Some years back I was visiting a CIO and as I passed the corridors of her office, I saw one screen with a post-it note sticking on the monitor and what looked like a password. The CIO commented that they were looking at ways to encourage staff not to write their passwords on post-it notes.
The annual World Password Day is held on the first Thursday of May. This year, 2021 – the 9th annual, we are asked to remember our passwords on May 6. Why do we need to be reminded about this?
Because passwords are the keys that unlock stores of digital and physical assets. And if we are not careful, we could lose some, if not all, things of value to us, either as employees or as individuals.
How many passwords
A 2020 NordPass study estimated that the average person has about 70-80 passwords – that’s a lot of information to remember. But as NordPass revealed, people do not take passwords seriously despite repeatedly being told of the importance to do so.
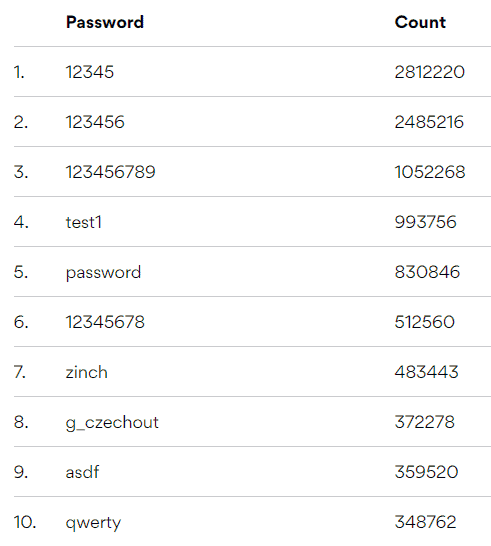
No wonder data breaches are easy, and the records of user accounts being leaked on the Internet has been steadily climbing.
The shift to remote last year has opened a new can of worms for CISOs and CIOs tasked with protecting company systems and data.

Jeffrey Kok, VP solution engineers APJ for CyberArk, says “every new corporate application or tool becomes a new identity silo, with unique password management requirements, such as complexity or how often they should be rotated.”
He pointed to a CyberArk surveyed which revealed that people tend to use and re-use weak passwords. What is lamentable is that despite this, passwords are still often the only verification method in use – despite the availability of new technologies.
Any other way to create passwords? Yes, there are. Innovations in smart computing have allowed for the proliferation of password creation and authentication systems that range from simple PIN to biometrics – fingerprint, palm, eye, face and voice – to apps that create and store passwords.
Editor's pick: PodChats for FutureCIO: Evolving identity authentication technology

Banks and credit card companies typically will use one-time-email passcodes sent via email or SMS. Unfortunately, both have been proven to be easily hackable. There are also security keys like Yubico and security authenticators like Google Authenticator.

According to Johan Fantenberg, principal sales engineer, ForgeRock, Asians conduct a lot of their business online interactions on the go — this has resulted in a largely mobile-first environment.
“As a result, for convenience and security, we see a greater use of mobile device capabilities, such as biometric sensors in the form of facial recognition and fingerprint scanning. Commercially, digital banks are making great use of these capabilities for customer on-boarding and subsequent authentication and authorization,” he continued.
Fantenberg believes that passwordless tech is ready to take on the job of authentication.
“For instance, with the industry accepted FIDO2 WebAuthn, users are able to leverage common devices to easily authenticate to online services in both mobile and desktop environments – without a traditional password login,” he continued.
Tips to reduce risk
CyberArk’s Kok offers four tips for reducing password-related risks:
Mandate the use of a strong password. Passwords should contain at least 10 characters and include a combination of character types, such as commas, percent signs and parentheses, as well as uppercase and lowercase letters and numbers.
Enforce the use of one unique password for each service and account. If employees re-use passwords on multiple sites or accounts, even if the password is complex enough and long, all it will take is for one of their accounts to be compromised to make all of their other accounts vulnerable.
Use multi-factor authentication. This means that multiple types of authentication – not just a password – are required to unlock the account. The first part of the authentication process requires something the user already knows, like a password.
The other part of the authentication process involves something the user doesn’t already know, such as a code sent to the mobile phone by authentication software or created by a designated application on the phone.
This code becomes the other half of a user’s login authentication. Now, even if attackers manage to get a password, they still don’t have access to the account without the other part of the authentication.
Address the risk of local admin accounts on workstations. Weak passwords and end users with local admin rights on their workstations represent a significant security risk for organisations. Many attacks start on endpoints where attackers initially gain access through a phishing attack or when an employee inadvertently downloads and executes a malicious application. In many cases, an attacker’s aim is to compromise the privileged credentials that reside on workstations.
He also advocates organisations rotate local admin credentials (including the OS build in local account) on a periodic basis as an important security measure. Consider removing local admin rights from end user workstations altogether to further reduce the risk of attacks from the endpoint.




