The Entrust 2021 Hong Kong Encryption Trends Study, part of the 16th annual multinational survey by the Ponemon Institute, noted that security and IT professionals in Hong Kong continue to outpace the global average when it comes to the adoption of enterprise-wide encryption, with particular focus on cloud services and applications, as well as containers.
Michael Tai, area vice president, Greater China, Entrust noted that organizations in Hong Kong are increasing their use of the cloud and containers as IT and security professionals focus on the risks associated with employee mistakes and system or process malfunctions.
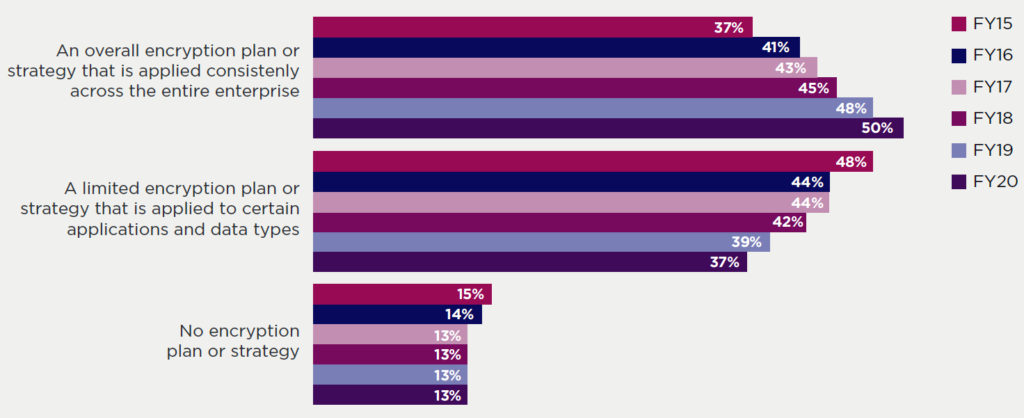
Figure 1: Does your company have an encryption strategy? (country samples are consolidated)
He opined that as they strive to protect customer information and intellectual property and to comply with data privacy mandates, organizations on average now use more than eight different products that perform encryption.
“This brings new challenges associated with discovering where sensitive data resides, deploying encryption technology and training users to use encryption appropriately,” he added.
Identified threats and priorities
Specifically, 54% of respondents in Hong Kong now have a consistently applied encryption plan/strategy, well ahead of the global average (50%) for the second year running.
For the second straight year in Hong Kong, the biggest threats that might result in the exposure of sensitive data were employee mistakes (47% vs. 53% globally) and system or process malfunction, which increased from 30% to 36% (vs. 31% globally).
Currently, around six-in-ten (59%) organizations surveyed in Hong Kong transfer data to the cloud. This is up from 55% last year but is expected to surge with an additional 24% planning to do so in the next 12-24 months.
Just over half of organizations surveyed deploy encryption for public cloud services (51% vs. 46% globally) and Bring Your Own Key (BYOK) management support was cited as the fastest growing feature of cloud encryption solutions by 53%, up from 48% last year.
Around 47% of responding IT professionals in Hong Kong deploy encryption for containers, the highest rate worldwide, up from 40% last year and far above the global average of 32%.
The growing role of hardware security modules (HSMs)
Figure 2: Trends in encryption strategy (country samples are consolidated)
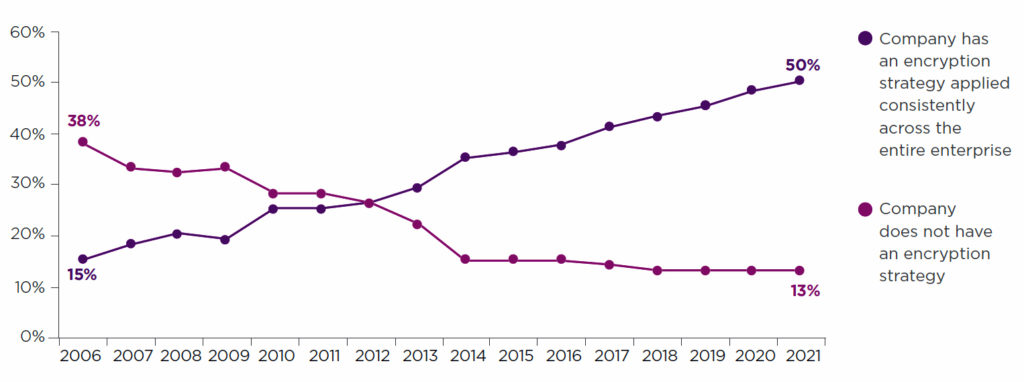
For Hong Kong IT professionals, the pain associated with key management is increasing, with two-thirds reporting a high rate of overall pain associated with managing keys or certificates. This is up from 61% last year and higher than this year’s global average of 56%.
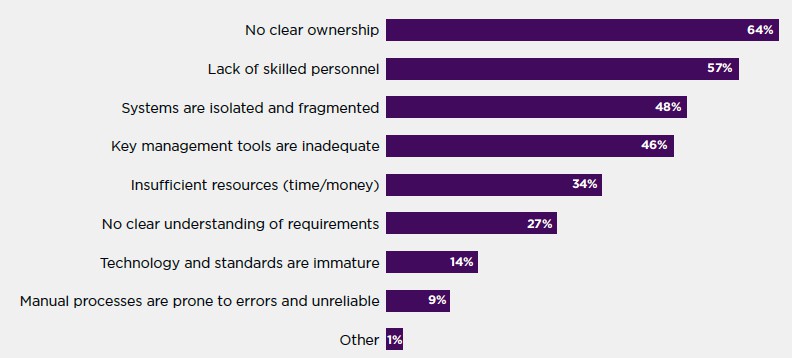
The top factor driving this is “no clear ownership” (74% vs. 64% globally), with inadequate key management tools in second place (58% vs. 46% globally).
Another factor to consider is the lower rates of hardware security module (HSM) adoption, with 40% of respondent organizations in Hong Kong using HSMs (vs. 49% globally).
The fact that this is up from 34% last year, making it the 2nd highest increase worldwide, suggests that the benefits of HSMs – including the ability to help with key management - are being recognized in the region.
Hong Kong results indicate that the importance of HSMs to encryption or key management strategy is expected to increase from 63% to 79% over the next 12 months.
With the increased focus on cloud migration, when using HSMs to protect cloud applications a higher percentage of responding organizations in Hong Kong than any other region prefer to use HSMs they own and operate (54% vs 41% globally).
Over the next 12 months, respondent organizations anticipate greater use of HSMs for several use cases, led by TLS/SSL going from 38% to 78% year over year, the largest expected increase of any use case.
Other leading use cases include database encryption (increasing from 25% to 45%), blockchain applications (from 13% to 30%) and payment transaction processing or payment credential issuing/provisioning (expected to increase from 26% to 40%).
Figure 3: Key management challenges (country samples are consolidated. Three responses permitted)
Entrust’s Tai is concerned that key management still causes a high level of pain, due primarily to concerns about key ownership and inadequate key management tools.
“As they deploy encryption for databases, containers and cloud applications, organizations in the region seek encryption solutions that offer scalability, tamper resistance with an HSM, but as cloud use increases, organizations prefer to own and manage the HSMs used to protect cloud applications,” he concluded.




