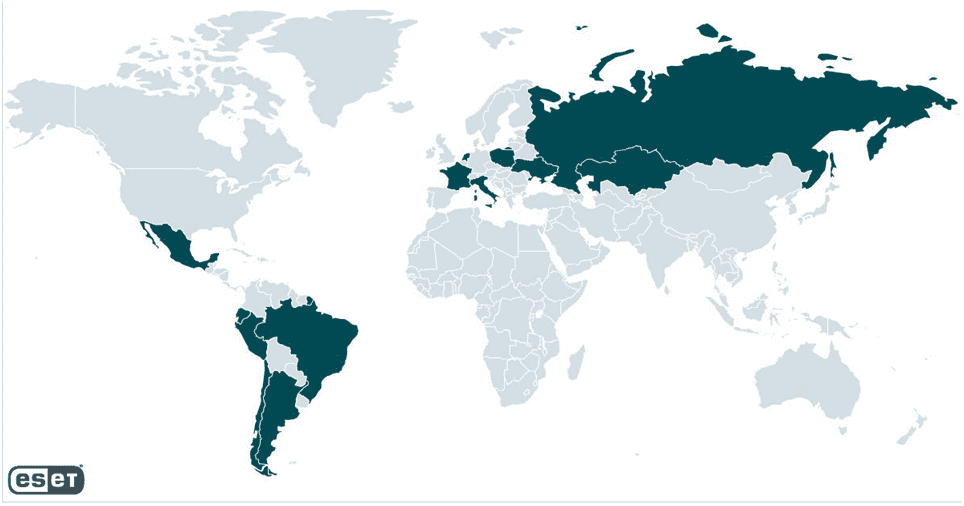
A mass-spreading phishing campaign aimed at collecting Zimbra account users’ credentials was detected by ESET researchers. The ongoing campaign has been active since at least April 2023 and targets a variety of small and medium businesses and governmental entities. There have been victims in Latin America and European countries such as Ukraine, Italy, France, the Netherlands and Poland, where the largest number of targets are located.
ESET researcher Viktor Šperka, who discovered it explains that those who launched the campaign took advantage of HTML attachments that contain legitimate codes, making it much easier to bypass reputable antispam policies, as compared to more prevalent phishing techniques such as directly placing malicious links in the email body.
Launching the attack
The attack starts when a target receives an email with a phishing page in an attached HTML file. The email may contain warnings about email server update, account deactivation or a similar issue, which then directs the victim to click on the attached file. Afterwards, the victim is guided to a fake Zimbra login page.
The submitted credentials are collected from the HTML form and sent to a server controlled by the attacker at the back-end, infiltrating the email account. The attacker can compromise the victim’s administrator accounts and create new mailboxes to send more phishing emails to other targets.
“Target organizations vary; adversaries do not focus on any specific vertical – the only thing connecting victims is that they are using Zimbra,” adds Šperka.





