With over 20 million confirmed coronavirus cases and nearly 800,000 deaths, threat actors have found new prey: the dire call for a COVID-19 vaccine to steam the relentless spread of the contagion.
That was yesterday.
With news coverage about the race to release a vaccine growing every day, it was inevitable that threat actors would capitalise on the misery of others to line their own coffers.
While Russia’s announcement of a COVID-19 vaccine that is ready for mass news is garnering mix comments from everywhere. The idea of when a COVID-19 vaccine will become readily available has drawn the attention of the threat actor community.
Vaccine related campaigns
According to researchers at Check Point Software Technologies, one in 25 malicious coronavirus-related websites’ landing pages is vaccine-related. And that is just between June and July 2020.
In an email alert, Check Point warns of a malspam campaign with the email subject “URGENT INFORMATION LETTER: COVID-19 NEW APPROVED VACCINES”.
These emails contains a malicious .EXE file with the name “Download_Covid 19 New approved vaccines.23.07.2020.exe” that when clicked on, installs an InfoStealer capable of gathering information, such as login information, usernames and passwords from the user’s computer.
Another phishing campaign sends an email with the subject “UK coronavirus vaccine effort is progressing badly appropriate, recruiting consequence and elder adults”.
The mail contains a malicious link “surgicaltoll\.com/vy2g4b\.html” which now seems to be inactive. Our further research revealed that it was used to redirect traffic to a medical phishing website; “thelifestillgoeson[.]su”, which was trying to imitate a legitimate Canadian pharmacy.
Mailboxes – weakest link, really?
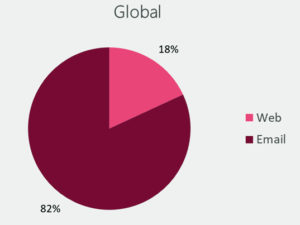
Check Point said that over 80% of attacks against organisations start from a malicious email and called out the email as the weakest link. The condition is exacerbated during COVID-19 as remote working becomes the norm and the security perimeter now extends to a semi-safe edge – the mobile device.
Check Point says closing this security gap requires protections against various threat vectors: phishing, malware, data theft and account-takeover.
This might force you to choose between the security level you need and what you can actually afford and efficiently manage. Email is the first link in a chain of attacks, and with the rise of remote working, the use of cloud mailboxes and productivity applications have been increasing exponentially.
Tips for protection
Recommended reading: Enhancing your email's immune system
The folks at Check Point offered the following tips for mitigating against the risks of falling victim to these cyberattacks:
- Protect your email traffic with at least one layer of an advanced email security solution from a known vendor. Niche players and open-source solutions might cause more damage than good.
- Protect mobile and endpoint browsing with advanced cybersecurity solutions, which prevent browsing to phishing web sites, whether known or unknown
- Use two-factor authentication to verify any change to account information or wire instructions.
- Continuously educate your end-users: whenever irreversible actions such as money transfers are conducted, details of the transaction must be verified in additional means such as voice communication and must not exclusively rely on information from email correspondence.
- Check the full email address on any message and be alert to hyperlinks that may contain misspellings of the actual domain name.
- Do not supply login credentials or personal information in response to a text or email.
- Regularly monitor financial accounts.
- Keep all software and systems up to date.
My take – responsibility is a long rope that is shared by all
Check Point called out email boxes as the weakest link.
I beg to disagree – in some ways. I believe that the email box is just the endpoint, part of the delivery mechanism. But since, in theory, most organisations should have a strategy to securing incoming traffic from malware, shouldn’t the weakest link actually be the people who will click on those email attachments?
Still, I do think that the ecosystem of vendors should share accountability and responsibility – the network operators, including ISPs and those claiming to provide secure connectivity inside their network, for letting bad traffic flow through the system, those sellers of security solutions, standalone or as-a-service to claiming to sell security solutions that hype the protection but claim no responsibility when a breach happens.
I agree that these vendors did not build the content of the email, but if not for them, that email would not have reached the user.
What do you think?
PS: I am not passing the buck here. I am just sharing the blame. This is a community problem that continues to exist. The victims are consumers and enterprises. The winners are threat actors. And, just maybe, those that sell solutions to counter the threat actors are benefiting by tapping on the opportunity? When I was in college, someone referred to this as capitalism!




