According to Gartner, among the top strategic technology trends for 2022 is cybersecurity mesh, just behind the data fabric. The researcher defines cybersecurity mesh as a distributed architectural approach to scalable, flexible and reliable cybersecurity control. Many assets now exist outside of the traditional security perimeter.

Vivien Pua, industry analyst covering security with Frost & Sullivan, adds that cybersecurity mesh offers better protection in distributed environments, by redefining the security perimeter around the identity of a person or machine on the network instead of a single security perimeter approach.
“Organisations can strengthen their security posture by interconnecting the security tools via a standardised and integrated security approach, at the same time, fully optimise their existing or even future cybersecurity investment,” she adds.
What problems does it solve?
From a security standpoint, the acceleration of digitalisation and the increasing adoption of new technologies have expanded organisations’ network perimeter as well as the potential attack surface.
Pua points out that the business environment is becoming increasingly distributed with the fragmented perimeter as the users are connecting to the network from anywhere and the assets are being placed in multiple locations including on-premises and cloud environments.
The result is the proliferation of siloed security solutions that serve purposes, calls out Pua.

Then along comes the pandemic which resulted in mass restrictions around mobility giving rise to remote working. Cherry Fung, regional director serving Fortinet’s Hong Kong, Macau and Mongolia markets says many enterprises are struggling to cope with the long-term need for work-from-anywhere capabilities.
From a security standpoint, “they need a unifying architecture to bring their fragmented infrastructure under control, so adopting new technologies is secure and straightforward,” she adds.
Manikandan Thangaraj, vice president at ManageEngine, cybersecurity mesh provides a modular approach by ensuring that each node has its own perimeter, as opposed to a single wide perimeter. “This facilitates tighter security for each node in the network, allowing IT teams to track access levels and prevent attackers from gaining unauthorised access,” he adds.
However, making sure to cover this expanding universe of connected elements is only one part of the equation. It is also making sense of the data streams flowing to and from these nodes and across the network needed to be done for an effective security posture. And doing this with the limited resources available to the CIO and CISO.
“Replacing manual processes with AI-driven automation to better discover, manage and secure access to essential business resources and data, and ensuring security & compliance while freeing your IT team from manual processes,” adds Chern-Yue Boey, senior vice president, Asia-Pacific at SailPoint.
Cybersecurity mesh – under the hood
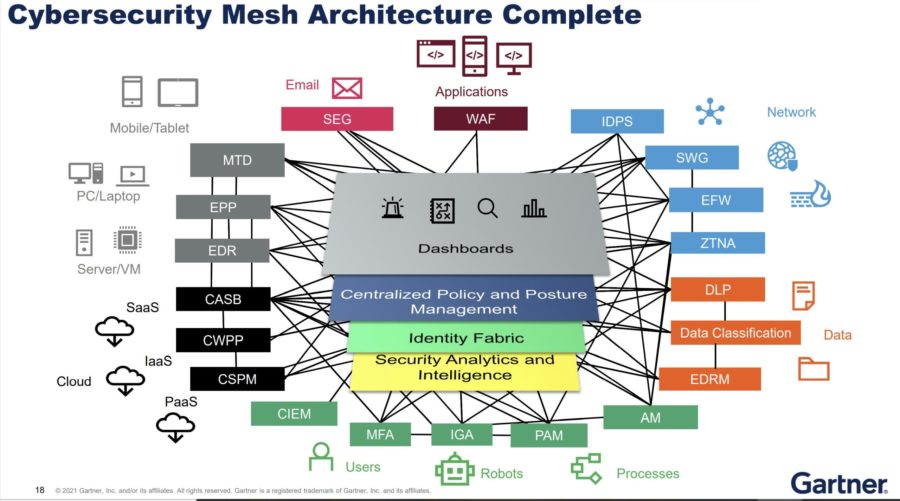
Different experts view cybersecurity mesh architecture (CSMA) differently. Frost's Pua opines that CSMA is not a solution but a strategy that promotes a collaborative approach for standardised and centralised security controls under the foundation of a distributed architectural approach.
“Key components of this concept include a distributed identity approach that defines the cybersecurity perimeter around the identity of a person or machines on the network, a consolidated management and centralised visibility of the existing security tools, and a collaborative approach to security data and intelligence sharing between the security tools,” she continues.
Thangaraj concurs adding that organisations deploying a CSMA, require solutions that can operate together to ensure visibility across all nodes and facilitate centralised management.
“These integrated solutions should also use a shared threat intelligence database to ensure that they all detect and respond to the same threats and alerts. The different solutions required to implement a CSMA approach include insider threat prevention and management, DLP, CASB, IAM, PAM, SIEM, SOAR, and password management solutions,” he lists out.
Fung sums it up by saying a true CSMA platform should break down technology and vendor silos. It will display three attributes: broad visibility to reduce risk and enable coordination, an integrated and unified approach to security, and a context-aware, self-healing network and security posture.
CSMA use cases

Boey notes that as organisations embrace hybrid, multi-cloud environments, they will need secure cloud access to prevent unauthorised access across the infrastructure. Visibility is important to reduce risk, help define (and redefine as conditions evolve) policies and govern efficiently.
“Organisations will need to adopt secure, compliant access for remote workers wherever they are. Your staff needs access to applications and data whether they’re working from home or on the road. But every day, hackers are finding new ways to exploit the security vulnerabilities of remote workers,” he continues.
CSMA guidelines for CISOs and CIOs
Everyone has an opinion here.
Frost’s Pua says the CIO and CISO need to ensure an identity-driven approach is in place to secure the distributed environment as the concept of a network being fully enclosed within a building is gone.
“Secondly, it’s important to consolidate and centralise the management and controls of the existing security tools and not run these tools in silo to avoid gaps or vulnerabilities in the system. Thirdly, a collaborative approach to data analytics and threat intelligence will be the key to addressing the evolving cybersecurity threat landscape.
“All these components need to be done under one single architecture and that’s the key value of how the cybersecurity mesh can help organisations to optimise their existing security investments, at the same time, strengthen their security posture,” she advises.
According to Fung, the mesh solution must support more deployment including physical, virtual, cloud, and X-as-a-Service environments and encompass the industry’s broadest ecosystem and product portfolio, spanning endpoints, networks, and clouds.
“It converges networking and security into a single, integrated system that can expand to any edge and takes a zero-trust approach to verification.
“Within multi-cloud environments, consistent, cloud-native security with auto-scaling is needed. Adaptive Cloud Security allows for effective usage of resources with auto-scaling, dynamic load-balancing, and application user experience visibility,” elaborates Fung.
For his part, SailPoint’s Boey recommends making informed access decisions based on AI.
“With AI-driven recommendations and insights, you can safely decide if access should be approved or revoked, automatically approve low-risk access requests, identify users with access that is outside the norm or is high-risk and prevent audit issues by enabling more accurate access certification decision,” he posits.

Thangaraj from ManageEngine, says to integrate a CSMA with existing information security infrastructure, CIOs and CISOs should keep in mind the following:
- Since cybersecurity mesh is a building block of the Zero Trust approach, begin the implementation of a CSMA with a Zero Trust mindset.
- Audit existing resources and tools and integrate them.
- Shift to cloud-delivered cybersecurity solutions and ensure that the vendors behind those tools support CSMA implementation.
- Choose security tools that are interoperable and extensible.
- Opt for dynamic licensing schemes that allow for scalability and flexibility across any environment.




