Digital transformation (DX) has expanded the availability, velocity, and mission-critical need of data. The COVID-19 pandemic has exacerbated the DX imperative and compounded it with almost unrealistic pressures on time-to-market for projects while keeping the lights on – not just for IT but for the entire organisation.
Despite the attention paid to DX efforts, one area that continues to be a mainstay of interest for leadership and the entire organisation is security.
The Ponemon Institute/ServiceNow study titled, Costs and Consequences of Gaps in Vulnerability Response, revealed that cybersecurity breaches are occurring faster than the ability of cybersecurity teams to respond.
Why enterprise security is failing miserably
While proactive mitigation is the preference, the reality is that the complexity of the IT infrastructure makes it extremely difficult to provide full security cover.
Sixty percent of respondents to the study acknowledged that the breached they experienced was due to an unpatched known vulnerability where the patch was not applied.
The study highlighted a disturbing pattern, there is greater awareness of the importance of timely patching vulnerabilities (44% in 2019 vs 40% in 2018) and yet there is actually a decline (50% in 2019 vs 52% in 2018) in the ability to quickly detect vulnerabilities and preventing threats.
Lame excuse or focusing on the wrong approach?
In 2019, it takes 43 days to detect a cyberattack once a patch is released for a high priority vulnerability, an increase from 36 days in 2018. What happened?
According to 52% of the respondents, 67% of whom are CIOs, head of IT, head of IT security or head of enterprise risk management, said their organisations are at a disadvantage in responding to vulnerabilities because they use manual processes.
Another excuse is ownership of responsibility with 88% of respondents claiming their team is not fully responsible for patching. Coordinating with other teams means an additional 12 days delay in getting the patch done.
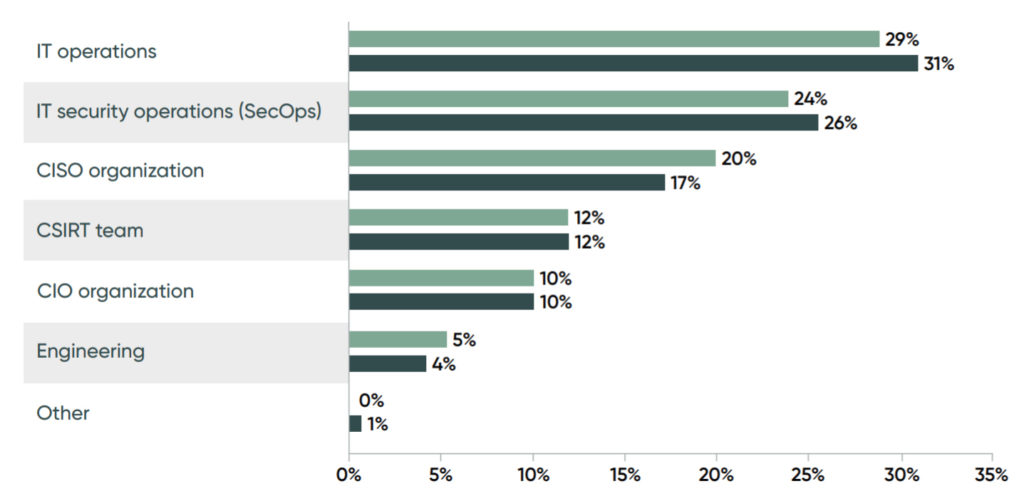
Vulnerability patching is delayed because of a lack of resources, no common view of applications and assets and no ability to take critical applications and systems off-line so they can be patched quickly.
Paradox of the digital era
Gartner forecasts cybersecurity spending to reach US$123 billion in 2020. Who has this kind of money when businesses are trying to contain the bleed from declining revenue and rising cost of keeping remote working processes secure?
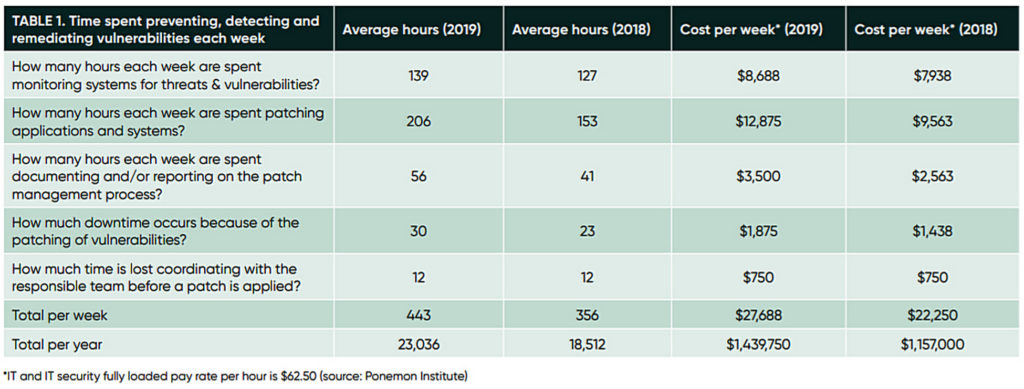
In 2019, organisations spend an average US$1.439 million on vulnerability management, up over 24% from 2018. That is US$282,750 that could either go back to profit or spent on other activities to generate more revenue.
Tony Stark (or Iron Man on his day job) is quoted as saying: “Is it better to be feared or respected? I say, is it too much to ask for both?”
Paraphrasing Tony Stark’s is it better to be feared or respected question: “Do I focus on security (data protection) or revenue?” The rhetoric should be: Is it too much to ask for both?
Understanding the complexity paradox
To be fair to those responsible, managing the security of an organisation has become expansively complex.
There are at least 13 areas that require attention: threat intelligence, incident response platforms, security, automation, security information and event management, artificial intelligence or machine learning, user behaviour analytics, data loss prevention, firewalls, web security, sandbox, manual processes using spreadsheets and paper, endpoint security and email security.
It’s almost like you need a small army to protect the business, its employees, partners and customers. It’s a full-time job! For organisations that see this role as in-house, what is their option?
A better future starts here
With cybercriminals employing artificial intelligence and machine learning to improve their attacks, perhaps it is time for enterprises to do the same. But what is required is more than just adding AI/ML into the game. It is also about improving visibility over the security landscape of the enterprise, followed by a workflow that encourages responsibility.
Where to begin?
Write to us at editors@cxociety.com and share with us your views on how security should be approached to ensure business resilience without sacrificing data privacy and data protection.




