The Ransomware Index Report identified a 7.6% increase in the number of vulnerabilities tied to ransomware in Q1 2022, with the Conti ransomware group exploiting most of those vulnerabilities. The report uncovered 22 new vulnerabilities tied to ransomware (bringing the total to 310). 19 of those vulnerabilities are connected to Conti, a prolific ransomware group that pledged support for the Russian government following the invasion of Ukraine.

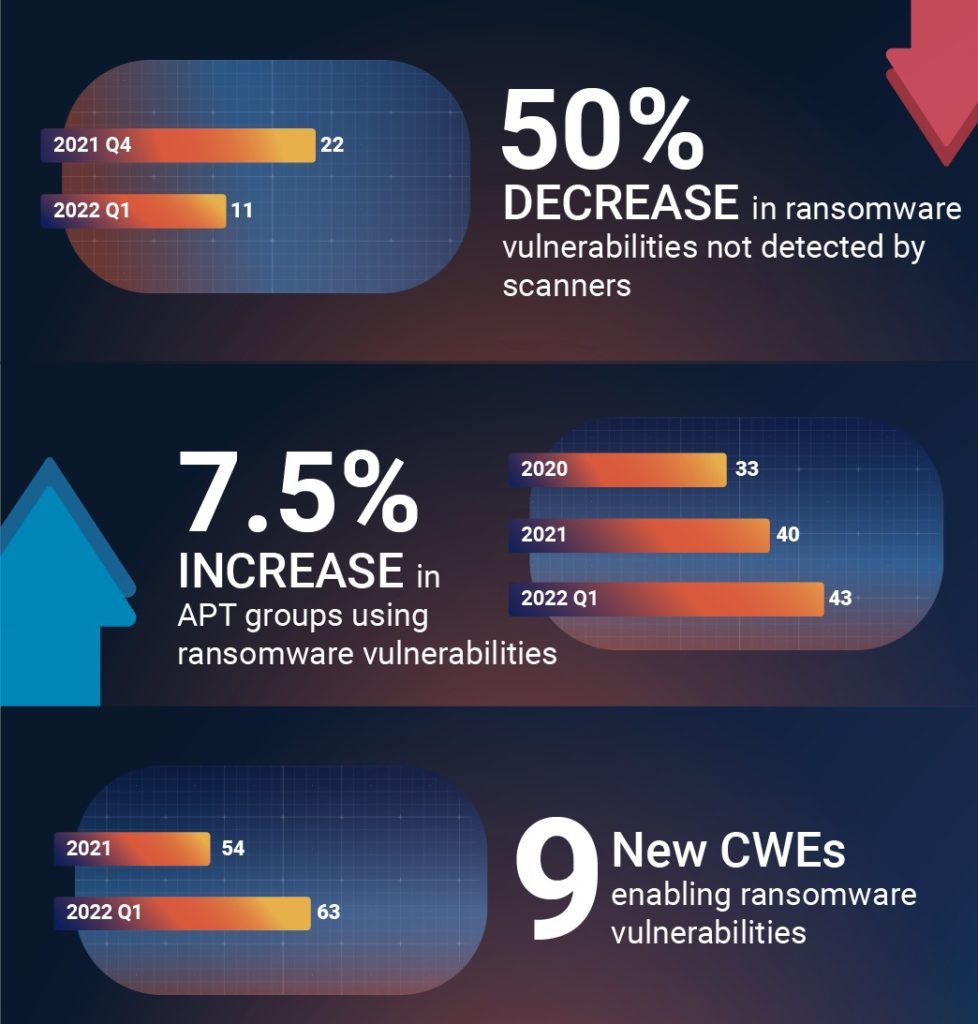
The report also revealed a 7.5% increase in APT groups associated with ransomware, a 6.8% increase in actively exploited and trending vulnerabilities and a 2.5% increase in ransomware families.
Analysis revealed that three new Advanced Persistent Threat (APT) groups (Exotic Lily, APT 35, DEV-0401) started using ransomware to attack their targets, 10 new active and trending vulnerabilities became associated with ransomware (bringing the total to 157) and four new ransomware families (AvosLocker, Karma, BlackCat, Night Sky) became active in Q1 2022.
Faster weaponization of vulnerabilities
Additionally, the report revealed that ransomware operators continued to weaponize vulnerabilities faster than ever before and target those that create maximum disruption and impact. This increased sophistication by ransomware groups has resulted in vulnerabilities being exploited within eight days of patches being released by vendors.
It also means that any minor laxity in security measures by third-party vendors and organisations is sufficient for ransomware groups to enter and infiltrate vulnerable networks. To make matters worse, some of the most popular scanners are not detecting several key ransomware vulnerabilities.
The research revealed that over 3.5% of ransomware vulnerabilities are being missed, exposing organisations to grave risks.

Aaron Sandeen, CEO of Cyber Security Works, said, “The fact that scanners are not detecting critical ransomware vulnerabilities is a huge problem for organisations. The good news is that in this quarter, we saw the number coming down."
This means that scanner companies are taking this seriously. That said, there are still 11 ransomware vulnerabilities that the scanners are not detecting where five are rated critical and associated with notorious ransomware gangs like Ryuk, Petya and Locky.
Further handicapping security and IT teams are gaps that exist within the National Vulnerability Database (NVD), the Common Attack Pattern Enumeration and Classification (CAPEC) list by The MITRE Corporation and the Known Exploited Vulnerabilities (KEVs) catalogue by the US Cybersecurity and Infrastructure Security Agency (CISA).
The report revealed that the NVD is missing Common Weakness Enumerations (CWEs) for 61 vulnerabilities, while the CAPEC list is missing CWEs for 87 vulnerabilities. On average, a ransomware vulnerability is added to the NVD a week after being disclosed by a vendor. 169 vulnerabilities with ransomware associations have yet to be added to the CISA KEV list. Meanwhile, hackers worldwide are actively targeting 100 of these vulnerabilities, scouting organisations for one unpatched instance to exploit.

Srinivas Mukkamala, senior vice president & general manager of security products at Ivanti, cautioned that threat actors are increasingly targeting flaws in cyber hygiene, including legacy vulnerability management processes.
He noted that many security and IT teams struggle to identify the real-world risks that vulnerabilities pose and therefore improperly prioritise vulnerabilities for remediation.
For example, many only patch new vulnerabilities or those that have been disclosed in the NVD. Others only use the Common Vulnerability Scoring System (CVSS) to score and prioritise vulnerabilities.
"To better protect organisations against cyberattacks, security and IT teams need to adopt a risk-based approach to vulnerability management. This requires AI-based technology that can identify enterprise exposures and active threats, provide early warnings of vulnerability weaponization, predict attacks and prioritise remediation activities," he elaborated.
Threat to healthcare systems
The report also analysed 56 vendors that supply healthcare applications, medical devices and hardware used in hospitals and healthcare centres and uncovered 624 unique vulnerabilities in their products.
Forty of those vulnerabilities have public exploits and two vulnerabilities (CVE-2020-0601 and CVE-2021-34527) are associated with four ransomware operators (BigBossHorse, Cerber, Conti and Vice Society).
Unfortunately, this could indicate that the healthcare industry may be targeted more aggressively by ransomware attacks in the coming months.

Cyware co-founder and CEO, Anuj Goel warns that ransomware is now one of the most predominant attack vectors affecting the bottom line of organisations globally.
He added that the Q1 report underscores the fact with new numbers that show an increase in the number of ransomware vulnerabilities and the APTs using ransomware. However, one of the major concerns that have surfaced is the lack of complete threat visibility for security teams owing to cluttered threat intelligence available across sources.
"If security teams must mitigate ransomware attacks proactively, they must tie their patch and vulnerability response to a centralised threat intelligence management workflow that drives complete visibility into the shape-shifting ransomware attack vectors through multi-source intelligence ingestion, correlation and security actioning," he concluded.




