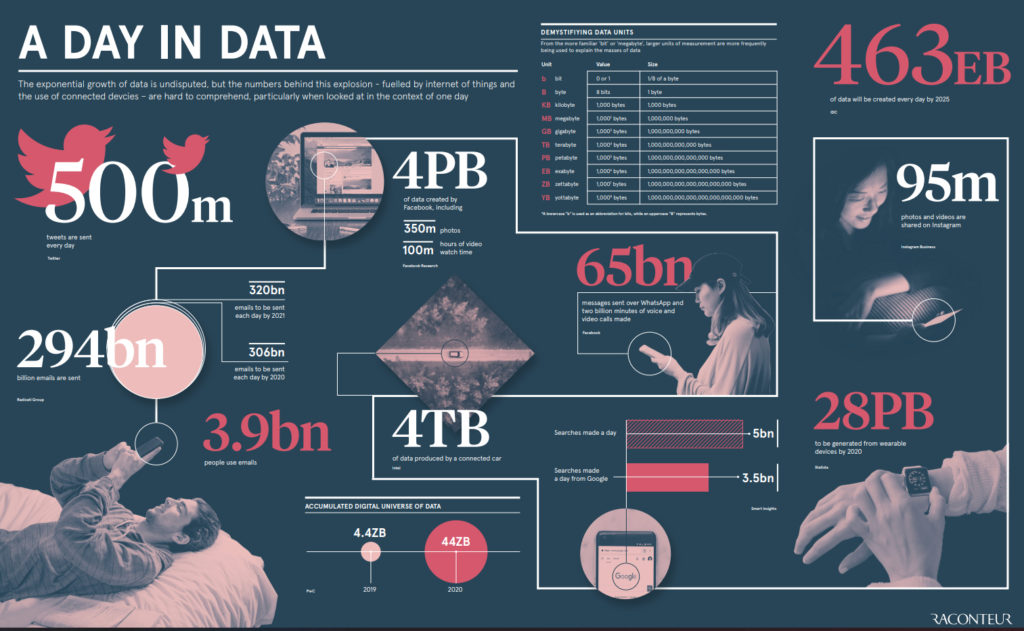
By 2025, it’s estimated that 463 exabytes of data will be created each day globally. Acquiring, curating, storing, and protecting that data is one of the main preoccupations of the office of the Chief Information Officer and the Chief Information Security Officer.
Given the extent to which enterprises connect to customers, business partners, suppliers and employees, it is important to ensure that this expanded, near borderless network, remain protected and secure.
Singleton says XDR technology possesses all the technical capabilities and allows us to strengthen interaction with third-party solutions. While XDR delivers some of the capabilities of Security Orchestration, Automation and Response (SOAR), he believes XDR serves as a better alternative as compared to SOAR in some key areas.
“First, the level of turnkey integration is much higher and does not require extensive labour or intensive calibration to get it up and running and operational. Secondly, XDRs focus solely on threat detection and incident response and have much better detection and analysis built-in. And third, they are generally built on cloud-native architectures, so you can deploy them very rapidly,” he continued.
What XDR protects
XDR improves incident response time and offers organisations better overall security outcomes including 6 to 10 hours saved per incident from reduced response time,72% reduction of dwell time from eliminating investigation tasks and shortening of time spent on threat hunting and staying compliant and enhanced visibility across the network, enabling the detection of threats across the private network, public clouds, and even in encrypted traffic.
What to look for in XDR
Singleton suggests that when evaluating an XDR solution, decision-makers should look at three things:
- Does the solution bring together many different control points across multiple data sources?
- Does it make detection smarter and faster with machine-learning analytics?
- Does it reduce dwell times through easier investigation, faster response, and more automation?
“The three elements should all be present in balance for an XDR solution to achieve its purpose. As with all investments, one must look at the costs. Security teams should look for an XDR solution that can lower the overall total cost of ownership for the solutions that they're integrating, which means they’re also getting more value out of their existing investments,” he continued.
The zero-trust factor
On the question of zero-trust, Singleton commented that “from a Cisco perspective, a zero-trust approach to security is simply understood by protecting 3Ws – the workforce, workplace and workloads. This enables organizations large and small to address the full spectrum of vulnerabilities - identity, applications and network threats.”
He concluded by noting that beyond detecting threats, XDR takes things further by identifying malicious intent with machine-learning-based analytics across a variety of data sources and vendors.
“What becomes important is reducing the number of vendors, having the integration between products and the XDR platform. All these factors become important in the decision-making process,” he concluded.
Click on the PodChat player and listen to Singleton describe in detail the operational value of XDR, where it fits in an organization’s zero-trust strategy, and what to look for when evaluating XDR solutions.
- Why is there a need for XDR? What are the primary functions of an XDR system?
- Is SOAR (Security Orchestration, Automation, and Response) a better alternative to XDR?
- How does XDR improve security staff productivity?
- What should the IT/security team look for when evaluating an XDR solution?
- Where does XDR fit in the zero-trust strategy?




