As Asia inches to recovery from the pandemic, focus will shift back to Industry 4.0 sometimes referred to as the digitalisation of industries. Shifting businesses and enterprises into an intelligent and connected virtual space is no longer an option but a necessity to survive, primarily due to the added pressure brought about by the pandemic.
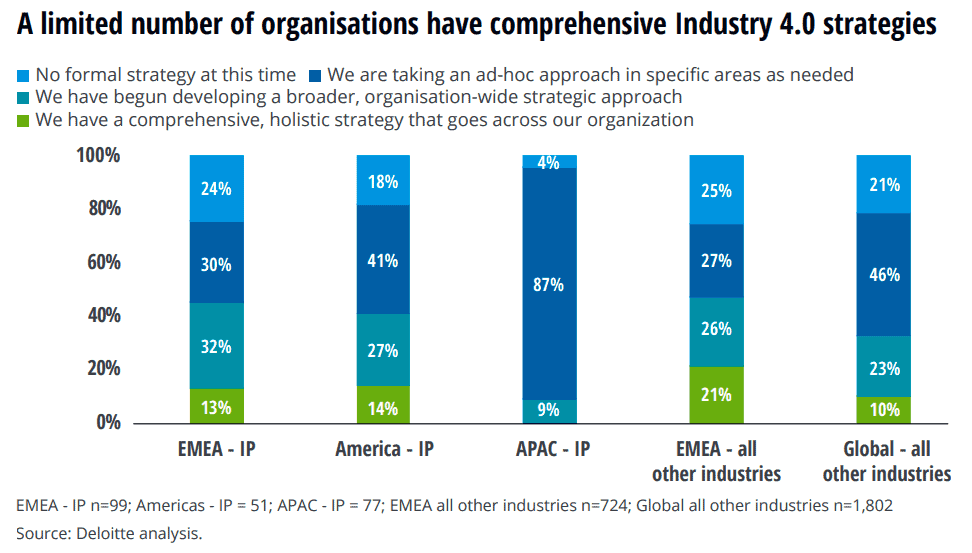
A Deloitte study, The Fourth Industrial Revolution, proved this trend with a great majority (96%) of companies from Asia Pacific (APAC) revealing that they have conducted an audit to find opportunities for Industry 4.0, significantly higher compared with the global average of 51%.
Stephan Neumeier, managing director for Asia-Pacific at Kaspersky says Asia Pacific’s level of digitalisation is still in its early stages until the pandemic forced everyone to reconsider their operational practices.
“Contrary to popular belief that Industry 4.0 is a high-level topic confined in the four corners of a board room, this revolution has the consumer at its core. This, alongside breakthroughs like Big Data, Internet of Things (IoT), 5G, are here to create a customised future,” he further adds.
Threats in APAC’s manufacturing industry
Several start-ups across the world, aware of the demand, have since kicked off their mass customisation practices. Consumers can now have their own names on the sole of their shoes, get bespoke necklace, as well as better-fitting body implants, personalised doses of medicines, and more.
While these are proofs of the power of technology when harnessed correctly, the flexible and highly-connected manufacturing process also opens a wider attack surface for cybercriminals. The latest report from Kaspersky for industrial automation systems showed that Asia and Africa are the least secure globally during the first six months of 2020.
Top rankings not to be proud of
Asian regions occupy four out of the top five positions in the regional rankings based on the percentage of Industrial Control Systems (ICS) computers which were almost infected in the first half of the year.
Southeast Asia recorded the highest percentages, leading in several ratings:
- percentage of ICS computers where malicious activity was blocked – 49.8%
- percentage of ICS computers where internet threats were blocked – 14.9%
- percentage of ICS computers where malicious email attachments were blocked – 5.8%
Percentage of ICS computers on which malicious objects were blocked by regions of the world
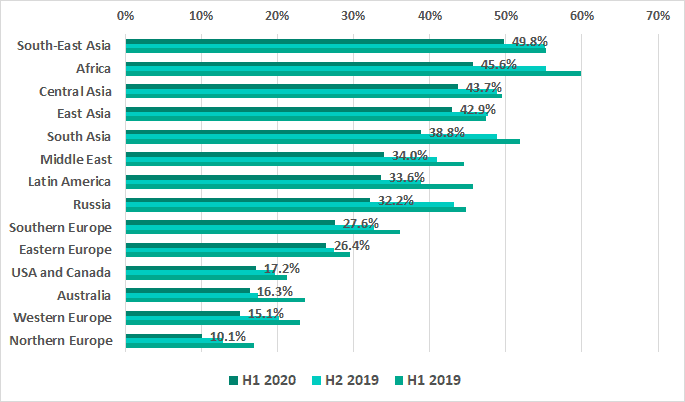
Source: Kaspersky 2020
Africa comes second while Central, East, and South Asia follow closely at third, fourth, and fifth places respectively.
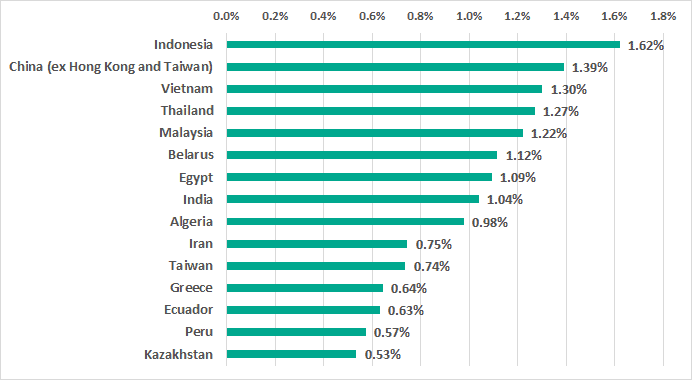
In terms of ransomware, regions in Asia still led with a noticeable margin in the regional rating. Over half of the countries in the top 15 ranking are from APAC.
TOP 15 countries and territories by percentage of ICS computers on which ransomware was blocked by Kaspersky in H1 2020
Neumeier said he is not surprised that ICS computers in Asia Pacific were exposed to the highest number of cyber threats as the region is well on its way in building a customer-centric future.
“Smart systems and automated productions require in-depth, intelligent defences to foil malicious disruptions, with possible aftermaths that can cross from the virtual to the physical realm. To avoid grave circumstances, a secure-by-design approach is necessary. Cyber immunity against attacks should be ingrained at the very fabric of the present and the future industrial systems,” he added.
Singapore use case
An example of a secure and beneficial application of Industry 4.0 is that of the Singapore Aquaculture Technologies’ (SAT) first smart floating fish farm. A first in Singapore and is expected to produce 350 tonnes of fish annually, the S$4 million aquaculture facility is set to cater to the needs of Singaporeans for quality fish while also addressing the challenges posed by climate change that have resulted in declining fish populations.
By using innovative advanced predictive analytics such as machine learning and video analytics, SAT is able to predict potential biomass growth and prevent the outbreak of diseases, reducing fish mortality. This also paves the way for scalable, highly flexible and above all environmentally efficient aquaculture across the entire value chain.
Suggestions for protecting ICS environment from malicious attacks:
- Provide your staff with basic cybersecurity hygiene training, as many targeted attacks start with phishing or other social engineering techniques. Conduct a simulated phishing attack to ensure that they know how to distinguish phishing emails
- Provide your SOC team with access to the latest threat intelligence (TI).
- For endpoint level detection, investigation and timely remediation of incidents, implement EDR solutions
- In addition to adopting essential endpoint protection, implement a corporate-grade security solution that detects advanced threats at the network level at an early stage
- Make sure you protect industrial endpoints as well as corporate ones