BYOPC (Bring Your Own PC) security and SASE (secure access service edge) will have transformational impact on global businesses within the next 10 years. Gartner says BYOPC security will become mainstream in the next 2-5 years whilst SASE will come a little later – 5-10 years.
“Prior to the COVID-19 pandemic, there was little interest in BYOPC,” said
Rob Smith, senior research director at Gartner, said BYOPC did not matter pre-COVID-19. However, at the start of the pandemic, organizations simply had no other alternative.
“The urgent need to enable employees to work from home and a lack of available hardware bolstered its adoption globally. Gartner clients said their adoption of BYOPC is up from less than 5% in 2019,” he commented.
In the 2020 Gartner Hype Cycle for Endpoint Security BYOPC security and SASE reached the Peak of Inflated Expectations. The wide and sudden adoption of BYOPC has become a necessary security strategy which requires CISOs and security leaders to put in place specific security practices.
Figure 1. Hype Cycle for Endpoint Security, 2020
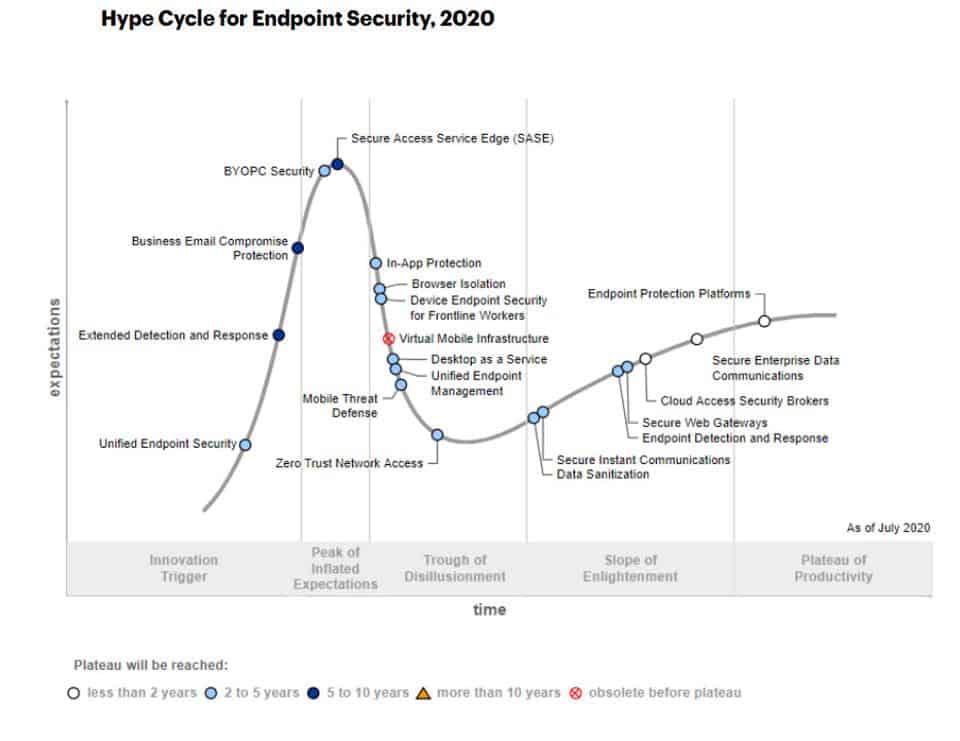
Why CISOs and security heads will care
Smith argued that CISOs and security leaders should expect the need to support BYOPC to be dependent upon a long-term work-from-home strategy, and also expect to support security tools needed for a BYOPC environment
Smith said these executives need to prioritise their security practices, including enabling multifactor authentication (MFA) for all access to any corporate resource regardless if virtual or not, and if cloud or on-premises.
“Organizations must contain all cloud application data and disallow local storage or upload of local data from any BYOPC device as this could infect the cloud system. They also need to virtualize access to any traditional on-premises application,” said Smith.
Malware magnets
As BYOPCs are often infected with malware or ransomware and fall victim to phishing attacks, IT must limit and control access by offsetting the PC hardware investment with critical security technologies such as MFA, cloud access security broker (CASB), zero trust network access (ZTNA), virtual desktop infrastructure, and desktop as a service.
“Without investment in these technologies, IT faces a much higher potential cost in the form of ransomware. It is also critical that IT works with HR, legal, and workers councils to develop a proper work-from-home policy,” added Smith.
SASE to open the floodgates for insecurity
Also, at the peak this year, SASE allows any endpoint to access any application over any network in a protected manner. SASE delivers multiple capabilities such as SD-WAN, secure web gateways, CASB, next-generation firewall and ZTNA.
Editor recommends: Busting 4 common myths surrounding SD-WAN
Joe Skorupa, distinguished research vice president at Gartner, argued that although SASE is relatively new, the COVID-19 pandemic has fostered the need for business continuity plans that include flexible, anywhere, anytime, secure remote access, at scale, even from untrusted devices.
“As SASE services are cloud-native — dynamically scalable, globally accessible, multitenant and including zero trust network access, they are driving its rapid adoption. Over the last three months, SASE has been adopted by more than 40% of global remote workers,” he added.
SASE enables I&O and security teams to deliver a rich set of secure networking and security services in a consistent and integrated manner to support the needs of digital business transformation, edge computing and workforce mobility.
“Mobile workforce, contractor access and edge computing applications that are latency sensitive are three likely opportunities,” concluded Skorupa.




