Are businesses getting better at detection breaches and intrusions? In a 2019 global survey published by Statista, IT security decision-makers listed malwares, phishing and ransomware as their three most dreaded security threats. But the variances against most other threats are not significant suggesting that threats are given nearly the same weight and concern irrespective of the type. A cyber threat is a threat no matter what form it comes in.
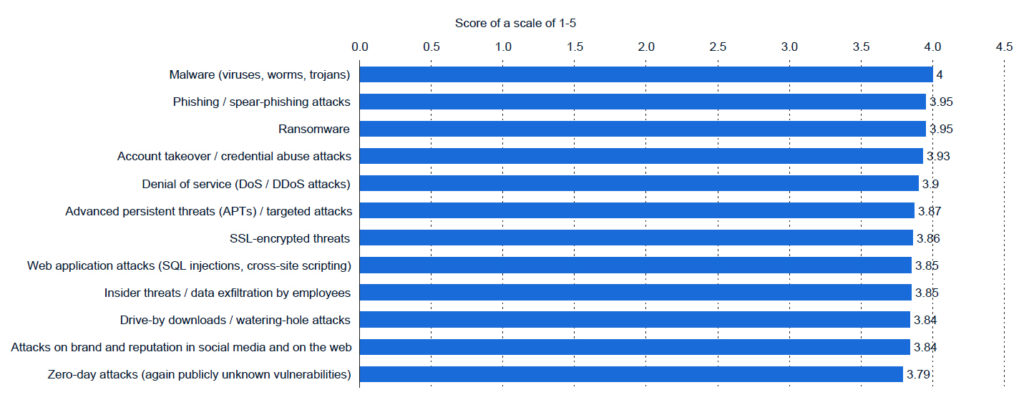
Source: CyberEdge, Statista
The FireEye Mandiant M-Trends 2021 report has observed a trending reduction in global median dwell time (defined as the duration between the start of a cyber intrusion and when it is identified).
This measure went from over one year in 2011 to just 24 days in 2020 – that’s more than twice as quickly identified in comparison to last year’s report with a median dwell time of 56 days.
Mandiant attributes this reduction to continued development and improvement of organisational detection and response capabilities, along with the surge of multifaceted extortion and ransomware intrusions.

According to Steven Stone, senior director, advanced practices, FireEye Mandiant, the combined improvements in detections from internal teams and the continued reduction in median global dwell times indicate improvements on the organization side.
“While some of these trends are likely due to ransomware, these progress areas are also highly likely due to maturing clients, continued innovations across the cyber security industry, and government/partnership efforts,” he added.

Jurgen Kutscher, executive vice president, service delivery at Mandiant, acknowledged that organisations continue to improve their ability to discover compromises within their environments, containing adversaries today comes with unique challenges.
Mandiant experts observed a return of organisations independently detecting most of their own incidents. Internal incident detection rose to 59% in 2020 – a 12-point increase compared to 2019. This return to organisations detecting the majority of intrusions within their environments is in line with the overall trend observed over the last five years.
“The consequences of a global pandemic forced companies to rethink how they operate and move to a remote workforce. This change resulted in VPN infrastructure, video conferencing, collaboration and knowledge sharing platforms becoming business-critical systems and changing the attack surface of organisations. In many cases, regular employees became responsible for connectivity and cybersecurity,” he continued.
Is Mandiant suggesting that employees are more aware of the cyber threat?
Most popular targets
The top five most targeted industries are Business and Professional Services, Retail and Hospitality, Financial, Healthcare and High Technology.
Mandiant experts observed that organisations in the Retail and Hospitality industry were targeted more heavily in 2020 – coming in as the second most targeted industry compared to 11th in last year’s report.
Healthcare also rose significantly, becoming the third most targeted industry in 2020, compared to eighth in last year’s report. This increased focus by threat actors can most likely be explained by the vital role the healthcare sector played during the global pandemic.
According to Kutscher, the sudden boost in business services necessary for remote working has made this industry the most targeted in 2020 by cybercriminals and state-sponsored threat actors.
Motivation
Mandiant harps the same observation that other security reports claim – that the primary motivation for many of the attacks remain financial gain (at least for 36% of the intrusions the company has investigated), with multifaceted extortion and ransomware are the preferred weapon of choice.

“Data theft and reselling of unauthorized access to victim organisations remain high as multifaceted extortion and ransomware actors have trended away from purely opportunistic campaigns in favour of targeting organisations that are more likely to pay large extortion demands. Given this surge, organisations must take proactive action to mitigate the potential impact,” said Charles Carmakal, senior vice president and chief technology officer, Mandiant.
Wolf in sheep’s clothing
Carmakal warned that threat groups and cyber criminals rely on publicly available tools introduced in different stages of a compromise. The usage of public or commercially available tools, often used by red teams and penetration testers, allows the threat actor to blend in with security testing. It also makes attribution more complex.
He cited the example of the commercial tool BEACON, part of the Cobalt Strike software platform, commonly used for penetration testing (pentesting) of network environments. BEACON is being used by groups like APT19, APT32, APT40, APT41, FIN6, FIN7, FIN9 and FIN11, as well as nearly 300 uncategorised clusters of threat activity.
Lessons learned

Citing what is arguably one of the most high-profile cyberattacks of 2020 – UNC2452, the threat actor responsible for the SolarWinds supply chain attack – Mandiant’s executive vice president, global threat intelligence, Sandra Joyce, warned that a highly disciplined and patient actor cannot be underestimated.
“This actor’s attention paid to operational security, counter forensics, and even counterintelligence set it apart from its peers. Defence against this actor will not be easy, but it is not impossible. We believe that intelligence will be our advantage in future encounters,” harped Joyce.
Kutscher concurred adding that the increase in exploit usage should remind organisations to have a more robust plan for patching product vulnerabilities. He noted that one of the challenges is identifying what sources and information are available to make better risk-based decisions when prioritising what systems and applications to patch now and what to patch at a later stage based on current knowledge about exploitation and targeting by threat actors.
Thomas Richards, principal security consultant at Synopsys Software Integrity Group added that focusing solely on detecting what tools are in use is a short-sighted strategy.
“Companies who contract security testing, or do their own security testing, should require their vendors to disclose the source IP addresses of their testing traffic. With that information, the company’s security operations team is then able to differentiate between legitimate testing traffic and other potentially malicious traffic,” he concluded.
So, are users getting better at identifying cyberattacks like phishing? In my view, maybe a smidgen. People are concerned with many things and it is these concerns that can distract them from given attention to what they are doing at any moment in time. That is the moment that cybercriminals are banking on - when we do something automatic like opening an email or clicking on a link because we were too distracted about something else.
Unfortunately securing the known weakest link in the enterprise appears to be the last priority in IT enterprises' cybersecurity strategy. Otherwise, adaptive access control wouldn't be so low in the totem point of investment priorities as per Statista chart below.
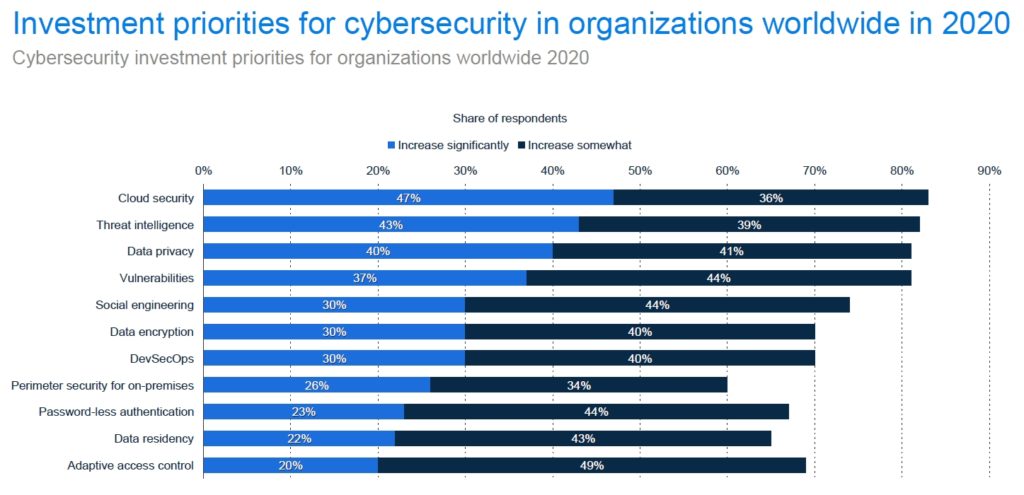
Source: Investment priorities for cybersecurity in organizations worldwide in 2020, Statista




