The Consortium for Information and Software Quality (or CISQ) estimates that poor software quality costs US companies upwards of $2.08 trillion annually. These losses include costs from operational failures, unsuccessful projects, and software errors in legacy systems.
A software bug is an error, flaw or fault in the design, development or operation of software that causes it to behave in unintended ways. CISQ estimates that the process for identifying and correcting bugs, called debugging, accounts for a significant percentage of a software project’s cost – more than the creation of the software in the first place.
Finding software bugs is a full-time job and can detract the IT team from focusing on focusing on more strategic priorities – although to be clear, repairing errors in software is just as important, especially those about security exploits and vulnerabilities.
Debugging engineers typically are proficient in one or more programming languages and are familiar with common frameworks, libraries, and platforms, such as Selenium, JUnit, TestNG, or Cucumber.
The scarcity of such talent coupled with the accelerated pace at which new applications are being designed, tested and moved to production, has created an economic opportunity for bug bounty.
Dave Gerry, CEO at Bugcrowd, defines a bug bounty program as a cybersecurity initiative that organisations implement to incentivize security researchers and ethical hackers to find and report vulnerabilities or security flaws in their software, websites, or digital systems.
“These programs are designed to help identify and fix security issues before malicious hackers can exploit them for malicious purposes,” he continued.
Importance of bug bounty
A bug bounty typically involves research and testing, reporting, verification, fixing and patching and acknowledgement.
Gerry claims bug bounty programs have become a popular approach for organisations to bolster their cybersecurity efforts. “They benefit from the expertise of the global security community, which can often identify vulnerabilities that internal teams might have missed. For ethical hackers and security researchers, bug bounties provide an opportunity to earn money while contributing to the security of digital systems,” he elaborated.
These programs have been adopted by tech companies, government agencies, financial institutions, and a wide range of organisations with an online presence to improve their security posture.
Bug bounty oversight
Just as with any program, delivered internally or through an outsourced expert, some supervision or guidelines need to be set in place. Otherwise, the organisation risks the program running in tangent or not delivering on the original reasons for which it was created.
Asked who should oversee such operations, Gerry noted that typically, the security organisation is responsible for deploying a bug bounty program and coordinating the necessary budgets.
“From there, it becomes an organisation-wide initiative as most functions will contribute to the remediation efforts, promotion, and overall success of the program,” he added.
He also pointed out that anything that an organisation produces, including applications, hardware, infrastructure, networks, APIs, LLM, etc, is a good candidate to be a part of a bug bounty program.
“While security does typically own the management and budgeting of a bug bounty program, the entire organisation plays a critical role in its long-term success,” he continued.
In-source or outsource
According to Gerry organisations of all sizes and maturity levels can benefit from a bug bounty program. "While some large (F100) companies may have in-house staff to deal with the management of the program, they often come to providers for assistance in the triaging of vulnerabilities or the payment processing of bounty payments to the hacker community," he added.
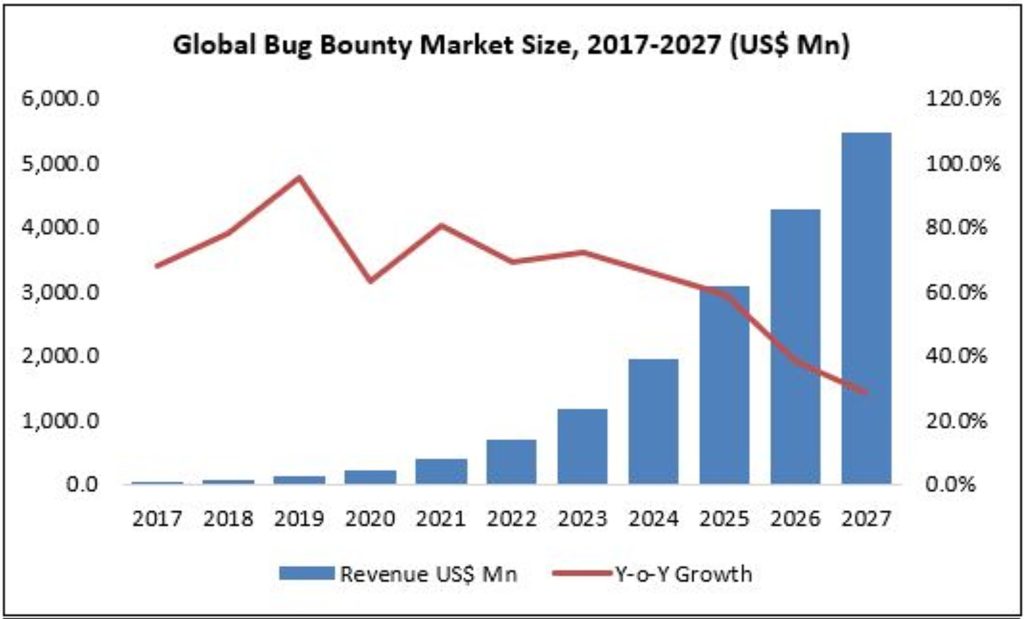
The 2023 Bug Bounty Platforms Report estimates the bug bounty platforms market at US$973.1 million in 2021 steadily rising at a CAGR of 15.94% during the forecast period reaching US$2.36 billion by 2027.
Guidelines for bug bounty programs
Asked what guidelines and rules should be part of any bug bounty program or strategy, Gerry points out that before the launch of any bug bounty program, it is important to document the scope of the engagement, areas of the organisation’s asset(s) that may be out of scope, the pay scale for vulnerabilities by criticality, and the process in which the organisation will evaluation the vulnerabilities that are identified.
“This is typically provided to the hacker community via a Program Brief on the organisation’s website or by the bug bounty provider,” he added.
The growing influence of AI
In the Inside the Mind of the Hacker Report, Bugcrowd founder CTO, Casey Ellis, believes that cybersecurity is about to become less predictable – commenting on the topic of AI and the impact of generative AI on security.
Acknowledging that artificial intelligence (AI) is a ‘hot button’ in security, Gerry points out that AI has the potential to make security teams wildly more productive, and, at the same time, has the potential to make bad actors more productive in their criminal activities.
The report cited that 91% of hackers believe that AI will help amplify the work that they do, with 78% believing it will disrupt the way they conduct penetration testing or work on bug bounty programs.
Generative AI technology types used by Hackers

However, 72% believe that AI cannot replace the human creativity that they bring to hacking. Interestingly, 94% of hackers plan to start using AI in the future to help them ethically hack while 91% believe that AI technologies are upping the value of ethical hacking.
Bug Bounty in 2024 and beyond

“We expect to see continued growth around new programs launching - both in organisations using bug bounties today and for those not yet using bug bounty. As these programs continue to launch, more and more individuals will become hackers on the various platforms as they see the income opportunity in bug bounties.”
Dave Gerry
“Security has never been more critical to an organisation’s long-term success than it is today - the legacy tools, scanners, and methods have failed and organisations must look to the hacker community for help as we all aim to disrupt the adversaries we face daily,” concluded Gerry.




