The Australian Government’s Annual Cyber Threat Report 2022 reported that losses from business compromised email (BEC) scams are up 21% from the previous year, reaching A$98 million, with the national average loss per successful BEC exceeding A$64,000. The report noted that “despite the best efforts of law enforcement agencies, only a small fraction of BEC financial losses are ever recovered.”
A business email compromise is a form of phishing attack where a criminal attempts to trick a senior executive (or budget holder) into transferring funds or revealing sensitive information. Because BECs are often sent to a target, the message may look legitimate.
ResearchAndMarkets.com estimates the global BEC market – organisations offering solutions to combat BEC – will reach US$1.1 billion in 2022, and more than double to US$2.8 billion by 2027.
The firm says the use of free, open-source, and pirated email security software and the high cost associated with the deployment of BEC solutions are expected to hinder the market growth.
So, what else is new? FutureCIO reached out to Sundaresan Kanappan, vice president of high growth technologies for Tech Data Asia Pacific & Japan, on how emails continue to be one of the most popular vectors of attack.
Emails have been around since the 1970s. Given the many other ways to communicate with others, why do emails continue to be popular as a business communication tool?

Sundaresan Kanappan: Today, with the easy availability of numerous applications, there is an increasing shift towards apps which provide convenience via collaboration and messaging options.
However, email is ubiquitous and is essentially a standard communication format that is widely used and accepted by the virtue of it having almost zero barriers to entry and its reach. Email permits elaborate and detailed communication, which is difficult in applications. Moreover, emails are now accepted as legal documents on many occasions.
Another reason why emails are still popular is the accessibility aspect since emails do not require VPN (virtual private network) or workplace access. Emails are also evolving with new functionality — such as collaborative emails — to keep up with current needs.
We anticipate that email will continue to be popular and that security solutions will continue to mature and provide the depth and breadth of functionality that security teams require.
From a security and privacy perspective, are most organisations in Asia observing best practices when it comes to email use?
Sundaresan Kanappan: Organisations are becoming more aware of the risks associated with email security and privacy but there still is a long way to go since a piecemeal approach to security will never work.
One of the key issues we see is that due to the overuse of emails, exposure levels are increasing. On average, everyone receives about 100 emails per day, with 300 billion emails sent and received globally, daily.
Implementing strong email defences is paramount – this will allow organisations to stop malware threats and tackle phishing emails. Having a secure email gateway whether deployed as cloud services, on-premises or through a hybrid model will be effective in tackling spam, graymail or other harmful emails.
It is important for organisations to have their emails encrypted, encourage better password management practices, use two-factor authentication, implement endpoint anti-virus protection across all work devices and most importantly educate employees about phishing, ransomware, CEO Fraud and Business Email Compromise (BEC) red flags.
Security management for emails is also a complex activity in today’s world and organisations are forced to use many tools to secure email communications.
Per Osterman Research, organisations remain vulnerable to breaches through email. Despite all the technologies and expertise available today, including claims of protection by cloud service providers, why do email attacks persist and why are success rates high?
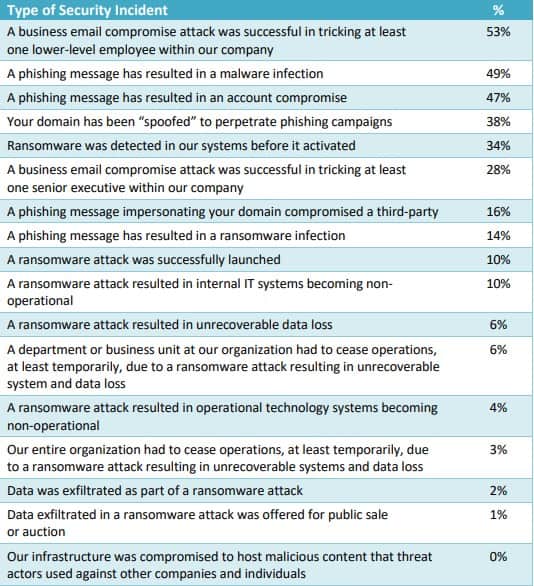
Source: Osterman Research 2021
Sundaresan Kanappan: Lack of cybersecurity awareness is one of the key accelerators of persistence in email attacks. Unprotected endpoints are also a major security concern with remote working becoming more common, since the employees’ computers may not be consistently protected by an organisation’s perimeter-based defences, leaving them more vulnerable to cyber threats.
Based on our observation, what’s needed is to drive awareness and the right adoption and implementation of technologies. Given the lack of cybersecurity skills about the technical skills possessed by domain experts, there needs to be a strong focus on developing skills.
Conducting effective security awareness training is an ideal way to guard against email attacks and other cyber threats.
This is where a Centre of Excellence (CoE) can play a vital role, bringing together experts from different disciplines through a shared facility which provides training and further enablement opportunities for customers.
A CoE which is well-established can help partners enhance their skills, optimise their operations, and increase their speed to market so they can capture new business opportunities.
What are contributing factors to this success rate in terms of breaches via email?
Sundaresan Kanappan: Today, attackers are coming up with innovative ways of using email-based cyberattacks, given the growing technology use across organisations and that emails have become essential to business communications.
In fact, based on MailGuard’s research, email is the number one vector for cyberattacks, with 91% of them starting with an email. According to IBM’s Cost of a Data Breach Report 2022, the global average cost of a breach is now US$4.35 million.
Security vendors keep harping on the importance of layered approaches to security. Can vendors guarantee that with a layered approach, even a multi-layered approach, breaches via email can be significantly reduced to near zero?
Sundaresan Kannappan: There is no single, standalone security measure that will guarantee the reduction of data breaches via email to near zero. This is as the nature of the industry means that new, sophisticated, and targeted attacks are being created every day. As breaches can come from legitimate but compromised accounts, or even from a vendor, stopping every threat is impossible.
What businesses need to do is deploy a multi-layered security stack to keep their ICT infrastructure and assets fully protected. Gartner predicts that by 2024, organisations that adopt a “cybersecurity mesh” architecture will reduce the financial impact of individual security incidents by an average of 90%. This shows that while cybersecurity can be enhanced, it is challenging to achieve a reduction to near zero.
The final aspect of security is the human factor – where mindsets and behaviours around security need to be continuously improved via education and awareness. This combination of technology with behaviours is probably our best bet in realising near-zero incidents.
Can and should vendors take responsibility for successful breaches under their watch?
Sundaresan Kanappan: There is a general belief among IT professionals, that vendors are well-informed in managing all areas of their cloud-based email services, whether it is compliance requirements or security. This misunderstanding leads to major gaps in cloud compliance and security coverage when those IT professionals don’t manage their end of the collective responsibility model.
As such, a collective approach is the best way forward, by being aware and acting on the various elements of one’s responsibility, be it an end-user, IT professional or vendor.
Going forward, how should CIOs/CISOs reframe their email security strategy to further improve the protection of users and the company?
Sundaresan Kanappan: A best practice is to adopt a multi-layered approach to email security, as no single vendor can defend against every threat. As such, if a business is using Microsoft 365, even with Defender, they should still deploy an additional specialist layer of email security to enhance their protection. Experts refer to this as a “defence-in-depth” approach.
Additionally, businesses must take a holistic approach to their email security, like password management and best practices, mandating multi-factor authentication, and investing in cyber awareness training for their workforce.




