Privileged access management (PAM) is a high-priority cyber defence capability. PAM requires a comprehensive technical strategy based on a zero-standing privilege (ZSP) operating model. Key success factors include visibility and control of privileged accounts across all assets.
Traditional PAM controls such as credential vaulting and session management are essential, but not sufficient. Adopting just-in-time privilege approaches and managing machine identities are imperative while implementing privilege task automation and advanced analytics are preferred.
Broader coverage of PAM controls for cloud platforms, DevOps, microservices, robotic process automation (RPA) and operational technology scenarios requires robust secrets management (with secretless brokering) and cloud infrastructure entitlement management (CIEM).
PAM is applicable to all local and remote human-to-machine and machine-to-machine privileged access scenarios. This makes PAM a critical infrastructure service due to risk aggregation related to storing sensitive credentials/secrets as well as performing privileged operations in different systems. As such, PAM capabilities require thoughtful high-availability and recovery mechanisms.
“PAM should be prioritized as a cyber defence mechanism. It plays a key role in enabling zero trust and defence-in-depth strategies that extend beyond mere compliance requirements. Some organizations may choose to deploy a minimum set of PAM controls to meet their compliance obligations in response to an audit finding.
“However, these organizations remain susceptible to attack vectors such as service accounts, privilege escalation and lateral movements. Although minimalistic controls are better than nothing, expanding the PAM control coverage can mitigate a broader number of risks to defend against complex cyberattacks.”
The figure below shows the key steps to develop/enhance PAM architecture strategy:
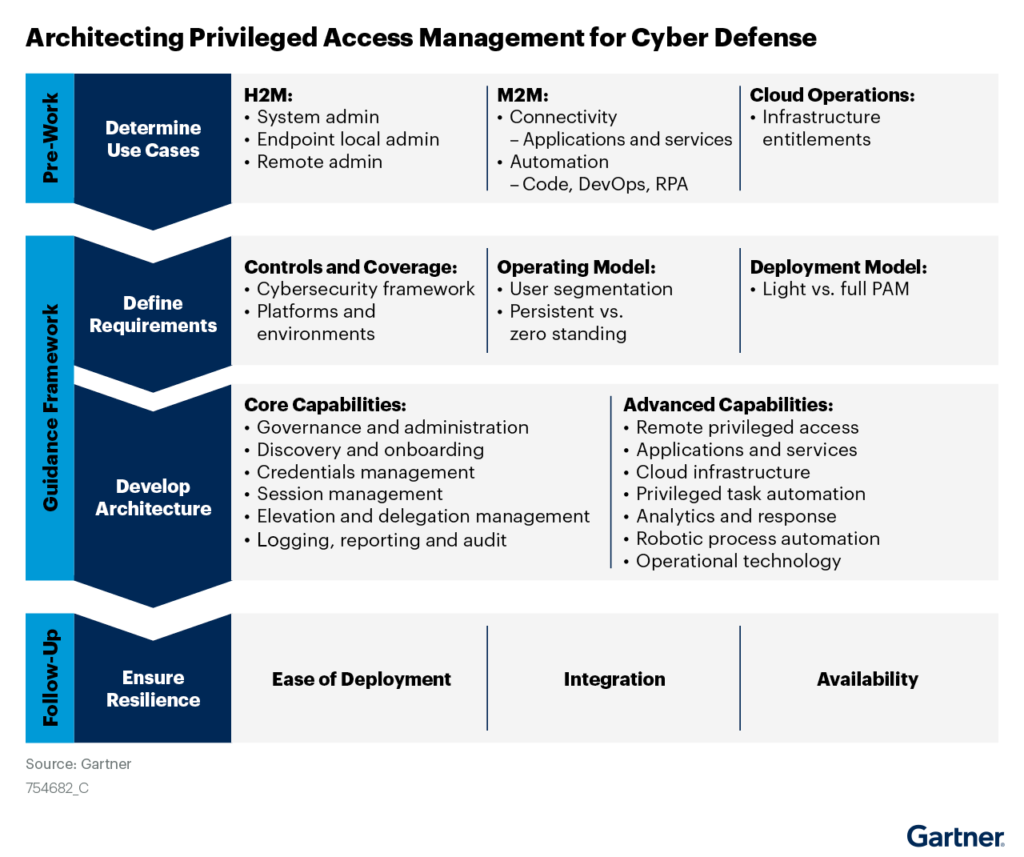
Security and risk management technical professionals should:
Develop a risk-based approach to plan and implement or enhance PAM controls and their breadth of coverage by creating a PAM control coverage matrix that aligns with the organization’s cybersecurity framework.
Implement core PAM capabilities by deploying solutions that cover intended use cases while driving a zero standing privilege operating model. That includes governance, discovery, protection, monitoring, auditing, and just-in-time privilege elevation and delegation.
Implement additional PAM capabilities by extending the deployed solutions or integration with other security management tools. That includes remote support, task automation (especially in DevOps pipeline and infrastructure-as-code use cases), change management, vulnerability assessment and remediation, as well as secrets management, secretless brokering, and cloud infrastructure entitlement management. Integrate PAM solutions with security information and event management (SIEM) and IT service management (ITSM) tools.
Architect resiliency for the PAM solution by using high-availability design and advanced disaster recovery processes, such as a hot or cold site versus simple local backup and recovery. Also, plan for recovery scenarios using reliable break-glass approaches.
First published on Gartner Blog Network




