At a recent FutureCISO Breakfast briefing, on the topic of “Looming cyberthreats in 2022 – Tipping the scale in your favour”, one of the areas covered was the different types of attacks used to get the target to click on a link.
During the panel discussion, it was acknowledged that cybercriminals are employing as many tactics as they can to get the intended target to fall prey to the attack. Given that targets are becoming more aware of what fake content, in the form of social postings, email messages and websites and what these look like, criminal elements are decidedly combining the previous attack approaches in the hope of landing that next victim.
One old attack scheme that has seen an uptick in 2021 is Telephone-oriented attack delivery or TOAD. According to the Proofpoint 2022 State of the Phish report, multi-faceted TOAD efforts use a variety of tools such as fraudulent emails, call centres, well-designed websites and mobile apps, remote access software, and malware that includes downloaders linked to later-stage ransomware delivery.
In explaining the uptick in 2021, Adrian Covich, senior director of systems engineering for Asia-Pacific and Japan at Proofpoint observes that the pandemic has shifted company operation to largely email, messaging and voice.
"The more frequent use of voice communication has become an effective way for the attacker to gain trust," he opined. He also noted the use by attackers of a malware family BazaLoader and BazaCall, a phishing campaign that tells people to dial a phone number to cancel a phoney subscription, for example. At the other end is an attacker posing as customer support that guides victims to download a malicious payload commonly used in ransomware attacks.
"If an attacker is trying to convince you to change a payment destination, typically that's not something that's done over the phone, but with the right level of bravado and confidence – an attacker may be able to convince you to do that," he elaborated.
According to Covich attackers have worked out that the phone is a great thing to use to deliver malware and be able to con people out of money.
Why attacks are successful

Covich conceded when organisations shifted to the cloud and remote work, attackers were quick at pivoting on opportunities.
"They knew that people reuse usernames and passwords for different services, so compromising one may give you access to others. They also know that people do not necessarily know colleagues by face, so TOAD attacks have increased to take advantage of this anonymity," he added.
He further commented that TOAD attacks against businesses are successful because business processes are either not there or not properly followed.
"Having businesses and organisations really adhere to not only having those processes for those important financial transactions in place but also well-communicated and well-trained – and that's an essential part as well – is going to be key to be able to deal with that," he continued.
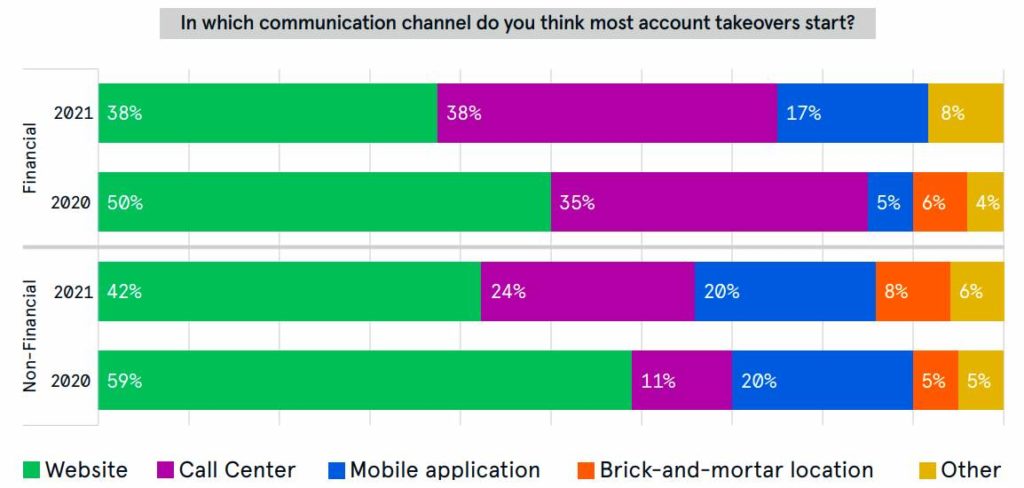
The 2021 State of the Call Center Authentication report by Neustar revealed that websites and call centres are the two main starting points for account takeovers.
Getting better at handling threats
He suggested that emails need to be scanned for incoming messages that are used in conjunction with telephone scams. He raised the importance of having robust controls like web filtering.
"Awareness and training on those processes become important. Because we all have phones, we cannot stop phone calls. So, the first tule is if something seems too good to be true, it probably is. This should be your number one guide," he suggested.
Asked whether there are tools currently able to identify TOAD attacks, particularly for enterprises with security teams, technology, and processes in place?
Covich pointed out that Proofpoint's mantra: it's all about people.
"Successful threat protection requires people-centric defence in depth. Your users must be a key part of the security stack. The more informed and equipped they are, the more resilient your organisation will be." Proofpoint 2022 State of the Phish
Recognising what attack types are popular and where they are coming from will be important in containing the threats, said Covich. He also suggests that IT and security look at how well security strategies are integrated into the organisation's overall operation – how well controls are aligned with the business.
"Finally, are you investing in making sure that you're going to be able to adjust to the next threat? What is the level of understanding you have of a threat landscape? Are you investing in research and development so that you can then apply the latest intelligence to protect your organisation?" called out Covich.
Click on the PodChat player and hear Covich elaborate on best practices for managing TOAD attacks.
- What is a telephone-oriented attack delivery, or TOAD?
- How dangerous can TOADs be? Could you give some examples of how TOADs can impact consumers and businesses?
- Though call centre threats are not new, they are evolving to become part of a robust and complex attack chain. Could you elaborate more on this?
- How do you protect against these TOADS – viewed from the perspective of the enterprise and the consumer?
- What are the top challenges that companies like Proofpoint face when it comes to battling TOADs and other phishing attacks?
- What are some strategies that can be put into place?