What is the impact of the immediate shift to remote work on network security infrastructure? How has the experience affected hybrid workforce network security strategies with the realization that work is an activity, not a place?
A new report from Palo Alto Networks, The State of Hybrid Workforce Security 2021 report, concluded that cloud-delivered network security is important:
- 94% of people are considering a hybrid workforce model in the next 12 months.
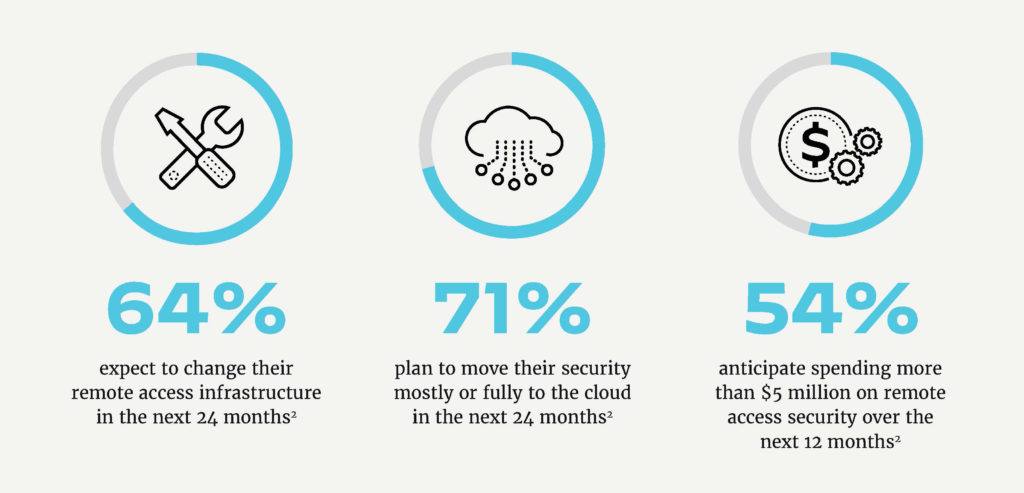
- 71% of people are planning to move security mostly or fully to the cloud in the next 24 months.
- 54% of people anticipate spending more than US$5 million on remote security in the next 12 months.
This report highlighted several priorities that network and security professionals have as they look to secure their organizations’ hybrid workforce.
Hard Decisions for Network and Security Teams
As network and security professionals who are always in a high stakes game of whack-a-mole, but based on the discovery of this survey, maintaining comprehensive network security is now their key challenge.
51% of survey respondents stated they have difficulty in maintaining comprehensive network security. Perhaps what’s even more concerning is that 61% of respondents noted they struggle to provide the necessary remote security to support work-from-home capabilities.
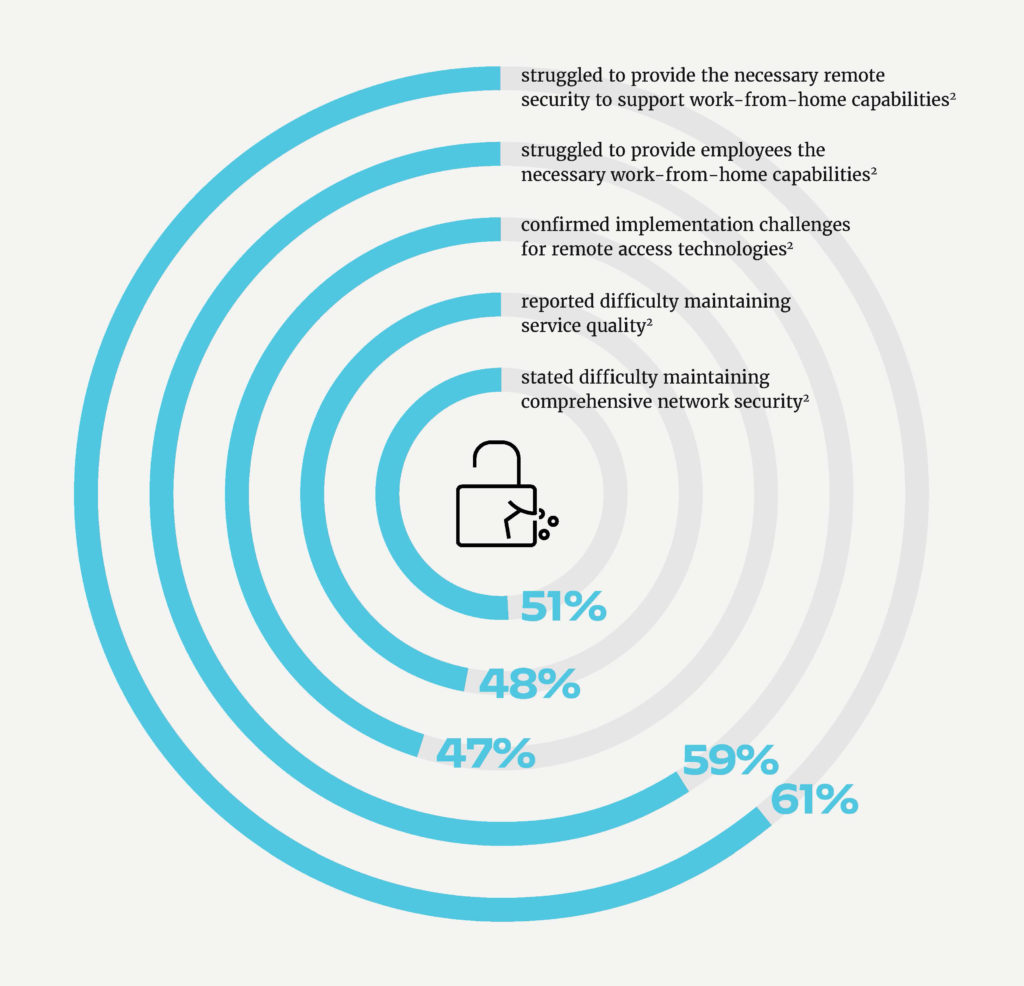
At the beginning of the pandemic, most organizations’ immediate concern was how to stay running and keep people working even if they couldn’t return physically to the workplace. The survey noted that this immediate shift to remote work turned network access and network security into equally high, yet competing, priorities for network and security professionals. Ultimately, network access emerged as the winner.
Many leaders fear that shortcuts were taken that now put their organizations at higher risk. 48% of organizations admitted to compromising security and increasing security risk through lax enforcement of security policies and allowing employees more leeway than what was normally acceptable. 53% of organizations that prioritized remote access over security are now exposed to significant security risks from unchecked acceptable use policy violations and unsanctioned application usage.




